
Telemetry is the in situ collection of measurements or other data at remote points and their automatic transmission to receiving equipment (telecommunication) for monitoring. The word is derived from the Greek roots tele, 'remote', and metron, 'measure'. Systems that need external instructions and data to operate require the counterpart of telemetry: telecommand.

A barcode or bar code is a method of representing data in a visual, machine-readable form. Initially, barcodes represented data by varying the widths, spacings and sizes of parallel lines. These barcodes, now commonly referred to as linear or one-dimensional (1D), can be scanned by special optical scanners, called barcode readers, of which there are several types. Later, two-dimensional (2D) variants were developed, using rectangles, dots, hexagons and other patterns, called matrix codes or 2D barcodes, although they do not use bars as such. 2D barcodes can be read using purpose-built 2D optical scanners, which exist in a few different forms. 2D barcodes can also be read by a digital camera connected to a microcomputer running software that takes a photographic image of the barcode and analyzes the image to deconstruct and decode the 2D barcode. A mobile device with a built-in camera, such as smartphone, can function as the latter type of 2D barcode reader using specialized application software.
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory goods.

A barcode reader or barcode scanner is an optical scanner that can read printed barcodes, decode the data contained in the barcode to a computer. Like a flatbed scanner, it consists of a light source, a lens and a light sensor for translating optical impulses into electrical signals. Additionally, nearly all barcode readers contain decoder circuitry that can analyse the barcode's image data provided by the sensor and send the barcode's content to the scanner's output port.

A QR code is a type of two-dimensional matrix barcode, invented in 1994, by Japanese company Denso Wave for labelling automobile parts. A barcode is a machine-readable optical image that contains information specific to the labelled item. In practice, QR codes contain data for a locator, an identifier, and web tracking. To efficiently store data, QR codes use four standardized modes of encoding (i) numeric, (ii) alphanumeric, (iii) byte or binary, and (iv) kanji.

A time clock, sometimes known as a clock card machine or punch clock or time recorder, is a device that records start and end times for hourly employees at a place of business.
Object hyperlinking is a term that refers to extending the Internet to objects and locations in the real world. Object hyperlinking aims to extend the Internet to the physical world by attaching tags with URLs to tangible objects or locations. These object tags can then be read by a wireless mobile device and information about objects and locations retrieved and displayed.

Bag tags, also known as baggage tags, baggage checks or luggage tickets, have traditionally been used by bus, train, and airline carriers to route checked luggage to its final destination. The passenger stub is typically handed to the passenger or attached to the ticket envelope:
- to aid the passenger in identifying their bag among similar bags at the destination baggage carousel;
- as proof—still requested at a few airports—that the passenger is not removing someone else's bag from the baggage reclaim hall; and
- as a means for the passenger and carrier to identify and trace a specific bag that has gone astray and was not delivered at the destination. The carriers' liability is restricted to published tariffs and international agreements.

A tracking system, also known as a locating system, is used for the observing of persons or objects on the move and supplying a timely ordered sequence of location data for further processing.
In the distribution and logistics of many types of products, track and trace or tracking and tracing concerns a process of determining the current and past locations of a unique item or property. Mass serialization is the process that manufacturers go through to assign and mark each of their products with a unique identifier such as an Electronic Product Code (EPC) for track and trace purposes. The marking or "tagging" of products is usually completed within the manufacturing process through the use of various combinations of human readable or machine readable technologies such as DataMatrix barcodes or RFID.
Time and attendance systems (T&A) are used to track and monitor when employees start and stop work. A time and attendance system enables an employer to monitor their employees working hours and late arrivals, early departures, time taken on breaks and absenteeism. It also helps to control labor costs by reducing over-payments, which are often caused by paying employees for time that are not working, and eliminates transcription error, interpretation error and intentional error. T&A systems can also be used to ensure compliance with labor regulations regarding proof of attendance.
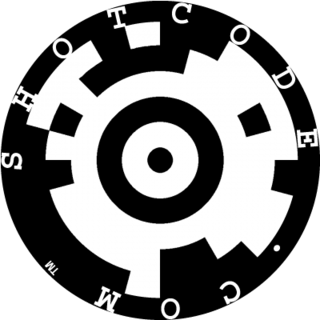
ShotCode is a circular barcode created by High Energy Magic of Cambridge University. It uses a dartboard-like circle, with a bullseye in the centre and datacircles surrounding it. The technology reads databits from these datacircles by measuring the angle and distance from the bullseye for each.

High Capacity Color Barcode (HCCB) is a technology developed by Microsoft for encoding data in a 2D "barcode" using clusters of colored triangles instead of the square pixels conventionally associated with 2D barcodes or QR codes. Data density is increased by using a palette of 4 or 8 colors for the triangles, although HCCB also permits the use of black and white when necessary. It has been licensed by the ISAN International Agency for use in its International Standard Audiovisual Number standard, and serves as the basis for the Microsoft Tag mobile tagging application.

A payment terminal, also known as a point of sale (POS) terminal, credit card machine, PIN pad, EFTPOS terminal, is a device which interfaces with payment cards to make electronic funds transfers. The terminal typically consists of a secure keypad for entering PIN, a screen, a means of capturing information from payments cards and a network connection to access the payment network for authorization.
Mobile tagging is the process of providing data read from tags for display on mobile devices, commonly encoded in a two-dimensional barcode, using the camera of a camera phone as the reader device. The contents of the tag code is usually a URL for information addressed and accessible through Internet.
Touchatag was an RFID service for consumers, application developers and operators/enterprises created by Alcatel-Lucent. Consumers could use RFID tags to trigger what touchatag called Applications, which could include opening a webpage, sending a text message, shutting down the computer, or running a custom application created through the software's API, via the application developer network. Touchatag applications were also compatible with NFC enabled phones like the Nokia 6212. TikiTag was launched as an open beta on October 1, 2008. And it was rebranded to touchatag on February 15, 2009. Touchatag also sold RFID hardware, like a starter package with 1 USB RFID reader and 10 RFID tags (stickers), for which the client software was compatible with Windows XP and Vista, along with Mac OS X 10.4 and up. Touchatag was carried by Amazon.com, ThinkGeek, Firebox.com and getDigital.de along with Touchatag's own Online Store. Touchatag also marketed their products' underlying technology for enterprise and operator solutions. Touchatag announced an agreement with Belgacom PingPing on jointly developing the contactless market and announced a commercial pilot with Accor Services. On June 27, 2012, the Touchatag team has announced the shutdown of the project. inviting users to use IOTOPE "a similar open source Internet Of Things service" which itself has no apparent activity since November 2012.
Asset tracking refers to the method of tracking physical assets, either by scanning barcode labels attached to the assets or by using tags using GPS, BLE, LoRa, or RFID which broadcast their location. These technologies can also be used for indoor tracking of persons wearing a tag.
Inventory management software is a software system for tracking inventory levels, orders, sales and deliveries. It can also be used in the manufacturing industry to create a work order, bill of materials and other production-related documents. Companies use inventory management software to avoid product overstock and outages. It is a tool for organizing inventory data that before was generally stored in hard-copy form or in spreadsheets.
ISO/IEC 20248Automatic Identification and Data Capture Techniques – Data Structures – Digital Signature Meta Structure is an international standard specification under development by ISO/IEC JTC 1/SC 31/WG 2. This development is an extension of SANS 1368, which is the current published specification. ISO/IEC 20248 and SANS 1368 are equivalent standard specifications. SANS 1368 is a South African national standard developed by the South African Bureau of Standards.
Barcode library or Barcode SDK is a software library that can be used to add barcode features to desktop, web, mobile or embedded applications. Barcode library presents sets of subroutines or objects which allow to create barcode images and put them on surfaces or recognize machine-encoded text / data from scanned or captured by camera images with embedded barcodes. The library can support two modes: generation and recognition mode, some libraries support barcode reading and writing in the same way, but some libraries support only one mode.








