GBDE, standing for GEOM Based Disk Encryption, is a block device-layer disk encryption system written for FreeBSD, [1] [2] initially introduced in version 5.0. It is based on the GEOM disk framework. GBDE was designed and implemented by Poul-Henning Kamp and Network Associates Inc. (now known as McAfee). [3]
Unlike most disk encryption software, GBDE does not attempt to defeat watermarking attacks through the use of disk encryption-specific modes of operation (see disk encryption theory), but instead generates a random key each time a sector is written. [4] Unlike some alternatives, such as CBC with sector-specific initialization vectors, this approach does not reveal any information to the attacker even if they have access to snapshots of the disk image from different points in time, since encryption keys are never re-used.
The one time sector key is encrypted using a pseudorandom key. This pseudorandom key is derived from the sector number and a static 2048-bit master key with 128 bits of salt. The pseudorandom number generator used for this purpose is called the Cherry Picker. This is not a well established PRNG, but rather one invented for GBDE. This generator may not meet the security levels of standard algorithms, and could be distinguishable from random numbers. [5]
Due to this unique approach, GBDE only supports 128-bit AES. Using a different key for each write also introduces a significant CPU overhead, as most block ciphers use key-specific precomputations, and makes disk updates non-atomic since the keys are written separately from the data. [5] [6] [7] As a result, data loss can occur on unexpected power drops, even when used with journaling file systems. GBDE also has a disk space overhead of about 3% to store the per-sector keys.
To address these shortcomings, a more typical disk encryption solution for FreeBSD, GELI, was written later by Pawel Jakub Dawidek.
A cryptographically secure pseudorandom number generator (CSPRNG) or cryptographic pseudorandom number generator (CPRNG) is a pseudorandom number generator (PRNG) with properties that make it suitable for use in cryptography. It is also loosely known as a cryptographic random number generator (CRNG).
Articles related to cryptography include:
In cryptography, Camellia is a symmetric key block cipher with a block size of 128 bits and key sizes of 128, 192 and 256 bits. It was jointly developed by Mitsubishi Electric and NTT of Japan. The cipher has been approved for use by the ISO/IEC, the European Union's NESSIE project and the Japanese CRYPTREC project. The cipher has security levels and processing abilities comparable to the Advanced Encryption Standard.
In Unix-like operating systems, /dev/random and /dev/urandom are special files that serve as cryptographically secure pseudorandom number generators. They allow access to environmental noise collected from device drivers and other sources. /dev/random typically blocked if there was less entropy available than requested; more recently it usually blocks at startup until sufficient entropy has been gathered, then unblocks permanently. The /dev/urandom device typically was never a blocking device, even if the pseudorandom number generator seed was not fully initialized with entropy since boot. Not all operating systems implement the same methods for /dev/random and /dev/urandom.

Poul-Henning Kamp is a Danish computer software developer known for work on various projects including FreeBSD and Varnish. He currently resides in Slagelse, Denmark.
Disk encryption software is computer security software that protects the confidentiality of data stored on computer media by using disk encryption.
Encryption software is software that uses cryptography to prevent unauthorized access to digital information. Cryptography is used to protect digital information on computers as well as the digital information that is sent to other computers over the Internet.

Random number generation is a process by which, often by means of a random number generator (RNG), a sequence of numbers or symbols that cannot be reasonably predicted better than by random chance is generated. This means that the particular outcome sequence will contain some patterns detectable in hindsight but unpredictable to foresight. True random number generators can be hardware random-number generators (HRNGs), wherein each generation is a function of the current value of a physical environment's attribute that is constantly changing in a manner that is practically impossible to model. This would be in contrast to so-called "random number generations" done by pseudorandom number generators (PRNGs), which generate numbers that only look random but are in fact pre-determined—these generations can be reproduced simply by knowing the state of the PRNG.
Disk encryption is a special case of data at rest protection when the storage medium is a sector-addressable device. This article presents cryptographic aspects of the problem. For an overview, see disk encryption. For discussion of different software packages and hardware devices devoted to this problem, see disk encryption software and disk encryption hardware.
The OpenBSD operating system focuses on security and the development of security features. According to author Michael W. Lucas, OpenBSD "is widely regarded as the most secure operating system available anywhere, under any licensing terms."
Steganographic file systems are a kind of file system first proposed by Ross Anderson, Roger Needham, and Adi Shamir. Their paper proposed two main methods of hiding data: in a series of fixed size files originally consisting of random bits on top of which 'vectors' could be superimposed in such a way as to allow levels of security to decrypt all lower levels but not even know of the existence of any higher levels, or an entire partition is filled with random bits and files hidden in it.

FreeBSD is a free and open-source Unix-like operating system descended from the Berkeley Software Distribution (BSD), which was based on Research Unix. The first version of FreeBSD was released in 1993. In 2005, FreeBSD was the most popular open-source BSD operating system, accounting for more than three-quarters of all installed and permissively licensed BSD systems.
This is a technical feature comparison of different disk encryption software.
dm-crypt is a transparent block device encryption subsystem in Linux kernel versions 2.6 and later and in DragonFly BSD. It is part of the device mapper (dm) infrastructure, and uses cryptographic routines from the kernel's Crypto API. Unlike its predecessor cryptoloop, dm-crypt was designed to support advanced modes of operation, such as XTS, LRW and ESSIV, in order to avoid watermarking attacks. In addition to that, dm-crypt addresses some reliability problems of cryptoloop.
GEOM is the main storage framework for the FreeBSD operating system. It is available in FreeBSD 5.0 and later releases, and provides a standardized way to access storage layers. GEOM is modular and allows for geom modules to connect to the framework. For example, the geom_mirror module provides RAID1 or mirroring functionality to the system. A number of modules are provided as part of FreeBSD and others have been developed independently and are distributed via (e.g.) GitHub.
Data erasure is a software-based method of data sanitization that aims to completely destroy all electronic data residing on a hard disk drive or other digital media by overwriting data onto all sectors of the device in an irreversible process. By overwriting the data on the storage device, the data is rendered irrecoverable.
geli is a block device-layer disk encryption system written for FreeBSD, introduced in version 6.0. It uses the GEOM disk framework. It was designed and implemented by Paweł Jakub Dawidek.
There are various implementations of the Advanced Encryption Standard, also known as Rijndael.
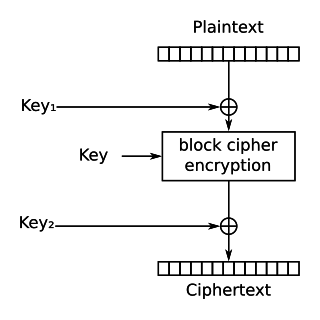
The xor–encrypt–xor (XEX) is a (tweakable) mode of operation of a block cipher. In tweaked-codebook mode with ciphertext stealing, it is one of the more popular modes of operation for whole-disk encryption. XEX is also a common form of key whitening, and part of some smart card proposals.