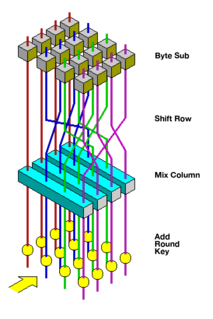
The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.

A password, sometimes called a passcode, is secret data, typically a string of characters, usually used to confirm a user's identity. Traditionally, passwords were expected to be memorized, but the large number of password-protected services that a typical individual accesses can make memorization of unique passwords for each service impractical. Using the terminology of the NIST Digital Identity Guidelines, the secret is held by a party called the claimant while the party verifying the identity of the claimant is called the verifier. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity.
In cryptography, SHA-1 is a cryptographically broken but still widely used hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits. It was designed by the United States National Security Agency, and is a U.S. Federal Information Processing Standard.

Bruce Schneier is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is a Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Center for Internet & Society as of November, 2013. He is a board member of the Electronic Frontier Foundation, Access Now, and The Tor Project; and an advisory board member of Electronic Privacy Information Center and VerifiedVoting.org. He is the author of several books on general security topics, computer security and cryptography and is a squid enthusiast.

Security is protection from, or resilience against, potential harm caused by others, by restraining the freedom of others to act. Beneficiaries of security may be of persons and social groups, objects and institutions, ecosystems or any other entity or phenomenon vulnerable to unwanted change.
Critical thinking is the analysis of available facts, evidence, observations, and arguments to form a judgement. The subject is complex; several different definitions exist, which generally include the rational, skeptical, and unbiased analysis or evaluation of factual evidence. Critical thinking is self-directed, self-disciplined, self-monitored, and self-corrective thinking. It presupposes assent to rigorous standards of excellence and mindful command of their use. It entails effective communication and problem-solving abilities as well as a commitment to overcome native egocentrism and sociocentrism.

Books on cryptography have been published sporadically and with highly variable quality for a long time. This is despite the tempting, though superficial, paradox that secrecy is of the essence in sending confidential messages — see Kerckhoffs' principle.

A Cooper vane is a mechanical aerodynamic wedge that prevents the ventral airstair of an aircraft from being lowered in flight.
Security theater is the practice of taking security measures that are considered to provide the feeling of improved security while doing little or nothing to achieve it.

Culture of fear is the concept that people may incite fear in the general public to achieve political or workplace goals through emotional bias; it was developed as a sociological framework by Frank Furedi and has been more recently popularized by the American sociologist Barry Glassner.

An airstair is a set of steps built into an aircraft so that passengers may board and alight the aircraft. The stairs are often built into a clamshell-style door on the aircraft. Airstairs eliminate the need for passengers to use a mobile stairway or jetway to board or exit the aircraft, providing more independence from ground services. Some of the earliest aircraft to feature airstairs were the Martin 2-0-2 and Martin 4-0-4. Some models of the Douglas DC-3 were also retrofitted with airstairs. As airport infrastructure has developed, the need for airstairs has decreased, as jetways or mobile stairways are often available.

Password strength is a measure of the effectiveness of a password against guessing or brute-force attacks. In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. The strength of a password is a function of length, complexity, and unpredictability.

The Black Swan: The Impact of the Highly Improbable is a 2007 book by author and former options trader Nassim Nicholas Taleb. The book focuses on the extreme impact of rare and unpredictable outlier events—and the human tendency to find simplistic explanations for these events, retrospectively. Taleb calls this the Black Swan theory.
Social anxiety is the anxiety and fear specifically linked to being in social settings. Some categories of disorders associated with social anxiety include anxiety disorders, mood disorders, autism spectrum disorders, eating disorders, and substance use disorders. Individuals with higher levels of social anxiety often avert their gazes, show fewer facial expressions, and show difficulty with initiating and maintaining a conversation. Social anxiety commonly manifests itself in the teenage years and can be persistent throughout life, however, people who experience problems in their daily functioning for an extended period of time can develop social anxiety disorder. Trait social anxiety, the stable tendency to experience this anxiety, can be distinguished from state anxiety, the momentary response to a particular social stimulus. Half of the individuals with any social fears meet the criteria for social anxiety disorder. Age, culture, and gender impact the severity of this disorder. The function of social anxiety is to increase arousal and attention to social interactions, inhibit unwanted social behavior, and motivate preparation for future social situations.
In simple terms, risk is the possibility of something bad happening. Risk involves uncertainty about the effects/implications of an activity with respect to something that humans value, often focusing on negative, undesirable consequences. Many different definitions have been proposed. The international standard definition of risk for common understanding in different applications is “effect of uncertainty on objectives”.
This article summarizes publicly known attacks against block ciphers and stream ciphers. Note that there are perhaps attacks that are not publicly known, and not all entries may be up to date.

The nothing to hide argument states that individuals have no reason to fear or oppose surveillance programs, unless they are afraid it will uncover their own illicit activities. An individual using this argument may claim that an average person should not worry about government surveillance, as they would have "nothing to hide".

Bullrun is a clandestine, highly classified program to crack encryption of online communications and data, which is run by the United States National Security Agency (NSA). The British Government Communications Headquarters (GCHQ) has a similar program codenamed Edgehill. According to the Bullrun classification guide published by The Guardian, the program uses multiple methods including computer network exploitation, interdiction, industry relationships, collaboration with other intelligence community entities, and advanced mathematical techniques.
The Aluth Oya massacre was the massacre of 127 Sinhalese civilians, including children and women, by the cadres of Liberation Tigers of Tamil Eelam organization on April 17, 1987, near the village of Aluth Oya, on the Habarana Trincomalee road in North Central Province of Sri Lanka. This massacre is considered one of the most notorious and devastating atrocities committed by the LTTE during the history of the Sri Lankan Civil War.











