
In mathematics and computer science, an algorithm is a finite sequence of well-defined, computer-implementable instructions, typically to solve a class of problems or to perform a computation. Algorithms are always unambiguous and are used as specifications for performing calculations, data processing, automated reasoning, and other tasks.
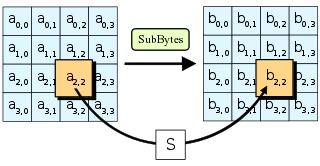
The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
In cryptography, key size or key length is the number of bits in a key used by a cryptographic algorithm.
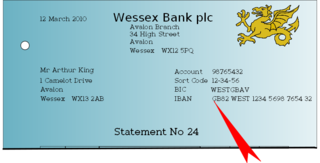
The International Bank Account Number (IBAN) is an internationally agreed system of identifying bank accounts across national borders to facilitate the communication and processing of cross border transactions with a reduced risk of transcription errors. It was originally adopted by the European Committee for Banking Standards (ECBS) and later as an international standard under ISO 13616:1997. The current standard is ISO 13616:2007, which indicates SWIFT as the formal registrar. Initially developed to facilitate payments within the European Union, it has been implemented by most European countries and numerous countries in other parts of the world, mainly in the Middle East and the Caribbean. As of February 2016, 69 countries were using the IBAN numbering system.
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991.

Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys which may be disseminated widely, and private keys which are known only to the owner. The generation of such keys depends on cryptographic algorithms based on mathematical problems to produce one-way functions. Effective security only requires keeping the private key private; the public key can be openly distributed without compromising security.
The U.S. National Security Agency (NSA) ranks cryptographic products or algorithms by a certification called product types. Product types are defined in the National Information Assurance Glossary which defines Type 1, 2, 3, and 4 products.

A capital market is a financial market in which long-term debt or equity-backed securities are bought and sold. Capital markets channel the wealth of savers to those who can put it to long-term productive use, such as companies or governments making long-term investments. Financial regulators like Securities and Exchange Board of India (SEBI), Bank of England (BoE) and the U.S. Securities and Exchange Commission (SEC) oversee capital markets to protect investors against fraud, among other duties.

A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very strong reason to believe that the message was created by a known sender (authentication), and that the message was not altered in transit (integrity).
A predictive dialer dials a list of telephone numbers and connects answered dials to people making calls, often referred to as agents. Predictive dialers use statistical algorithms to minimize the time that agents spend waiting between conversations, while minimizing the occurrence of someone answering when no agent is available.
An International Securities Identification Number (ISIN) uniquely identifies a security. Its structure is defined in ISO 6166. The ISIN code is a 12-character alphanumeric code that serves for uniform identification of a security through normalization of the assigned National Number, where one exists, at trading and settlement.
An electronic signature, or e-signature, refers to data in electronic form, which is logically associated with other data in electronic form and which is used by the signatory to sign. This type of signature provides the same legal standing as a handwritten signature as long as it adheres to the requirements of the specific regulation it was created under.

In cryptography, RC2 is a symmetric-key block cipher designed by Ron Rivest in 1987. "RC" stands for "Ron's Code" or "Rivest Cipher"; other ciphers designed by Rivest include RC4, RC5, and RC6.

Speedcubing is the hobby involving solving a variety of combination or twisty puzzles, the most famous being the 3x3x3 puzzle or Rubik's Cube, as quickly as possible. For most puzzles, solving entails performing a series of moves that alters a scrambled puzzle into a state in which every face of the puzzle is a single, solid color. Some puzzles have different requirements to be considered solved, such as the Clock, for which all the dials must be moved into the 12 'o clock position. The standard puzzle sizes are 2x2x2, 3x3x3, 4x4x4, 5x5x5, 6x6x6, and 7x7x7. There are also different shapes of the famous puzzles, including Pyraminx, Megaminx, Skewb, and Square-1. An individual who competes in speedcubing is known as a speedcuber.
Strong cryptography or cryptographic-ally strong are general terms applied to cryptographic systems or components that are considered highly resistant to cryptanalysis.

The European Community number is a unique seven-digit identifier that was assigned to substances for regulatory purposes within the European Union by the European Commission. The EC Inventory comprises three individual inventories, EINECS, ELINCS and the NLP list.

Cryptography or cryptology is the practice and study of techniques for secure communication in the presence of third parties called adversaries. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, electrical engineering, communication science, and physics. Applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications.
In financial markets, high-frequency trading (HFT) is a type of algorithmic trading characterized by high speeds, high turnover rates, and high order-to-trade ratios that leverages high-frequency financial data and electronic trading tools. While there is no single definition of HFT, among its key attributes are highly sophisticated algorithms, co-location, and very short-term investment horizons. HFT can be viewed as a primary form of algorithmic trading in finance. Specifically, it is the use of sophisticated technological tools and computer algorithms to rapidly trade securities. HFT uses proprietary trading strategies carried out by computers to move in and out of positions in seconds or fractions of a second.
The operations manual is the documentation by which an organisation provides guidance for members and employees to perform their functions correctly and reasonably efficiently. It documents the approved standard procedures for performing operations safely to produce goods and provide services. Compliance with the operations manual will generally be considered as activity approved by the persons legally responsible for the organisation.
Government by algorithm is an alternative form of government or also social ordering, where the advantages and usages of computer algorithms, especially of artificial intelligence, are applied to regulations, law enforcement and generally any aspect of everyday life like transportation system e.g..









