Related Research Articles
In computing terminology, a macro virus is a virus that is written in a macro language: a programming language which is embedded inside a software application. Some applications, such as Microsoft Office, Excel, PowerPoint allow macro programs to be embedded in documents such that the macros are run automatically when the document is opened, and this provides a distinct mechanism by which malicious computer instructions can spread. This is one reason it can be dangerous to open unexpected attachments in e-mails. Many antivirus programs can detect macro viruses; however, the macro virus' behavior can still be difficult to detect.

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
Bagle was a mass-mailing computer worm affecting Microsoft Windows. The first strain, Bagle.A, did not propagate widely. A second variant, Bagle.B, was considerably more virulent.
Local Security Authority Subsystem Service (LSASS) is a process in Microsoft Windows operating systems that is responsible for enforcing the security policy on the system. It verifies users logging on to a Windows computer or server, handles password changes, and creates access tokens. It also writes to the Windows Security Log.
ILOVEYOU, sometimes referred to as the Love Bug or Loveletter, was a computer worm that infected over ten million Windows personal computers on and after May 5, 2000. It started spreading as an email message with the subject line "ILOVEYOU" and the attachment "LOVE-LETTER-FOR-YOU.TXT.vbs." At the time, Windows computers often hid the latter file extension by default because it is an extension for a file type that Windows knows, leading unwitting users to think it was a normal text file. Opening the attachment activates the Visual Basic script. First, the worm inflicts damage on the local machine, overwriting random files, then, it copies itself to all addresses in the Windows Address Book used by Microsoft Outlook, allowing it to spread much faster than any other previous email worm.
The Sober worm is a family of computer worms that was discovered on October 24, 2003. Like many worms, Sober sends itself as an e-mail attachment, fake webpages, fake pop-up ads, and fake advertisements.
Criticism of Windows XP deals with issues with security, performance and the presence of product activation errors that are specific to the Microsoft operating system Windows XP.
CTX is a computer virus created in Spain in 1999. CTX was initially discovered as part of the Cholera worm, with which the author intentionally infected with CTX. Although the Cholera worm had the capability to send itself via email, the CTX worm quickly surpassed it in prevalence. Cholera is now considered obsolete, while CTX remains in the field, albeit with only rare discoveries.
The Vundo Trojan is either a Trojan horse or a computer worm that is known to cause popups and advertising for rogue antispyware programs, and sporadically other misbehavior including performance degradation and denial of service with some websites including Google and Facebook. It also is used to deliver other malware to its host computers. Later versions include rootkits and ransomware.
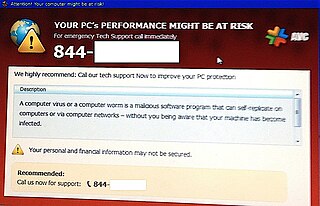
A computer virus hoax is a message warning the recipients of a non-existent computer virus threat. The message is usually a chain e-mail that tells the recipients to forward it to everyone they know, but it can also be in the form of a pop-up window.
W32.Navidad is a mass-mailing worm program or virus, discovered in December 2000 that ran on Windows 95, Windows 98, Windows NT, and Windows 2000 systems. It was designed to spread through email clients such as Microsoft Outlook while masquerading as an executable electronic Christmas card. Infected computers can be identified by blue eye icons which appear in the Windows system tray.
RavMonE, also known as RJump, is a Trojan that opens a backdoor on computers running Microsoft Windows. Once a computer is infected, the virus allows unauthorized users to gain access to the computer's contents. This poses a security risk for the infected machine's user, as the attacker can steal personal information, and use the computer as an access point into an internal network.

The Storm Worm is a phishing backdoor Trojan horse that affects computers using Microsoft operating systems, discovered on January 17, 2007. The worm is also known as:

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.
Happy99 is a computer worm for Microsoft Windows. It first appeared in mid-January 1999, spreading through email and usenet. The worm installs itself and runs in the background of a victim's machine, without their knowledge. It is generally considered the first virus to propagate by email, and has served as a template for the creation of other self-propagating viruses. Happy99 has spread on multiple continents, including North America, Europe, and Asia.
The Pikachu virus, sometimes referred to as Pokey or the Pokémon virus, was a computer worm believed to be the first malware geared at children due to its incorporation of Pikachu from the Pokémon series. It was released on June 28, 2000, and arrived in the form of an email titled "Pikachu Pokemon" [sic] with the body of the e-mail containing the text "Pikachu is your friend." Opening the attached executable shows users an image of Pikachu, along with a message stating: "Between millions of people around the world I found you. Don’t forget to remember this day every time MY FRIEND!" The worm itself appeared in the attachment to the email as a file named "PikachuPokemon.exe".
Sality is the classification for a family of malicious software (malware), which infects Microsoft Windows systems files. Sality was first discovered in 2003 and has advanced to become a dynamic, enduring and full-featured form of malicious code. Systems infected with Sality may communicate over a peer-to-peer (P2P) network to form a botnet to relay spam, proxying of communications, exfiltrating sensitive data, compromising web servers and/or coordinating distributed computing tasks to process intensive tasks. Since 2010, certain variants of Sality have also incorporated rootkit functions as part of an ongoing evolution of the malware family. Because of its continued development and capabilities, Sality is considered one of the most complex and formidable forms of malware to date.
Slenfbot is the classification for a family of malicious software (malware), which infects files on Microsoft Windows systems. Slenfbot was first discovered in 2007 and, since then, numerous variants have followed; each with slightly different characteristics and new additions to the worm's payload, such as the ability to provide the attacker with unauthorized access to the compromised host. Slenfbot primarily spreads by luring users to follow links to websites, which contain a malicious payload. Slenfbot propagates via instant messaging applications, removable drives and/or the local network via network shares. The code for Slenfbot appears to be closely managed, which may provide attribution to a single group and/or indicate that a large portion of the code is shared amongst multiple groups. The inclusion of other malware families and variants as well as its own continuous evolution, makes Slenfbot a highly effective downloader with a propensity to cause even more damage to compromised systems.

Trojan:Win32/FakeSysdef, originally dispersed as an application called "HDD Defragmenter" hence the name "FakeSysdef" or "Fake System Defragmenter", is a Trojan targeting the Microsoft Windows operating system that was first documented in late 2010.
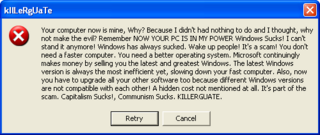
Gruel, also referred to by F-Secure as Fakerr, was a worm first surfacing in 2003 targeting Microsoft Windows platforms such as Windows 9x, Windows ME, Windows 2000 and Windows XP. It spread via email and file sharing networks.