Related Research Articles

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
The Melissa virus is a mass-mailing macro virus released on or around March 26, 1999. It targets Microsoft Word and Outlook-based systems and created considerable network traffic. The virus infects computers via email; the email is titled "Important Message From," followed by the current username. Upon clicking the message, the body reads, "Here's that document you asked for. Don't show anyone else ;)." Attached is a Word document titled "list.doc," containing a list of pornographic sites and accompanying logins for each. It then mass-mails itself to the first fifty people in the user's contact list and disables multiple safeguard features on Microsoft Word and Microsoft Outlook.
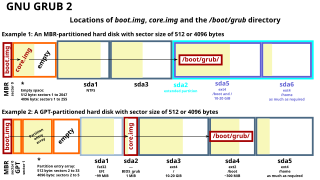
A boot sector is the sector of a persistent data storage device which contains machine code to be loaded into random-access memory (RAM) and then executed by a computer system's built-in firmware.

Antivirus software, also known as anti-malware, is a computer program used to prevent, detect, and remove malware.

CIH, also known as Chernobyl or Spacefiller, is a Microsoft Windows 9x computer virus that first emerged in 1998. Its payload is highly destructive to vulnerable systems, overwriting critical information on infected system drives and, in some cases, destroying the system BIOS. The virus was created by Chen Ing-hau, a student at Tatung University in Taiwan. It was believed to have infected sixty million computers internationally, resulting in an estimated NT$1 billion (US$35,801,231.56) in commercial damages.
Abraxas, also known as Abraxas5, discovered in April 1993, is an encrypted, overwriting, file infecting computer virus which infects .COM and .EXE files, although it does not infect command.com. It does not become memory resident. Each time an infected file is executed, Abraxas infects the copy of dosshell.com located in the C:\DOS directory, as well as one EXE file in the current directory. Due to a bug in the virus, only the first EXE file in any directory is infected.
Infectious salmon anemia (ISA) is a viral disease of Atlantic salmon caused by Salmon isavirus. It affects fish farms in Canada, Norway, Scotland and Chile, causing severe losses to infected farms. ISA has been a World Organisation for Animal Health notifiable disease since 1990. In the EU, it is classified as a non-exotic disease, and is monitored by the European Community Reference Laboratory for Fish Diseases.
In computing, data recovery is a process of retrieving deleted, inaccessible, lost, corrupted, damaged, or formatted data from secondary storage, removable media or files, when the data stored in them cannot be accessed in a usual way. The data is most often salvaged from storage media such as internal or external hard disk drives (HDDs), solid-state drives (SSDs), USB flash drives, magnetic tapes, CDs, DVDs, RAID subsystems, and other electronic devices. Recovery may be required due to physical damage to the storage devices or logical damage to the file system that prevents it from being mounted by the host operating system (OS).
The Michelangelo virus is a computer virus first discovered on 3 February 1991 in Australia. The virus was designed to infect DOS systems, but did not engage the operating system or make any OS calls. Michelangelo, like all boot sector viruses, operated at the BIOS level. Each year, the virus remained dormant until March 6, the birthday of Renaissance artist Michelangelo. There is no reference to the artist in the virus, and it is doubtful that the virus's developer(s) intended a connection between the virus and the artist. The name was chosen by researchers who noticed the coincidence of the activation date. The actual significance of the date to the author is unknown. Michelangelo is a variant of the already endemic Stoned virus.
The Hare Virus was a destructive computer virus which infected DOS and Windows 95 machines in August 1996. It was also known as Hare.7610, Krsna and HD Euthanasia.
Jerusalem is a logic bomb DOS virus first detected at Hebrew University of Jerusalem, in October 1987. On infection, the Jerusalem virus becomes memory resident, and then infects every executable file run, except for COMMAND.COM. COM files grow by 1,813 bytes when infected by Jerusalem and are not re-infected. Executable files grow by 1,808 to 1,823 bytes each time they are infected, and are then re-infected each time the files are loaded until they are too large to load into memory. Some .EXE files are infected but do not grow because several overlays follow the genuine .EXE file in the same file. Sometimes .EXE files are incorrectly infected, causing the program to fail to run as soon as it is executed.
AntiCMOS is a boot virus. Its first discovery was at Lenart, Slovenia, which led to its alias of Lenart. It was isolated in Hong Kong several times at the beginning of 1994, but did not become common until it spread to North America in the Spring of 1995. AntiCMOS is a fairly standard boot virus, and is primarily notable for being one of the few DOS viruses to remain in the wild as of 2020.
Ontario is a family of computer viruses, named after its point of isolation, the Canadian province of Ontario. This family of computer virus consists of Ontario.1024, Ontario.512 and Ontario.2048. The first variant Ontario.512 was discovered in July 1990. Because Ontario.1024 was also discovered in Ontario, it is likely that both viruses originate from within the province. By the Ontario.2048 variant, the author had adopted "Ontario" as the family's name and even included the name "Ontario-3" in the virus code.
Blackworm is an Internet worm discovered on January 20, 2006 that infects several versions of Microsoft Windows. It is also known as Grew.a, Grew.b, Blackmal.e, Nyxem.e, Nyxem.d, Mywife.d, Tearec.a, CME-24, and Kama Sutra.
Form was a boot sector virus isolated in Switzerland in the summer of 1990 which became very common worldwide. The origin of Form is widely listed as Switzerland, but this may be an assumption based on its isolation locale. The only notable characteristics of Form are that it infects the boot sector instead of the Master Boot Record (MBR) and the clicking noises associated with some infections. Infections under Form can result in severe data damage if operating system characteristics are not identical to those Form assumes.

Stoned is a boot sector computer virus created in 1987. It is one of the first viruses and is thought to have been written by a student in Wellington, New Zealand. By 1989 it had spread widely in New Zealand and Australia, and variants became very common worldwide in the early 1990s.
The Ping-Pong virus is a boot sector virus discovered on March 1, 1988, at the Politecnico di Torino in Italy. It was likely the most common and best known boot sector virus until outnumbered by the Stoned virus.
Natas is a computer virus written by James Gentile, a then-18-year-old hacker from San Diego, California who went by the alias of "Little Loc" and later "Priest". The virus was made for a Mexican politician who wanted to win the Mexican elections by affecting all the Mexican Federal Electoral Institute (IFE) computers with a floppy disk.

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.
Shamoon, also known as W32.DistTrack, is a modular computer virus that was discovered in 2012, targeting then-recent 32-bit NT kernel versions of Microsoft Windows. The virus was notable due to the destructive nature of the attack and the cost of recovery. Shamoon can spread from an infected machine to other computers on the network. Once a system is infected, the virus continues to compile a list of files from specific locations on the system, upload them to the attacker, and erase them. Finally the virus overwrites the master boot record of the infected computer, making it unusable.