
A packet analyzer or packet sniffer is a computer program or computer hardware such as a packet capture appliance, that can intercept and log traffic that passes over a computer network or part of a network. Packet capture is the process of intercepting and logging traffic. As data streams flow across the network, the analyzer captures each packet and, if needed, decodes the packet's raw data, showing the values of various fields in the packet, and analyzes its content according to the appropriate RFC or other specifications.
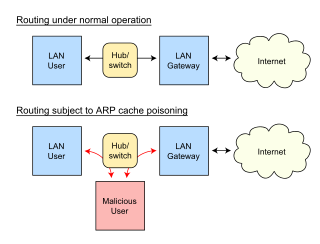
In computer networking, ARP spoofing, ARP cache poisoning, or ARP poison routing, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address to be sent to the attacker instead.
arpwatch is a computer software tool for monitoring Address Resolution Protocol traffic on a computer network. It generates a log of observed pairing of IP addresses with MAC addresses along with a timestamp when the pairing appeared on the network. It also has the option of sending an email to an administrator when a pairing changes or is added.

TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. The combination of parameters may then be used to infer the remote machine's operating system, or incorporated into a device fingerprint.

Ettercap is a free and open source network security tool for man-in-the-middle attacks on LAN. It can be used for computer network protocol analysis and security auditing. It runs on various Unix-like operating systems including Linux, Mac OS X, BSD and Solaris, and on Microsoft Windows. It is capable of intercepting traffic on a network segment, capturing passwords, and conducting active eavesdropping against a number of common protocols. Its original developers later founded Hacking Team.

Rhett James McLaughlin and Charles Lincoln "Link" Neal III, known as Rhett & Link, are an American comedy duo. Self-styled as "Internetainers", they are known for creating and hosting the YouTube series Good Mythical Morning. Their other notable projects include comedic songs and sketches, their Independent Film Channel series Rhett & Link: Commercial Kings, their YouTube Premium series Rhett and Link's Buddy System, their podcast Ear Biscuits, their novel The Lost Causes of Bleak Creek and their acquisition of Smosh.
Information source may refer to:
Twilight series may refer to:
Neutral point of view may refer to:
Ashley Lane may refer to:
LGBT literature may refer to:
ipsectrace is a software tool designed by Wayne Schroeder to help profile IPsec connections in a packet capture (PCP) file. The program uses a command line interface to point at a PCP capture and informs the user about what is going on. It is somewhat inspired by tcptrace, which uses the same input of PCP files. Ipsectrace is only available for the Linux operating system. It is coded in C++ and is licensed under the GPL, effectively allowing anyone to modify and redistribute it.

BackBox is a penetration test and security assessment oriented Ubuntu-based Linux distribution providing a network and informatic systems analysis toolkit. It includes a complete set of tools required for ethical hacking and security testing.

Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security.
Cambridge Movement may refer to:
Timeline of the COVID-19 pandemic in Indonesia may refer to:
The visa policy of China may refer to:
This page is based on this
Wikipedia article Text is available under the
CC BY-SA 4.0 license; additional terms may apply.
Images, videos and audio are available under their respective licenses.






