Flowmon probe - result of research activities
Flowmon probe is an appliance for monitoring and reporting information of IP flows in high-speed computer networks. The probe is being developed by Liberouter team within the scope of CESNET research plan Optical National Research Network and its New Applications, research activity 602 - Programmable hardware.
Flowmon probe is built upon a pair of programmable network cards, called COMBO, and a host computer with Linux operating system. The pair of COMBO cards consists of a main card with PCI, PCI-X or PCI-Express connector for a connection to a motherboard of the host computer and of an add-on card with 2 or 4 network interfaces. Both cards contain programmable chips (FPGAs) which are able to process high amount of data at multi-gigabit speed. The flow monitoring process itself is split between the hardware (acceleration cards) and the application software running on the host computer. Following the principle of hardware/software codesign, all time-critical tasks are implemented in FPGA chips on acceleration cards while more complex operations are carried out by the application software. This concept enables monitoring of modern high-speed (1 Gbps, 10 Gbps) networks with no packet loss and with no necessity of input sampling. At the same time, a flexible and user-friendly interface is provided by software.
Flowmon probe is a passive monitoring device, i.e. it does not alter passing traffic in any way. Therefore, its detection is hardly possible. When connected to a network, Flowmon probe observes all passing traffic/packets, extracts and aggregates information of IP flows into flow records. Flowmon probe is able to export aggregated data to external collectors in NetFlow (version 5 and 9) and IPFIX format. Collectors collect incoming flow records and store them for automated or manual and visual analysis (automated malicious traffic detection, filter rules, graphs and statistical schemas). The whole system allows monitoring of actual state of monitored network as well as long-term traffic analysis.
Flowmon probe is part of GÉANT2 Security Toolset, which consists of the NetFlow analysis tools NfSen and NfDump and the Flowmon appliance.

An embedded system is a computer system—a combination of a computer processor, computer memory, and input/output peripheral devices—that has a dedicated function within a larger mechanical or electronic system. It is embedded as part of a complete device often including electrical or electronic hardware and mechanical parts. Because an embedded system typically controls physical operations of the machine that it is embedded within, it often has real-time computing constraints. Embedded systems control many devices in common use. In 2009, it was estimated that ninety-eight percent of all microprocessors manufactured were used in embedded systems.

A packet analyzer, also known as packet sniffer, protocol analyzer, or network analyzer, is a computer program or computer hardware such as a packet capture appliance that can analyze and log traffic that passes over a computer network or part of a network. Packet capture is the process of intercepting and logging traffic. As data streams flow across the network, the analyzer captures each packet and, if needed, decodes the packet's raw data, showing the values of various fields in the packet, and analyzes its content according to the appropriate RFC or other specifications.

A system on a chip or system-on-chip is an integrated circuit that integrates most or all components of a computer or other electronic system. These components almost always include on-chip central processing unit (CPU), memory interfaces, input/output devices, input/output interfaces, and secondary storage interfaces, often alongside other components such as radio modems and a graphics processing unit (GPU) – all on a single substrate or microchip. SoCs may contain digital, and also analog, mixed-signal, and often radio frequency signal processing functions.

An intrusion detection system is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms.
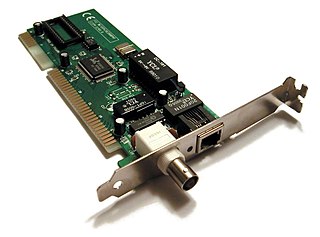
A network interface controller is a computer hardware component that connects a computer to a computer network.
In computer networking, promiscuous mode is a mode for a wired network interface controller (NIC) or wireless network interface controller (WNIC) that causes the controller to pass all traffic it receives to the central processing unit (CPU) rather than passing only the frames that the controller is specifically programmed to receive. This mode is normally used for packet sniffing that takes place on a router or on a computer connected to a wired network or one being part of a wireless LAN. Interfaces are placed into promiscuous mode by software bridges often used with hardware virtualization.
TCP offload engine (TOE) is a technology used in some network interface cards (NIC) to offload processing of the entire TCP/IP stack to the network controller. It is primarily used with high-speed network interfaces, such as gigabit Ethernet and 10 Gigabit Ethernet, where processing overhead of the network stack becomes significant. TOEs are often used as a way to reduce the overhead associated with Internet Protocol (IP) storage protocols such as iSCSI and Network File System (NFS).

NetFlow is a feature that was introduced on Cisco routers around 1996 that provides the ability to collect IP network traffic as it enters or exits an interface. By analyzing the data provided by NetFlow, a network administrator can determine things such as the source and destination of traffic, class of service, and the causes of congestion. A typical flow monitoring setup consists of three main components:

Hardware acceleration is the use of computer hardware designed to perform specific functions more efficiently when compared to software running on a general-purpose central processing unit (CPU). Any transformation of data that can be calculated in software running on a generic CPU can also be calculated in custom-made hardware, or in some mix of both.

A hardware security module (HSM) is a physical computing device that safeguards and manages secrets, performs encryption and decryption functions for digital signatures, strong authentication and other cryptographic functions. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server. A hardware security module contains one or more secure cryptoprocessor chips.
Capacity management's goal is to ensure that information technology resources are sufficient to meet upcoming business requirements cost-effectively. One common interpretation of capacity management is described in the ITIL framework. ITIL version 3 views capacity management as comprising three sub-processes: business capacity management, service capacity management, and component capacity management.
In computer networks, network traffic measurement is the process of measuring the amount and type of traffic on a particular network. This is especially important with regard to effective bandwidth management.
Network behavior anomaly detection (NBAD) is a security technique that provides network security threat detection. It is a complementary technology to systems that detect security threats based on packet signatures.
A bypass switch (or bypass TAP) is a hardware device that provides a fail-safe access port for an in-line active security appliance such as an intrusion prevention system (IPS), next generation firewall (NGFW), etc. Active, in-line security appliances are single points of failure in live computer networks because if the appliance loses power, experiences a software failure, or is taken off-line for updates or upgrades, traffic can no longer flow through the critical link. The bypass switch or bypass tap removes this point of failure by automatically 'switching traffic via bypass mode' to keep the critical network link up.
Telesoft Technologies is a privately held UK based technology company which develops cyber security, telecoms mobile products and services and government infrastructure. Telesoft has operations in USA, UK and India.
The NetFPGA project is an effort to develop open-source hardware and software for rapid prototyping of computer network devices. The project targeted academic researchers, industry users, and students. It was not the first platform of its kind in the networking community. NetFPGA used an FPGA-based approach to prototyping networking devices. This allows users to develop designs that are able to process packets at line-rate, a capability generally unafforded by software based approaches. NetFPGA focused on supporting developers that can share and build on each other's projects and IP building blocks.
Deep content inspection (DCI) is a form of network filtering that examines an entire file or MIME object as it passes an inspection point, searching for viruses, spam, data loss, key words or other content level criteria. Deep Content Inspection is considered the evolution of Deep Packet Inspection with the ability to look at what the actual content contains instead of focusing on individual or multiple packets. Deep Content Inspection allows services to keep track of content across multiple packets so that the signatures they may be searching for can cross packet boundaries and yet they will still be found. An exhaustive form of network traffic inspection in which Internet traffic is examined across all the seven OSI ISO layers, and most importantly, the application layer.
In digital communications networks, packet processing refers to the wide variety of algorithms that are applied to a packet of data or information as it moves through the various network elements of a communications network. With the increased performance of network interfaces, there is a corresponding need for faster packet processing.
A software-defined wide area network (SD-WAN) is a wide area network that uses software-defined network technology, such as communicating over the Internet using overlay tunnels which are encrypted when destined for internal organization locations.
Flowmon Networks is a privately held technology company which develops network performance monitoring and network security products utilizing information from traffic flow. Its Flowmon product series consists of network monitoring probes, collectors for flow data analysis and software modules which extend probes and collectors by analytical features for network behavior anomaly detection, network awareness application performance management, DDoS detection and mitigation and traffic recording.







