
Time-division multiple access (TDMA) is a channel access method for shared-medium networks. It allows several users to share the same frequency channel by dividing the signal into different time slots. The users transmit in rapid succession, one after the other, each using its own time slot. This allows multiple stations to share the same transmission medium while using only a part of its channel capacity. Dynamic TDMA is a TDMA variant that dynamically reserves a variable number of time slots in each frame to variable bit-rate data streams, based on the traffic demand of each data stream.
100BaseVG is a 100 Mbit/s Ethernet standard specified to run over four pairs of category 3 cable. It is also called 100VG-AnyLAN because it was defined to carry both Ethernet and Token Ring frame types.
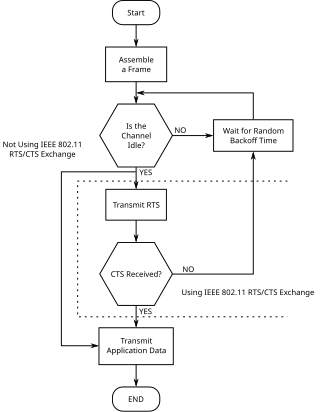
Carrier-sense multiple access with collision avoidance (CSMA/CA) in computer networking, is a network multiple access method in which carrier sensing is used, but nodes attempt to avoid collisions by beginning transmission only after the channel is sensed to be "idle". When they do transmit, nodes transmit their packet data in its entirety.
Carrier-sense multiple access with collision detection (CSMA/CD) is a medium access control (MAC) method used most notably in early Ethernet technology for local area networking. It uses carrier-sensing to defer transmissions until no other stations are transmitting. This is used in combination with collision detection in which a transmitting station detects collisions by sensing transmissions from other stations while it is transmitting a frame. When this collision condition is detected, the station stops transmitting that frame, transmits a jam signal, and then waits for a random time interval before trying to resend the frame.
Carrier-sense multiple access (CSMA) is a medium access control (MAC) protocol in which a node verifies the absence of other traffic before transmitting on a shared transmission medium, such as an electrical bus or a band of the electromagnetic spectrum.
In telecommunications and computer networks, a channel access method or multiple access method allows more than two terminals connected to the same transmission medium to transmit over it and to share its capacity. Examples of shared physical media are wireless networks, bus networks, ring networks and point-to-point links operating in half-duplex mode.
ALOHAnet, also known as the ALOHA System, or simply ALOHA, was a pioneering computer networking system developed at the University of Hawaii.
The data link layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers data between nodes on a network segment across the physical layer. The data link layer provides the functional and procedural means to transfer data between network entities and may also provide the means to detect and possibly correct errors that can occur in the physical layer.
A collision domain is a network segment connected by a shared medium or through repeaters where simultaneous data transmissions collide with one another. The collision domain applies particularly in wireless networks, but also affected early versions of Ethernet. A network collision occurs when more than one device attempts to send a packet on a network segment at the same time. Members of a collision domain may be involved in collisions with one another. Devices outside the collision domain do not have collisions with those inside.
In IEEE 802 LAN/MAN standards, the medium access control sublayer is the layer that controls the hardware responsible for interaction with the wired, optical or wireless transmission medium. The MAC sublayer and the logical link control (LLC) sublayer together make up the data link layer. The LLC provides flow control and multiplexing for the logical link, while the MAC provides flow control and multiplexing for the transmission medium.
Distributed coordination function (DCF) is the fundamental medium access control (MAC) technique of the IEEE 802.11-based WLAN standard. DCF employs a carrier-sense multiple access with collision avoidance (CSMA/CA) with the binary exponential backoff algorithm.
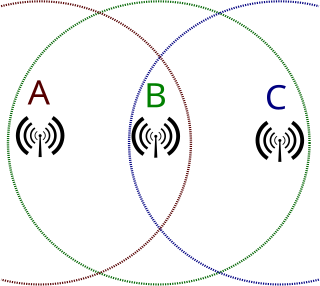
In wireless networking, the hidden node problem or hidden terminal problem occurs when a node can communicate with a wireless access point (AP), but cannot directly communicate with other nodes that are communicating with that AP. This leads to difficulties in medium access control sublayer since multiple nodes can send data packets to the AP simultaneously, which creates interference at the AP resulting in no packet getting through.

A bus network is a network topology in which nodes are directly connected to a common half-duplex link called a bus.
RTS/CTS is the optional mechanism used by the 802.11 wireless networking protocol to reduce frame collisions introduced by the hidden node problem. Originally the protocol fixed the exposed node problem as well, but modern RTS/CTS includes ACKs and does not solve the exposed node problem.
Exponential backoff is an algorithm that uses feedback to multiplicatively decrease the rate of some process, in order to gradually find an acceptable rate. These algorithms find usage in a wide range of systems and processes, with radio networks and computer networks being particularly notable.

A Medium Attachment Unit (MAU) is a transceiver which converts signals on an Ethernet cable to and from Attachment Unit Interface (AUI) signals.
On a local area network, token passing is a channel access method where a packet called a token is passed between nodes to authorize that node to communicate. In contrast to polling access methods, there is no pre-defined "master" node. The most well-known examples are IBM Token Ring and ARCNET, but there were a range of others, including FDDI, which was popular in the early to mid 1990s.

Ethernet flow control is a mechanism for temporarily stopping the transmission of data on Ethernet family computer networks. The goal of this mechanism is to avoid packet loss in the presence of network congestion.
In statistical time division multiplexing, contention is a media access method that is used to share a broadcast medium. In contention, any computer in the network can transmit data at any time.

An evolved wireless ad hoc network (EVAN) is a decentralized type of wireless network that compensates for the shortcomings of the existing wireless ad hoc network (WANET). An EVAN is ad hoc like a WANET because it does not rely on a pre-existing infrastructure, such as routers in wired networks or access points in wireless networks. Further advantages of WANETs over networks with a fixed topology include flexibility, scalability and lower administration costs. These characteristics of WANETs are maintained in EVAN as well. However, an EVAN has a physically separate resource management channel called tone channel, unlike existing WANETs. In WANETs, the data channel performs two roles: resource management and data transfer, but in EVAN, the data channel is used only for data transfer.







