Related Research Articles

Industrial espionage, economic espionage, corporate spying, or corporate espionage is a form of espionage conducted for commercial purposes instead of purely national security.
Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types.

The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees.

TEMPEST is a U.S. National Security Agency specification and a NATO certification referring to spying on information systems through leaking emanations, including unintentional radio or electrical signals, sounds, and vibrations. TEMPEST covers both methods to spy upon others and how to shield equipment against such spying. The protection efforts are also known as emission security (EMSEC), which is a subset of communications security (COMSEC).

The Five Eyes (FVEY) is an Anglosphere intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States. These countries are parties to the multilateral UK-USA Agreement, a treaty for joint cooperation in signals intelligence. Informally, Five Eyes can also refer to the group of intelligence agencies of these countries.
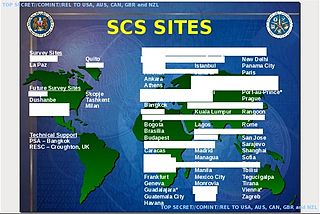
The Special Collection Service (SCS), codenamed F6, is a highly classified joint U.S. Central Intelligence Agency–National Security Agency program charged with inserting eavesdropping equipment in difficult-to-reach places, such as foreign embassies, communications centers, and foreign government installations. Established in the late 1970s and headquartered in Beltsville, Maryland, the SCS has been involved in operations ranging from the Cold War to the Global War on Terrorism.
Signals intelligence by alliances, nations and industries comprises signals intelligence (SIGINT) gathering activities by national and non-national entities; these entities are commonly responsible for communications security (COMSEC) as well.
Cyber spying, cyber espionage, or cyber-collection is the act or practice of obtaining secrets and information without the permission and knowledge of the holder of the information using methods on the Internet, networks or individual computers through the use of proxy servers, cracking techniques and malicious software including Trojan horses and spyware. Cyber espionage can be used to target various actors- individuals, competitors, rivals, groups, governments, and others- in order to obtain personal, economic, political or military advantages. It may wholly be perpetrated online from computer desks of professionals on bases in far away countries or may involve infiltration at home by computer trained conventional spies and moles or in other cases may be the criminal handiwork of amateur malicious hackers and software programmers.
Rohde & Schwarz GmbH & Co KG is an international electronics group specializing in the fields of electronic test equipment, broadcast & media, cybersecurity, radiomonitoring and radiolocation, and radiocommunication. The company provides also products for the wireless communications, electronics industry, aerospace and defense, homeland security and critical infrastructures.

The Office of Tailored Access Operations (TAO), now Computer Network Operations, and structured as S32, is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA). It has been active since at least 1998, possibly 1997, but was not named or structured as TAO until "the last days of 2000," according to General Michael Hayden.

Tempora is the codeword for a formerly-secret computer system that is used by the British Government Communications Headquarters (GCHQ). This system is used to buffer most Internet communications that are extracted from fibre-optic cables, so these can be processed and searched at a later time. It was tested from 2008 and became operational in late 2011.
During the 2010s, international media news reports revealed new operational details about the Anglophone cryptographic agencies' global surveillance of both foreign and domestic nationals. The reports mostly relate to top secret documents leaked by ex-NSA contractor Edward Snowden. The documents consist of intelligence files relating to the U.S. and other Five Eyes countries. In June 2013, the first of Snowden's documents were published, with further selected documents released to various news outlets through the year.
Global mass surveillance can be defined as the mass surveillance of entire populations across national borders.

This timeline of global surveillance disclosures from 2013 to the present day is a chronological list of the global surveillance disclosures that began in 2013. The disclosures have been largely instigated by revelations from the former American National Security Agency contractor Edward Snowden.
TURBINE is the codename of an automated system which enables the United States National Security Agency (NSA) automated management and control of a large surveillance network.
Regin is a sophisticated malware and hacking toolkit used by United States' National Security Agency (NSA) and its British counterpart, the Government Communications Headquarters (GCHQ). It was first publicly revealed by Kaspersky Lab, Symantec, and The Intercept in November 2014. The malware targets specific users of Microsoft Windows-based computers and has been linked to the US intelligence-gathering agency NSA and its British counterpart, the GCHQ. The Intercept provided samples of Regin for download, including malware discovered at a Belgian telecommunications provider, Belgacom. Kaspersky Lab says it first became aware of Regin in spring 2012, but some of the earliest samples date from 2003. Among computers infected worldwide by Regin, 28 percent were in Russia, 24 percent in Saudi Arabia, 9 percent each in Mexico and Ireland, and 5 percent in each of India, Afghanistan, Iran, Belgium, Austria, and Pakistan.
The Equation Group, classified as an advanced persistent threat, is a highly sophisticated threat actor suspected of being tied to the Tailored Access Operations (TAO) unit of the United States National Security Agency (NSA). Kaspersky Labs describes them as one of the most sophisticated cyber attack groups in the world and "the most advanced (...) we have seen", operating alongside the creators of Stuxnet and Flame. Most of their targets have been in Iran, Russia, Pakistan, Afghanistan, India, Syria and Mali.
Zombie Zero is an attack vector where a cyber attacker utilized malware that was clandestinely embedded in new barcode readers which were manufactured overseas.
Hardware backdoors are backdoors in hardware, such as code inside hardware or firmware of computer chips. The backdoors may be directly implemented as hardware Trojans in the integrated circuit.
References
- ↑ John Pike. "Air Interdiction--Focus For The Future". globalsecurity.org.
- ↑ https://fas.org/irp/doddir/dod/jp3_03.pdf [ bare URL PDF ]
- ↑ Australian Government - Department of Immigration and Citizenship Annual report 2009-10 Archived 2014-02-13 at the Wayback Machine Page 152
- ↑ SPIEGEL ONLINE, Hamburg, Germany (29 December 2013). "Catalog Reveals NSA Has Back Doors for Numerous Devices". SPIEGEL ONLINE.
- ↑ Tom's Guide (15 July 2014). "China-Made Handheld Barcode Scanners Ship with Spyware".
- ↑ Supply Chain 24/7 (10 July 2014). "Malware Hidden In Chinese Inventory Scanners Targeting Logistics and Shipping Companies - Supply Chain 24/7".
{{cite web}}: CS1 maint: numeric names: authors list (link)