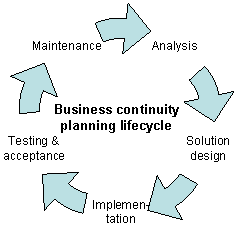
Business continuity may be defined as "the capability of an organization to continue the delivery of products or services at pre-defined acceptable levels following a disruptive incident", and business continuity planning is the process of creating systems of prevention and recovery to deal with potential threats to a company. In addition to prevention, the goal is to enable ongoing operations before and during execution of disaster recovery. Business continuity is the intended outcome of proper execution of both business continuity planning and disaster recovery.

Emergency services and rescue services are organizations that ensure public safety, security, and health by addressing and resolving different emergencies. Some of these agencies exist solely for addressing certain types of emergencies, while others deal with ad hoc emergencies as part of their normal responsibilities. Many of these agencies engage in community awareness and prevention programs to help the public avoid, detect, and report emergencies effectively. Emergency services are often considered first responders, and typically have dedicated emergency vehicles.

The Incident Command System (ICS) is a standardized approach to the command, control, and coordination of emergency response providing a common hierarchy within which responders from multiple agencies can be effective.
Vulnerabilities are flaws in a computer system that weaken the overall security of the device/system. Vulnerabilities can be weaknesses in either the hardware itself, or the software that runs on the hardware. Vulnerabilities can be exploited by a threat actor, such as an attacker, to cross privilege boundaries within a computer system. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerabilities are also known as the attack surface. Constructs in programming languages that are difficult to use properly can also manifest large numbers of vulnerabilities.
The National Incident Management System (NIMS) is a standardized approach to incident management developed by the United States Department of Homeland Security. The program was established in March 2004, in response to Homeland Security Presidential Directive-5, issued by President George W. Bush. It is intended to facilitate coordination between all responders. The system has been revised once, in December 2008. NIMS is the common framework that integrates a wide range of capabilities to help achieve objectives.
An incident is an event that could lead to loss of, or disruption to, an organization's operations, services or functions. Incident management (IcM) is a term describing the activities of an organization to identify, analyze, and correct hazards to prevent a future re-occurrence. These incidents within a structured organization are normally dealt with by either an incident response team (IRT), an incident management team (IMT), or Incident Command System (ICS). Without effective incident management, an incident can disrupt business operations, information security, IT systems, employees, customers, or other vital business functions.

In the U.S., critical infrastructure protection (CIP) is a concept that relates to the preparedness and response to serious incidents that involve the critical infrastructure of a region or the nation. The American Presidential directive PDD-63 of May 1998 set up a national program of "Critical Infrastructure Protection". In 2014 the NIST Cybersecurity Framework was published after further presidential directives.
Information assurance (IA) is the practice of assuring information and managing risks related to the use, processing, storage, and transmission of information. Information assurance includes protection of the integrity, availability, authenticity, non-repudiation and confidentiality of user data. IA encompasses both digital protections and physical techniques. These methods apply to data in transit, both physical and electronic forms, as well as data at rest. IA is best thought of as a superset of information security, and as the business outcome of information risk management.
In the United States, the hospital incident command system (HICS) is an incident command system (ICS) designed for hospitals and intended for use in both emergency and non-emergency situations. It provides hospitals of all sizes with tools needed to advance their emergency preparedness and response capability—both individually and as members of the broader response community.
ISO/IEC 27002 is an information security standard published by the International Organization for Standardization (ISO) and by the International Electrotechnical Commission (IEC), titled Information security, cybersecurity and privacy protection — Information security controls.
The ISO/IEC 27000-series comprises information security standards published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).

The Oklahoma Office of Homeland Security (OKOHS) is an agency of State of Oklahoma that is responsible for reducing the State's vulnerability to acts of terrorism and for minimizing and recovering the damage caused by terrorist attacks. OKOHS is a division of the Oklahoma Department of Public Safety.
The United States National Response Framework (NRF) is part of the National Strategy for Homeland Security that presents the guiding principles enabling all levels of domestic response partners to prepare for and provide a unified national response to disasters and emergencies. Building on the existing National Incident Management System (NIMS) as well as Incident Command System (ICS) standardization, the NRF's coordinating structures are always in effect for implementation at any level and at any time for local, state, and national emergency or disaster response.
Information technology risk, IT risk, IT-related risk, or cyber risk is any risk relating to information technology. While information has long been appreciated as a valuable and important asset, the rise of the knowledge economy and the Digital Revolution has led to organizations becoming increasingly dependent on information, information processing and especially IT. Various events or incidents that compromise IT in some way can therefore cause adverse impacts on the organization's business processes or mission, ranging from inconsequential to catastrophic in scale.
Emergency management software is the software used by local, state and federal emergency management personnel to deal with a wide range of disasters and can take many forms. For example, training software such as simulators are often used to help prepare first responders, word processors can keep form templates handy for printing and analytical software can be used to perform post-hoc examinations of the data captured during an incident. All of these systems are interrelated, as the results of an after-incident analysis can then be used to program training software to better prepare for a similar situation in the future. Crisis Information Management Software (CIMS) is the software found in emergency management operation centers (EOC) that supports the management of crisis information and the corresponding response by public safety agencies.
Homeland Security Presidential Directive (HSPD)-8, National Preparedness, describes the way United States Federal agencies will prepare for an incident. It requires Department of Homeland Security to coordinate with other Federal agencies and with State, local, and Tribal governments to develop a National Preparedness Goal with Emergency management. Congressional laws enacted, following the wake of 9/11, which resulted in new developments in the way security was assessed and addressed in the United States, to prevent and respond to threatened or actual domestic terrorist attacks, disasters, and other emergencies by requiring a national domestic all-hazards preparedness goal. HSPD 5, HSPD-7, HSPD-8, and HSPD-8 Annex 1 are directives that deal with the preparedness goals.
Security information and event management (SIEM) is a field within the field of computer security, where software products and services combine security information management (SIM) and security event management (SEM). They provide real-time analysis of security alerts generated by applications and network hardware. Vendors sell SIEM as software, as appliances, or as managed services; these products are also used to log security data and generate reports for compliance purposes. The term and the initialism SIEM was coined by Mark Nicolett and Amrit Williams of Gartner in 2005.

IT risk management is the application of risk management methods to information technology in order to manage IT risk, i.e.:
ISO/IEC 27001 is an international standard to manage information security. The standard was originally published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) in 2005, revised in 2013, and again most recently in 2022. There are also numerous recognized national variants of the standard. It details requirements for establishing, implementing, maintaining and continually improving an information security management system (ISMS) – the aim of which is to help organizations make the information assets they hold more secure. Organizations that meet the standard's requirements can choose to be certified by an accredited certification body following successful completion of an audit. The effectiveness of the ISO/IEC 27001 certification process and the overall standard has been addressed in a large-scale study conducted in 2020.
ISO 22300:2021, Security and resilience – Vocabulary, is an international standard developed by ISO/TC 292 Security and resilience. This document defines terms used in security and resilience standards and includes 360 terms and definitions. This edition was published in the beginning of 2021 and replaces the second edition from 2018.





