
In computing, BIOS is firmware used to perform hardware initialization during the booting process, and to provide runtime services for operating systems and programs. The BIOS firmware comes pre-installed on a personal computer's system board, and it is the first software to run when powered on. The name originates from the Basic Input/Output System used in the CP/M operating system in 1975. The BIOS originally proprietary to the IBM PC has been reverse engineered by some companies looking to create compatible systems. The interface of that original system serves as a de facto standard.

In information theory and coding theory with applications in computer science and telecommunication, error detection and correction or error control are techniques that enable reliable delivery of digital data over unreliable communication channels. Many communication channels are subject to channel noise, and thus errors may be introduced during transmission from the source to a receiver. Error detection techniques allow detecting such errors, while error correction enables reconstruction of the original data in many cases.

Malware is any software intentionally designed to cause damage to a computer, server, client, or computer network. By contrast, software that causes unintentional harm due to some deficiency is typically described as a software bug. A wide variety of malware types exist, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, rogue software, wiper and scareware.

In computing, booting is the process of starting a computer. It can be initiated by hardware such as a button press, or by a software command. After it is switched on, a computer's central processing unit (CPU) has no software in its main memory, so some process must load software into memory before it can be executed. This may be done by hardware or firmware in the CPU, or by a separate processor in the computer system.
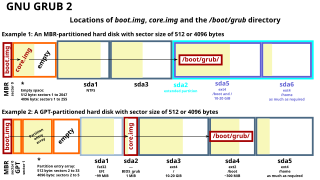
A boot sector is the sector of a persistent data storage device which contains machine code to be loaded into random-access memory (RAM) and then executed by a computer system's built-in firmware.
In computing, polymorphic code is code that uses a polymorphic engine to mutate while keeping the original algorithm intact - that is, the code changes itself every time it runs, but the function of the code will not change at all. For example, 1+3 and 6-2 both achieve the same result while using different values and operations. This technique is sometimes used by computer viruses, shellcodes and computer worms to hide their presence.

A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed and often masks its existence or the existence of other software. The term rootkit is a compound of "root" and the word "kit". The term "rootkit" has negative connotations through its association with malware.

Antivirus software, or antivirus software, also known as anti-malware, is a computer program used to prevent, detect, and remove malware.
Disk Operating System/360, also DOS/360, or simply DOS, is the discontinued first member of a sequence of operating systems for IBM System/360, System/370 and later mainframes. It was announced by IBM on the last day of 1964, and it was first delivered in June 1966. In its time, DOS/360 was the most widely used operating system in the world.
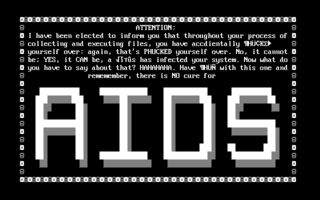
AIDS is a computer virus written in Turbo Pascal 3.01a which overwrites COM files. AIDS is the first virus known to exploit the MS-DOS "corresponding file" vulnerability. In MS-DOS, if both foo.com and foo.exe exist, then foo.com will always be executed first. Thus, by creating infected com files, AIDS code will always be executed before the intended exe code.
Win32/Simile is a metamorphic computer virus written in assembly language for Microsoft Windows. The virus was released in its most recent version in early March 2002. It was written by the virus writer "Mental Driller". Some of his previous viruses, such as Win95/Drill, have proved very challenging to detect.

Microsoft Anti-Virus (MSAV) is an antivirus program introduced by Microsoft for its MS-DOS operating system. The program first appeared in MS-DOS version 6.0 (1993) and last appeared in MS-DOS 6.22. The first version of the antivirus program was basic, had no inbuilt update facility and could scan for 1,234 different viruses. Microsoft Anti-Virus for Windows (MWAV), included as part of the package, was a front end that allowed MSAV to run properly on Windows 3.1x.
The Windows Metafile vulnerability—also called the Metafile Image Code Execution and abbreviated MICE—is a security vulnerability in the way some versions of the Microsoft Windows operating system handled images in the Windows Metafile format. It permits arbitrary code to be executed on affected computers without the permission of their users. It was discovered on December 27, 2005, and the first reports of affected computers were announced within 24 hours. Microsoft released a high-priority update to eliminate this vulnerability via Windows Update on January 5, 2006. Attacks using this vulnerability are known as WMF exploits.
4k is a computer virus which infects COM files and EXE files. The virus was one of the first file infectors to employ stealth tactics. Infected systems will hang, after September 22 every year, which is also the date of birth of Bilbo Baggins, a character from The Lord of the Rings. The code was intended to display the message Frodo Lives, but hangs in all known variants.

AmigaOS is a family of proprietary native operating systems of the Amiga and AmigaOne personal computers. It was developed first by Commodore International and introduced with the launch of the first Amiga, the Amiga 1000, in 1985. Early versions of AmigaOS required the Motorola 68000 series of 16-bit and 32-bit microprocessors. Later versions were developed by Haage & Partner and then Hyperion Entertainment. A PowerPC microprocessor is required for the most recent release, AmigaOS 4.

A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.

Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows OS software and dictionary attacks on administrator passwords to propagate while forming a botnet, and has been unusually difficult to counter because of its combined use of many advanced malware techniques. The Conficker worm infected millions of computers including government, business and home computers in over 190 countries, making it the largest known computer worm infection since the 2003 Welchia.
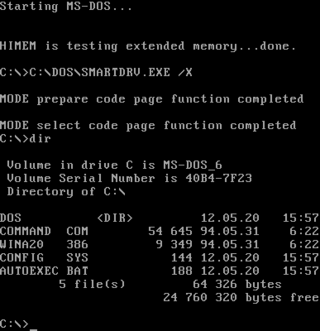
DOS is a platform-independent acronym for disk operating system which later became a common shorthand for disk-based operating systems on IBM PC compatibles. DOS primarily consists of Microsoft's MS-DOS and a rebranded version under the name IBM PC DOS, both of which were introduced in 1981. Later compatible systems from other manufacturers include DR DOS (1988), ROM-DOS (1989), PTS-DOS (1993), and FreeDOS (1998). MS-DOS dominated the IBM PC compatible market between 1981 and 1995.
A macro in computer science is a rule or pattern that specifies how a certain input sequence should be mapped to a replacement input sequence according to a defined procedure.
ANTI is a computer virus affecting Apple Macintosh computers running classic Mac OS versions up to System 6. It was the first Macintosh virus not to create additional resources within infected files; instead, it patches existing CODE resources.










