
Computer security, cybersecurity, or information technology security is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide.
European Strategic Programme on Research in Information Technology (ESPRIT) was a series of integrated programmes of information technology research and development projects and industrial technology transfer measures. It was a European Union initiative managed by the Directorate General for Industry of the European Commission.
The Internet protocol suite, commonly known as TCP/IP, is a framework for organizing the set of communication protocols used in the Internet and similar computer networks according to functional criteria. The foundational protocols in the suite are the Transmission Control Protocol (TCP), the User Datagram Protocol (UDP), and the Internet Protocol (IP). Early versions of this networking model were known as the Department of Defense (DoD) model because the research and development were funded by the United States Department of Defense through DARPA.

The Open Systems Interconnection model is a conceptual model that 'provides a common basis for the coordination of [ISO] standards development for the purpose of systems interconnection'. In the OSI reference model, the communications between a computing system are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application.
The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution.
A virtual private network (VPN) is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet.
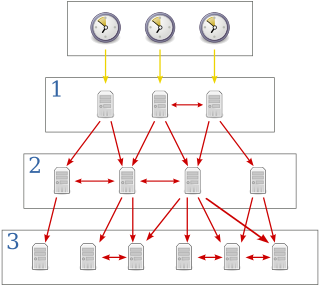
The Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data networks. In operation since before 1985, NTP is one of the oldest Internet protocols in current use. NTP was designed by David L. Mills of the University of Delaware.
An application layer is an abstraction layer that specifies the shared communications protocols and interface methods used by hosts in a communications network. An application layer abstraction is specified in both the Internet Protocol Suite (TCP/IP) and the OSI model. Although both models use the same term for their respective highest-level layer, the detailed definitions and purposes are different.
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible.
QinetiQ is a multinational defence technology company headquartered in Farnborough, Hampshire. It operates primarily in the defence, security and critical national infrastructure markets and run testing and evaluation capabilities for air, land, sea and target systems.
In computing, security-evaluated operating systems have achieved certification from an external security-auditing organization, the most popular evaluations are Common Criteria (CC) and FIPS 140-2.
The ISODE software, more formally the ISO Development Environment, was an implementation of the OSI upper layer protocols, from transport layer to application layer, which was used in the Internet research community to experiment with implementation and deployment of OSI during the late 1980s and early 1990s.

The Department of the Air Force Office of Special Investigations (OSI) is a U.S. federal law enforcement agency that reports directly to the Secretary of the Air Force. OSI is also a U.S. Air Force field operating agency under the administrative guidance and oversight of the Inspector General of the Department of the Air Force. By federal statute, OSI provides independent criminal investigative, counterintelligence and protective service operations worldwide and outside of the traditional military chain of command. Proactively, OSI identifies, investigates, and neutralizes serious criminal, terrorist, and espionage threats to personnel and resources of the Air Force, Space Force, and the U.S. Department of Defense, thereby protecting the national security of the United States.
Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications by allowing them to communicate in a way designed to prevent eavesdropping, tampering, or message forgery. The DTLS protocol is based on the stream-oriented Transport Layer Security (TLS) protocol and is intended to provide similar security guarantees. The DTLS protocol datagram preserves the semantics of the underlying transport—the application does not suffer from the delays associated with stream protocols, but because it uses UDP or SCTP, the application has to deal with packet reordering, loss of datagram and data larger than the size of a datagram network packet. Because DTLS uses UDP or SCTP rather than TCP, it avoids the "TCP meltdown problem", when being used to create a VPN tunnel.

Safelayer Secure Communications S.A. is a Spanish private company founded in May 1999. It develops software products on the public key infrastructure area. Safelayer's technology is part of the three major certification and digital identity projects in Spain: Fábrica Nacional de Moneda y Timbre, the Spanish ID card DNI electrónico and the Spanish E-passport. Safelayer's technology also secures the NATO X400 messaging system.

Rapiscan Systems is an American privately held company that specialises in walk-through metal detectors and X-ray machines for screening airport luggage and cargo. The company is owned by OSI Systems.
Colin Robbins is a network protocol and software engineer credited for research work in distributed directory systems and a co-inventor of LDAP. Educated at Alleyn's School, he holds a BSc, Computer Science & Electronic Engineering, with first class honours, from University College London.
The cyber security community in the United Kingdom is diverse, with many stakeholders groups contributing to support the UK Cyber Security Strategy. The following is a list of some of these stakeholders.
SWIPSY was a firewall toolkit produced by the Defence Evaluation and Research Agency in the UK. The SWIPSY toolkit was an ITSEC E3 evaluated product that allowed additional code to be added to its security ‘compartments’ without affecting the evaluation status of the toolkit itself.
A long-running debate in computer science known as the Protocol Wars occurred from the 1970s to the 1990s when engineers, organizations and nations became polarized over the issue of which communication protocol would result in the best and most robust computer networks. This culminated in the Internet–OSI Standards War in the late 1980s and early 1990s, which was ultimately "won" by the Internet protocol suite ("TCP/IP") by the mid-1990s and has since resulted in most other protocols disappearing.





