Related Research Articles
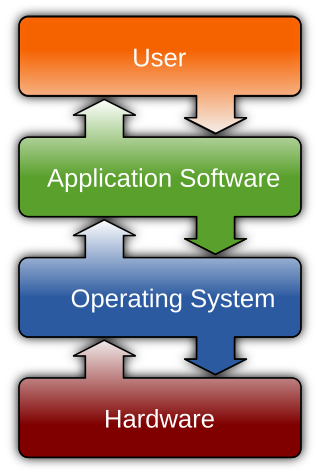
Software is a collection of programs and data that tell a computer how to perform specific tasks. Software often includes associated software documentation. This is in contrast to hardware, from which the system is built and which actually performs the work.

In computing, a database is an organized collection of data or a type of data store based on the use of a database management system (DBMS), the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an application associated with the database.
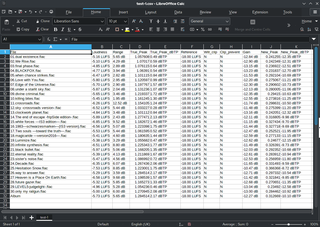
A spreadsheet is a computer application for computation, organization, analysis and storage of data in tabular form. Spreadsheets were developed as computerized analogs of paper accounting worksheets. The program operates on data entered in cells of a table. Each cell may contain either numeric or text data, or the results of formulas that automatically calculate and display a value based on the contents of other cells. The term spreadsheet may also refer to one such electronic document.
A management information system (MIS) is an information system used for decision-making, and for the coordination, control, analysis, and visualization of information in an organization. The study of the management information systems involves people, processes and technology in an organizational context.
An application program is a computer program designed to carry out a specific task other than one relating to the operation of the computer itself, typically to be used by end-users. Word processors, media players, and accounting software are examples. The collective noun "application software" refers to all applications collectively. The other principal classifications of software are system software, relating to the operation of the computer, and utility software ("utilities").

A Laboratory management system (LIMS), sometimes referred to as a laboratory information system (LIS) or laboratory management system (LMS), is a software-based solution with features that support a modern laboratory's operations. Key features include—but are not limited to—workflow and data tracking support, flexible architecture, and data exchange interfaces, which fully "support its use in regulated environments". The features and uses of a LIMS have evolved over the years from simple sample tracking to an enterprise resource planning tool that manages multiple aspects of laboratory informatics.
In computer programming, a software framework is an abstraction in which software, providing generic functionality, can be selectively changed by additional user-written code, thus providing application-specific software. It provides a standard way to build and deploy applications and is a universal, reusable software environment that provides particular functionality as part of a larger software platform to facilitate the development of software applications, products and solutions.
Business software is any software or set of computer programs used by business users to perform various business functions. These business applications are used to increase productivity, measure productivity, and perform other business functions accurately.

An accounting information system (AIS) is a system of collecting, storing and processing financial and accounting data that are used by decision makers. An accounting information system is generally a computer-based method for tracking accounting activity in conjunction with information technology resources. The resulting financial reports can be used internally by management or externally by other interested parties including investors, creditors and tax authorities. Accounting information systems are designed to support all accounting functions and activities including auditing, financial accounting porting, -managerial/ management accounting and tax. The most widely adopted accounting information systems are auditing and financial reporting modules.
Stages-of-growth model is a theoretical model for the growth of information technology (IT) in a business or similar organization. It was developed by Richard L. Nolan during the early 1970s, and with the final version of the model published by him in the Harvard Business Review in 1979.
Write once, compile anywhere (WOCA) is a philosophy taken by a compiler and its associated software libraries or by a software library/software framework which refers to a capability of writing a computer program that can be compiled on all platforms without the need to modify its source code. As opposed to Sun's write once, run anywhere slogan, cross-platform compatibility is implemented only at the source code level, rather than also at the compiled binary code level.
Customised software is software that is developed specifically for some specific organization or other user. As such, it can be contrasted with the use of out-of-the-box software packages developed for the mass market, such as commercial off-the-shelf software, or existing free software.
In business and accounting, information technology controls are specific activities performed by persons or systems designed to ensure that business objectives are met. They are a subset of an enterprise's internal control. IT control objectives relate to the confidentiality, integrity, and availability of data and the overall management of the IT function of the business enterprise. IT controls are often described in two categories: IT general controls (ITGC) and IT application controls. ITGC includes controls over the Information Technology (IT) environment, computer operations, access to programs and data, program development and program changes. IT application controls refer to transaction processing controls, sometimes called "input-processing-output" controls. Information technology controls have been given increased prominence in corporations listed in the United States by the Sarbanes-Oxley Act. The COBIT Framework is a widely used framework promulgated by the IT Governance Institute, which defines a variety of ITGC and application control objectives and recommended evaluation approaches. IT departments in organizations are often led by a chief information officer (CIO), who is responsible for ensuring effective information technology controls are utilized.
Enterprise software, also known as enterprise application software (EAS), is computer software used to satisfy the needs of an organization rather than its individual users. Enterprise software is an integral part of a computer-based information system, handling a number of business operations, for example to enhance business and management reporting tasks, or support production operations and back office functions. Enterprise systems must process information at a relatively high speed.
End-user development (EUD) or end-user programming (EUP) refers to activities and tools that allow end-users – people who are not professional software developers – to program computers. People who are not professional developers can use EUD tools to create or modify software artifacts and complex data objects without significant knowledge of a programming language. In 2005 it was estimated that by 2012 there would be more than 55 million end-user developers in the United States, compared with fewer than 3 million professional programmers. Various EUD approaches exist, and it is an active research topic within the field of computer science and human-computer interaction. Examples include natural language programming, spreadsheets, scripting languages, visual programming, trigger-action programming and programming by example.
IT Application Portfolio Management (APM) is a practice that has emerged in mid to large-size information technology (IT) organizations since the mid-1990s. Application Portfolio Management attempts to use the lessons of financial portfolio management to justify and measure the financial benefits of each application in comparison to the costs of the application's maintenance and operations.

Accounting software is a computer program that maintains account books on computers, including recording transactions and account balances. It may depends on virtual thinking. Depending on the purpose, the software can manage budgets, perform accounting tasks for multiple currencies, perform payroll and customer relationship management, and prepare financial reporting. Work to have accounting functions be implemented on computers goes back to the earliest days of electronic data processing. Over time, accounting software has revolutionized from supporting basic accounting operations to performing real-time accounting and supporting financial processing and reporting. Cloud accounting software was first introduced in 2011, and it allowed the performance of all accounting functions through the internet.
In big organizations, shadow IT refers to information technology (IT) systems deployed by departments other than the central IT department, to bypass limitations and restrictions that have been imposed by central information systems. While it can promote innovation and productivity, shadow IT introduces security risks and compliance concerns, especially when such systems are not aligned with corporate governance.
GrapeCity, inc. is a privately held, multinational software corporation based in Sendai, Japan, that develops software products and provides outsourced product development services, consulting services, software, and Customer relationship management services. GrapeCity also has established WINEstudios, a media design and digital production facility in Japan.
Customer data management (CDM) is the ways in which businesses keep track of their customer information and survey their customer base in order to obtain feedback. CDM includes a range of software or cloud computing applications designed to give large organizations rapid and efficient access to customer data. Surveys and data can be centrally located and widely accessible within a company, as opposed to being warehoused in separate departments. CDM encompasses the collection, analysis, organizing, reporting and sharing of customer information throughout an organization. Businesses need a thorough understanding of their customers’ needs if they are to retain and increase their customer base. Efficient CDM solutions provide companies with the ability to deal instantly with customer issues and obtain immediate feedback. As a result, customer retention and customer satisfaction can show marked improvement. According to a study by Aberdeen Group, "above-average and best-in-class companies... attain greater than 20% annual improvement in retention rates, revenues, data accuracy and partner/customer satisfaction rates."