
Information warfare (IW) is the battlespace use and management of information and communication technology (ICT) in pursuit of a competitive advantage over an opponent. It is different from cyberwarfare that attacks computers, software, and command control systems. Information warfare is the manipulation of information trusted by a target without the target's awareness so that the target will make decisions against their interest but in the interest of the one conducting information warfare. As a result, it is not clear when information warfare begins, ends, and how strong or destructive it is.
Cyberterrorism is the use of the Internet to conduct violent acts that result in, or threaten, the loss of life or significant bodily harm, in order to achieve political or ideological gains through threat or intimidation. Acts of deliberate, large-scale disruption of computer networks, especially of personal computers attached to the Internet by means of tools such as computer viruses, computer worms, phishing, malicious software, hardware methods, programming scripts can all be forms of internet terrorism. Cyberterrorism is a controversial term. Some authors opt for a very narrow definition, relating to deployment by known terrorist organizations of disruption attacks against information systems for the primary purpose of creating alarm, panic, or physical disruption. Other authors prefer a broader definition, which includes cybercrime. Participating in a cyberattack affects the terror threat perception, even if it isn't done with a violent approach. By some definitions, it might be difficult to distinguish which instances of online activities are cyberterrorism or cybercrime.
John Arquilla is an American analyst and academic of international relations.

Cyberwarfare is the use of cyber attacks against an enemy state, causing comparable harm to actual warfare and/or disrupting vital computer systems. Some intended outcomes could be espionage, sabotage, propaganda, manipulation or economic warfare.
Five Pillars or five pillars may refer to:

Command and control is a "set of organizational and technical attributes and processes ... [that] employs human, physical, and information resources to solve problems and accomplish missions" to achieve the goals of an organization or enterprise, according to a 2015 definition by military scientists Marius Vassiliou, David S. Alberts, and Jonathan R. Agre. The term often refers to a military system.
A cyber force is a military branch of a nation's armed forces that conducts military operations in cyberspace and cyberwarfare. The world's first independent cyber force was the People's Liberation Army Strategic Support Force, which was established in 2015 and also serves as China's space force. As of 2022, the world's only independent cyber forces are the PLA Strategic Support Force, the German Cyber and Information Domain Service, Norwegian Cyber Defence Force, and the Singapore Digital and Intelligence Service.
Beginning on 27 April 2007, a series of cyberattacks targeted websites of Estonian organizations, including Estonian parliament, banks, ministries, newspapers and broadcasters, amid the country's disagreement with Russia about the relocation of the Bronze Soldier of Tallinn, an elaborate Soviet-era grave marker, as well as war graves in Tallinn. Most of the attacks that had any influence on the general public were distributed denial of service type attacks ranging from single individuals using various methods like ping floods to expensive rentals of botnets usually used for spam distribution. Spamming of bigger news portals commentaries and defacements including that of the Estonian Reform Party website also occurred. Research has also shown that large conflicts took place to edit the English-language version of the Bronze Soldier's Wikipedia page.
Proactive cyber defense, means acting in anticipation to oppose an attack through cyber and cognitive domains. Proactive cyber defense can be understood as options between offensive and defensive measures. It includes interdicting, disrupting or deterring an attack or a threat's preparation to attack, either pre-emptively or in self-defence.
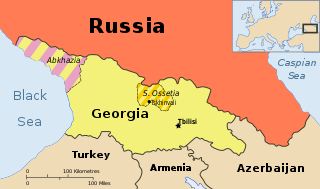
During the Russo-Georgian War, a series of cyberattacks swamped and disabled websites of numerous South Ossetian, Georgian, Russian and Azerbaijani organisations. The attacks were initiated three weeks before the shooting war began.
Cyberwarfare by Russia includes denial of service attacks, hacker attacks, dissemination of disinformation and propaganda, participation of state-sponsored teams in political blogs, internet surveillance using SORM technology, persecution of cyber-dissidents and other active measures. According to investigative journalist Andrei Soldatov, some of these activities were coordinated by the Russian signals intelligence, which was part of the FSB and formerly a part of the 16th KGB department. An analysis by the Defense Intelligence Agency in 2017 outlines Russia's view of "Information Countermeasures" or IPb as "strategically decisive and critically important to control its domestic populace and influence adversary states", dividing 'Information Countermeasures' into two categories of "Informational-Technical" and "Informational-Psychological" groups. The former encompasses network operations relating to defense, attack, and exploitation and the latter to "attempts to change people's behavior or beliefs in favor of Russian governmental objectives."

United States Cyber Command (USCYBERCOM) is one of the eleven unified combatant commands of the United States Department of Defense (DoD). It unifies the direction of cyberspace operations, strengthens DoD cyberspace capabilities, and integrates and bolsters DoD's cyber expertise which focus on securing cyberspace.

Cyber ShockWave, similar to the Cyber Storm Exercise, was a 4-hour wargame conducted in February 2010 by the Bipartisan Policy Center, an American think tank based in Washington, D.C. Former high-ranking Cabinet and National Security Officials role played a cabinet level response to a cyberwarfare scenario. Portions of the exercise were later broadcast on CNN.
Cyberwarfare is the use of computer technology to disrupt the activities of a state or organization, especially the deliberate attacking of information systems for strategic or military purposes. As a major developed economy, the United States is highly dependent on the Internet and therefore greatly exposed to cyber attacks. At the same time, the United States has substantial capabilities in both defense and power projection thanks to comparatively advanced technology and a large military budget. Cyber warfare presents a growing threat to physical systems and infrastructures that are linked to the internet. Malicious hacking from domestic or foreign enemies remains a constant threat to the United States. In response to these growing threats, the United States has developed significant cyber capabilities.
Jeffrey Carr is a cybersecurity author, researcher, entrepreneur and consultant, who focuses on cyber warfare.

The military-digital complex (MDC) is the militarization of cyber operations by governments and corporations, often through monetary relationships between computer programmers in private companies and the military to combat the threat of cyber terrorism and warfare. Cyber operations since 2000 have increased dramatically, with the recent branch of the US Strategic Command the United States Cyber Command. Cyber operations has been defined by the Washington Post as,
The Tallinn Manual is an academic, non-binding study on how international law applies to cyber conflicts and cyber warfare. Between 2009 and 2012, the Tallinn Manual was written at the invitation of the Tallinn-based NATO Cooperative Cyber Defence Centre of Excellence by an international group of approximately twenty experts. In April 2013, the manual was published by Cambridge University Press.
The Fifth Dimension of Warfare complements the four classical dimensions: land, sea, air, and space. It was enunciated in 1995 as information operations.

Cyberwarfare is a component of the confrontation between Russia and Ukraine since the Revolution of Dignity in 2013-2014. While the first attacks on information systems of private enterprises and state institutions of Ukraine were recorded during mass protests in 2013, Russian cyberweapon Uroburos had been around since 2005. Russian cyberwarfare continued with the 2015 Ukraine power grid hack at Christmas 2015 and again in 2016, paralysis of the State Treasury of Ukraine in December 2016, a Mass hacker supply-chain attack in June 2017 and attacks on Ukrainian government websites in January 2022.

Sandworm is an Advanced Persistent Threat operated by Military Unit 74455, a cyberwarfare unit of the GRU, Russia's military intelligence service. Other names for the group, given by cybersecurity researchers, include Telebots, Voodoo Bear, and Iron Viking.








