
In computing, BIOS is firmware used to provide runtime services for operating systems and programs and to perform hardware initialization during the booting process. The BIOS firmware comes pre-installed on an IBM PC or IBM PC compatible's system board and exists in some UEFI-based systems too as a compatibly support module to maintain compatibility operating systems that do not support UEFI native operation. The name originates from the Basic Input/Output System used in the CP/M operating system in 1975. The BIOS originally proprietary to the IBM PC has been reverse engineered by some companies looking to create compatible systems. The interface of that original system serves as a de facto standard.

Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. By contrast, software that causes harm due to some deficiency is typically described as a software bug. Malware poses serious problems to individuals and businesses on the Internet. According to Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 669,947,865 in 2017, which is twice as many malware variants as in 2016. Cybercrime, which includes malware attacks as well as other crimes committed by computer, was predicted to cost the world economy $6 trillion USD in 2021, and is increasing at a rate of 15% per year.

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.

Brain is the industry standard name for a computer virus that was released in its first form on 19 January 1986, and is considered to be the first computer virus for the IBM Personal Computer and compatibles.
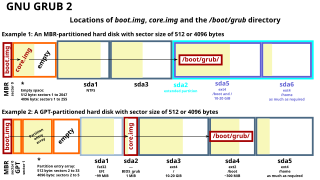
A boot sector is the sector of a persistent data storage device which contains machine code to be loaded into random-access memory (RAM) and then executed by a computer system's built-in firmware.

Antivirus software, also known as anti-malware, is a computer program used to prevent, detect, and remove malware.

CIH, also known as Chernobyl or Spacefiller, is a Microsoft Windows 9x computer virus that first emerged in 1998. Its payload is highly destructive to vulnerable systems, overwriting critical information on infected system drives and, in some cases, destroying the system BIOS. Chen Ing-hau, a student at Tatung University in Taiwan, created the virus. It was believed to have infected sixty million computers internationally, resulting in an estimated US$1 billion in commercial damages.

A live CD is a complete bootable computer installation including operating system which runs directly from a CD-ROM or similar storage device into a computer's memory, rather than loading from a hard disk drive. A live CD allows users to run an operating system for any purpose without installing it or making any changes to the computer's configuration. Live CDs can run on a computer without secondary storage, such as a hard disk drive, or with a corrupted hard disk drive or file system, allowing data recovery.

Elk Cloner is one of the first known microcomputer viruses that spread "in the wild", i.e., outside the computer system or laboratory in which it was written. It attached itself to the Apple II operating system and spread by floppy disk. It was written around 1982 by programmer and entrepreneur Rich Skrenta as a 15-year-old high school student, originally as a joke, and put onto a game disk.
The Michelangelo virus is a computer virus first discovered on 4 February 1991 in Australia. The virus was designed to infect DOS systems, but did not engage the operating system or make any OS calls. Michelangelo, like all boot sector viruses, operated at the BIOS level. Each year, the virus remained dormant until March 6, the birthday of Renaissance artist Michelangelo. There is no reference to the artist in the virus, and it is doubtful that the virus's developer(s) intended a connection between the virus and the artist. The name was chosen by researchers who noticed the coincidence of the activation date. The actual significance of the date to the author is unknown. Michelangelo is a variant of the already endemic Stoned virus.
Jerusalem is a logic bomb DOS virus first detected at Hebrew University of Jerusalem, in October 1987. On infection, the Jerusalem virus becomes memory resident, and then infects every executable file run, except for COMMAND.COM. COM files grow by 1,813 bytes when infected by Jerusalem and are not re-infected. Executable files grow by 1,808 to 1,823 bytes each time they are infected, and are then re-infected each time the files are loaded until they are too large to load into memory. Some .EXE files are infected but do not grow because several overlays follow the genuine .EXE file in the same file. Sometimes .EXE files are incorrectly infected, causing the program to fail to run as soon as it is executed.
OneHalf is a DOS-based polymorphic computer virus discovered in October 1994. It is also known as Slovak Bomber, Freelove or Explosion-II. It infects the master boot record (MBR) of the hard disk, and any files with extensions .COM, .SCR and .EXE. However, it will not infect files that have SCAN, CLEAN, FINDVIRU, GUARD, NOD, VSAFE, MSAV or CHKDSK in the name.

Stoned is a boot sector computer virus created in 1987. It is one of the first viruses and is thought to have been written by a student in Wellington, New Zealand. By 1989 it had spread widely in New Zealand and Australia, and variants became very common worldwide in the early 1990s.

The Ping-Pong virus is a boot sector virus discovered on March 1, 1988, at the Politecnico di Torino in Italy. It was likely the most common and best known boot sector virus until outnumbered by the Stoned virus.
Natas is a computer virus written by James Gentile, a then-18-year-old hacker from San Diego, California who went by the alias of "Little Loc" and later "Priest". The virus was made for a Mexican politician who wanted to win the Mexican elections by affecting all the Mexican Federal Electoral Institute (IFE) computers with a floppy disk.

The MacMag virus, also known by various other names, was a computer virus introduced in 1988 by Richard Brandow, who at the time was editor and publisher of MacMag computer magazine in Montréal.
4k is a computer virus which infects COM files and EXE files. The virus was one of the first file infectors to employ stealth tactics. Infected systems will hang, after September 22 every year, which is also the date of birth of Bilbo Baggins, a character from The Lord of the Rings. The code was intended to display the message Frodo Lives, but hangs in all known variants.
Ambulance or Ambulance Car is a computer virus that infected computers running a DOS operating system in June 1990. It was discovered in Germany.

A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.
Sality is the classification for a family of malicious software (malware), which infects files on Microsoft Windows systems. Sality was first discovered in 2003 and has advanced over the years to become a dynamic, enduring and full-featured form of malicious code. Systems infected with Sality may communicate over a peer-to-peer (P2P) network to form a botnet for the purpose of relaying spam, proxying of communications, exfiltrating sensitive data, compromising web servers and/or coordinating distributed computing tasks for the purpose of processing intensive tasks. Since 2010, certain variants of Sality have also incorporated the use of rootkit functions as part of an ongoing evolution of the malware family. Because of its continued development and capabilities, Sality is considered to be one of the most complex and formidable forms of malware to date.










