Related Research Articles

Microsoft Corporation is an American multinational corporation and technology company headquartered in Redmond, Washington. Microsoft's best-known software products are the Windows line of operating systems, the Microsoft 365 suite of productivity applications, and the Edge web browser. Its flagship hardware products are the Xbox video game consoles and the Microsoft Surface lineup of touchscreen personal computers. Microsoft ranked No. 14 in the 2022 Fortune 500 rankings of the largest United States corporations by total revenue; and it was the world's largest software maker by revenue in 2022 according to Forbes Global 2000. It is considered one of the Big Five American information technology companies, alongside Alphabet, Amazon, Apple, and Meta.
Trusted Computing (TC) is a technology developed and promoted by the Trusted Computing Group. The term is taken from the field of trusted systems and has a specialized meaning that is distinct from the field of confidential computing. With Trusted Computing, the computer will consistently behave in expected ways, and those behaviors will be enforced by computer hardware and software. Enforcing this behavior is achieved by loading the hardware with a unique encryption key that is inaccessible to the rest of the system and the owner.

The Next-Generation Secure Computing Base is a software architecture designed by Microsoft which claimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed platforms such as set-top boxes while simultaneously preserving the backward compatibility, flexibility, and openness of the Windows operating system. Microsoft's primary stated objective with NGSCB was to "protect software from software."

Craig James Mundie is an American businessperson. In 1982, he co-founded Alliant Computer Systems, becoming CEO. He was later Senior Advisor to the CEO at Microsoft, after being Microsoft's Chief Research and Strategy Officer from 2006 to 2012. He retired from Microsoft in 2014. During the Obama administration, he was a member of his President's Council of Advisors on Science and Technology (PCAST).

MSN TV was a web access product consisting of a thin client device that used a television for display, and the online service that supported it. The original WebTV device design and service were developed by WebTV Networks, Inc., a company started in 1995. The WebTV product was announced in July 1996 and later released on September 18, 1996. In April 1997, the company was purchased by Microsoft Corporation and in July 2001, was rebranded to MSN TV and absorbed into MSN.
The Windows Hardware Engineering Community (WinHEC) is a series of technical conferences and workshops, where Microsoft elaborates on its hardware plans for Windows devices.
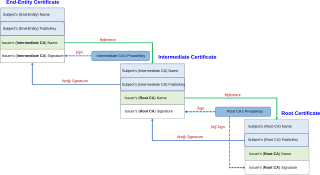
In cryptography and computer security, a root certificate is a public key certificate that identifies a root certificate authority (CA). Root certificates are self-signed and form the basis of an X.509-based public key infrastructure (PKI). Either it has matched Authority Key Identifier with Subject Key Identifier, in some cases there is no Authority Key identifier, then Issuer string should match with Subject string. For instance, the PKIs supporting HTTPS for secure web browsing and electronic signature schemes depend on a set of root certificates.

Cairo was the codename for a project at Microsoft from 1991 to 1996. Its charter was to build technologies for a next-generation operating system that would fulfill Bill Gates's vision of "information at your fingertips." Cairo never shipped, although portions of its technologies have since appeared in other products.
Microsoft Research (MSR) is the research subsidiary of Microsoft. It was created in 1991 by Richard Rashid, Bill Gates and Nathan Myhrvold with the intent to advance state-of-the-art computing and solve difficult world problems through technological innovation in collaboration with academic, government, and industry researchers. The Microsoft Research team has more than 1,000 computer scientists, physicists, engineers, and mathematicians, including Turing Award winners, Fields Medal winners, MacArthur Fellows, and Dijkstra Prize winners.

PSINet was an American internet service provider based in Northern Virginia. As one of the first commercial Internet service providers (ISPs), it was involved in the commercialization of the Internet until the company's bankruptcy in 2001 during the dot-com bubble and acquisition by Cogent Communications in 2002.

Internet governance consists of a system of laws, rules, policies and practices that dictate how its board members manage and oversee the affairs of any internet related-regulatory body. This article describes how the Internet was and is currently governed, some inherent controversies, and ongoing debates regarding how and why the Internet should or should not be governed in future.
The OpenNet Initiative (ONI) was a joint project whose goal was to monitor and report on internet filtering and surveillance practices by nations. Started in 2002, the project employed a number of technical means, as well as an international network of investigators, to determine the extent and nature of government-run internet filtering programs. Participating academic institutions included the Citizen Lab at the Munk Centre for International Studies, University of Toronto; Berkman Center for Internet & Society at Harvard Law School; the Oxford Internet Institute (OII) at University of Oxford; and, The SecDev Group, which took over from the Advanced Network Research Group at the Cambridge Security Programme, University of Cambridge.
Steven McGeady is a former Intel executive best known as a witness in the Microsoft antitrust trial. His notes and testimony contained colorful quotes by Microsoft executives threatening to "cut off Netscape's air supply" and Bill Gates' guess that "this antitrust thing will blow over". Attorney David Boies said that McGeady's testimony showed him to be "an extremely conscientious, capable and honest witness", while Microsoft portrayed him as someone with an "axe to grind". McGeady left Intel in 2000, but later again gained notoriety for defending his former employee Mike Hawash after his arrest on federal terrorism charges. From its founding in 2002 until its sale in November 2013, he was Chairman of Portland-based healthcare technology firm ShiftWise. He is a member of the Reed College Board of Trustees, the Portland Art Museum Board of Trustees, and the PNCA Board of Governors, and lives in Portland, Oregon.
Criticism of Windows XP deals with issues with security, performance and the presence of product activation errors that are specific to the Microsoft operating system Windows XP.
Microsoft is a multinational computer technology corporation. Microsoft was founded on April 4, 1975, by Bill Gates and Paul Allen in Albuquerque, New Mexico. Its current best-selling products are the Microsoft Windows operating system; Microsoft Office, a suite of productivity software; Xbox, a line of entertainment of games, music, and video; Bing, a line of search engines; and Microsoft Azure, a cloud services platform.
Collaboration Oriented Architecture (COA) is a computer system that is designed to collaborate, or use services, from systems that are outside of the operators control. Collaboration Oriented Architecture will often use Service Oriented Architecture to deliver the technical framework.
Fred Barry Schneider is an American computer scientist, based at Cornell University, where he is the Samuel B. Eckert Professor of Computer Science. He has published in numerous areas including science policy, cybersecurity, and distributed systems. His research is in the area of concurrent and distributed systems for high-integrity and mission-critical applications.
Advanced Network and Services, Inc. (ANS) was a United States non-profit organization formed in September, 1990 by the NSFNET partners to run the network infrastructure for the soon to be upgraded NSFNET Backbone Service. ANS was incorporated in the State of New York and had offices in Armonk and Poughkeepsie, New York.
Control-Alt-Delete is a computer keyboard command on IBM PC compatible computers, invoked by pressing the Delete key while holding the Control and Alt keys: Ctrl+Alt+Delete. The function of the key combination differs depending on the context but it generally interrupts or facilitates interrupting a function. For instance, in pre-boot environment or in MS-DOS, Windows 3.0 and earlier versions of Windows or OS/2, the key combination reboots the computer. Starting with Windows 95, the key combination invokes a task manager or security related component that facilitates ending a Windows session or killing a frozen application.
FREAK is a security exploit of a cryptographic weakness in the SSL/TLS protocols introduced decades earlier for compliance with U.S. cryptography export regulations. These involved limiting exportable software to use only public key pairs with RSA moduli of 512 bits or fewer, with the intention of allowing them to be broken easily by the National Security Agency (NSA), but not by other organizations with lesser computing resources. However, by the early 2010s, increases in computing power meant that they could be broken by anyone with access to relatively modest computing resources using the well-known Number Field Sieve algorithm, using as little as $100 of cloud computing services. Combined with the ability of a man-in-the-middle attack to manipulate the initial cipher suite negotiation between the endpoints in the connection and the fact that the finished hash only depended on the master secret, this meant that a man-in-the-middle attack with only a modest amount of computation could break the security of any website that allowed the use of 512-bit export-grade keys. While the exploit was only discovered in 2015, its underlying vulnerabilities had been present for many years, dating back to the 1990s.
References
- ↑ OGC-00-33R Department of Commerce: Relationship with the Internet Corporation for Assigned Names and Numbers (PDF). Government Accountability Office. July 7, 2000. p. 6. Archived (PDF) from the original on June 15, 2009. Retrieved June 25, 2015.
- ↑ Management of NSFNET Archived 2013-07-28 at the Wayback Machine , a transcript of the March 12, 1992 hearing before the Subcommittee on Science of the Committee on Science, Space, and Technology, U.S. House of Representatives, One Hundred Second Congress, Second Session, Hon. Rick Boucher, subcommittee chairman, presiding.
- ↑ Susan R. Harris; Elise Gerich (April 1996). "Retiring the NSFNET Backbone Service: Chronicling the End of an Era". ConneXions. 10 (4). Archived from the original on 2015-03-17.
- ↑ "A Brief History of the Internet". Archived from the original on 2015-08-11. Retrieved 2015-06-25.
- ↑ Gates, Bill – The Internet Tidal Wave Archived 2009-07-15 at the Wayback Machine . Microsoft, May 26, 1995. Made publicly available at United States Department of Justice. United States v. Microsoft Trial Exhibits.
- ↑ "Microsoft – The History of Internet Explorer". Microsoft . Archived from the original on 2005-10-01. Retrieved 2007-02-06.
- ↑ "A Brief History of Microsoft on the Web" Archived 2008-05-14 at the Wayback Machine , Dave Cramer, Microsoft.com.
- ↑ "MSN Historical Time line". Microsoft . Archived from the original on 2005-06-18. Retrieved 2006-07-03.
- ↑ "Trust in Cyberspace" Archived 2016-03-04 at the Wayback Machine , 1999, final report of the "Committee on Information System Trustworthiness".
- ↑ "Subject: Trustworthy computing" Archived 2015-06-26 at the Wayback Machine , From: Bill Gates Sent: Tuesday, January 15, 2002, wired.com.
- 1 2 "Trustworthy Computing, Microsoft White Paper" Archived 2015-06-26 at the Wayback Machine , (revised October 2002 version), Microsoft.com.
- ↑ "Era Ends With Break Up of Trustworthy Computing Group at Microsoft" Archived 2015-06-26 at the Wayback Machine , September 19, 2014, Dennis Fisher, Threatpost.com.
- ↑ "10 years ago today: Bill Gates kicks arse over security" Archived 2015-06-26 at the Wayback Machine , January 15, 2012, John Leyden, The Register.
- ↑ Tony Bradley (March 5, 2014). "The Business World Owes A Lot To Microsoft Trustworthy Computing". Forbes.com. Archived from the original on July 29, 2017. Retrieved December 2, 2017.
- ↑ Osterman [MSFT], Larry (21 October 2005). "Why no Easter Eggs? – Larry Osterman's WebLog". blogs.msdn.microsoft.com.