
JavaScript, often abbreviated as JS, is a programming language that is one of the core technologies of the World Wide Web, alongside HTML and CSS. As of 2022, 98% of websites use JavaScript on the client side for webpage behavior, often incorporating third-party libraries. All major web browsers have a dedicated JavaScript engine to execute the code on users' devices.
Deep Throat, Deep-throat or Deepthroat may refer to:

Cross-site scripting (XSS) is a type of security vulnerability that can be found in some web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy. Cross-site scripting carried out on websites accounted for roughly 84% of all security vulnerabilities documented by Symantec up until 2007. XSS effects vary in range from petty nuisance to significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner network.

AVG AntiVirus is a line of antivirus software developed by AVG Technologies, a subsidiary of Avast, a part of Gen Digital. It is available for Windows, macOS and Android.

Code injection is the exploitation of a computer bug that is caused by processing invalid data. The injection is used by an attacker to introduce code into a vulnerable computer program and change the course of execution. The result of successful code injection can be disastrous, for example, by allowing computer viruses or computer worms to propagate.
Men in black, in American popular culture and in UFO conspiracy theories, are men dressed in black suits who claim to be government agents who harass or threaten UFO witnesses to keep them quiet about what they have seen.
Cross-zone scripting is a browser exploit taking advantage of a vulnerability within a zone-based security solution. The attack allows content (scripts) in unprivileged zones to be executed with the permissions of a privileged zone - i.e. a privilege escalation within the client executing the script. The vulnerability could be:

USA-165 or XSS-11 is a small, washing-machine-sized, low-cost spacecraft developed by the U.S. Air Force Research Laboratory's Space Vehicles Directorate to test technology for proximity operations. In particular, the satellite was designed to demonstrate "autonomous rendezvous and proximity maneuvers." In other words, it would approach, investigate, and photograph other spacecraft in Earth orbit. It would help test the feasibility of in-space inspection and repair. The spacecraft was also designed to test systems that would allow the spacecraft to maneuver autonomously.
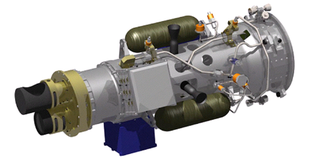
XSS-10 was a small, low-cost micro-spacecraft developed by the U.S. Air Force Research Laboratory's Space Vehicles Directorate to test technology for line-of-sight guidance of spacecraft. The project was initiated at AFRL by Program Manager David Barnhart and completed by Georgia Tech Research Institute engineer Thom Davis and team. The project was declared a success shortly after launch.

Clickjacking is a malicious technique of tricking a user into clicking on something different from what the user perceives, thus potentially revealing confidential information or allowing others to take control of their computer while clicking on seemingly innocuous objects, including web pages.
Cross-site request forgery, also known as one-click attack or session riding and abbreviated as CSRF or XSRF, is a type of malicious exploit of a website or web application where unauthorized commands are submitted from a user that the web application trusts. There are many ways in which a malicious website can transmit such commands; specially-crafted image tags, hidden forms, and JavaScript fetch or XMLHttpRequests, for example, can all work without the user's interaction or even knowledge. Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user's browser. In a CSRF attack, an innocent end user is tricked by an attacker into submitting a web request that they did not intend. This may cause actions to be performed on the website that can include inadvertent client or server data leakage, change of session state, or manipulation of an end user's account.
Content Security Policy (CSP) is a computer security standard introduced to prevent cross-site scripting (XSS), clickjacking and other code injection attacks resulting from execution of malicious content in the trusted web page context. It is a Candidate Recommendation of the W3C working group on Web Application Security, widely supported by modern web browsers. CSP provides a standard method for website owners to declare approved origins of content that browsers should be allowed to load on that website—covered types are JavaScript, CSS, HTML frames, web workers, fonts, images, embeddable objects such as Java applets, ActiveX, audio and video files, and other HTML5 features.
Self-XSS is a social engineering attack used to gain control of victims' web accounts. In a Self-XSS attack, the victim of the attack unknowingly runs malicious code in their own web browser, thus exposing personal information to the attacker, a kind of vulnerability known as cross-site scripting.

The Miniature X-ray Solar Spectrometer (MinXSS) CubeSat was the first launched National Aeronautics and Space Administration Science Mission Directorate CubeSat with a science mission. It was designed, built, and operated primarily by students at the University of Colorado Boulder with professional mentorship and involvement from professors, scientists, and engineers in the Aerospace Engineering Sciences department and the Laboratory for Atmospheric and Space Physics, as well as Southwest Research Institute, NASA Goddard Space Flight Center, and the National Center for Atmospheric Research's High Altitude Observatory. The mission principal investigator is Dr. Thomas N. Woods and co-investigators are Dr. Amir Caspi, Dr. Phil Chamberlin, Dr. Andrew Jones, Rick Kohnert, Professor Xinlin Li, Professor Scott Palo, and Dr. Stanley Solomon. The student lead was Dr. James Paul Mason, who has since become a Co-I for the second flight model of MinXSS.

Sakura Samurai was a white hat hacking and security research group that was founded in 2020. The group is responsible for multiple vulnerability disclosures involving governmental groups and various corporations.







