
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on exploiting the advantages of exponential growth, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer.
Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types.

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
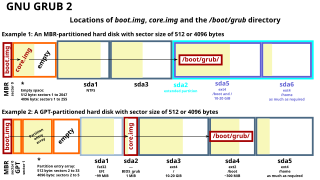
A boot sector is the sector of a persistent data storage device which contains machine code to be loaded into random-access memory (RAM) and then executed by a computer system's built-in firmware.

Antivirus software, also known as anti-malware, is a computer program used to prevent, detect, and remove malware.

A COM file is a type of simple executable file. On the Digital Equipment Corporation (DEC) VAX operating systems of the 1970s, .COM was used as a filename extension for text files containing commands to be issued to the operating system. With the introduction of Digital Research's CP/M, the type of files commonly associated with COM extension changed to that of executable files. This convention was later carried over to DOS. Even when complemented by the more general EXE file format for executables, the compact COM files remained viable and frequently used under DOS.
The EICAR Anti-Virus Test File or EICAR test file is a computer file that was developed by the European Institute for Computer Antivirus Research (EICAR) and Computer Antivirus Research Organization (CARO) to test the response of computer antivirus (AV) programs. Instead of using real malware, which could cause real damage, this test file allows people to test anti-virus software without having to use a real computer virus.
Abraxas, also known as Abraxas5, discovered in April 1993, is an encrypted, overwriting, file infecting computer virus which infects .COM and .EXE files, although it does not infect command.com. It does not become memory resident. Each time an infected file is executed, Abraxas infects the copy of dosshell.com located in the C:\DOS directory, as well as one EXE file in the current directory. Due to a bug in the virus, only the first EXE file in any directory is infected.
Acme is a computer virus which infects MS-DOS EXE files. Each time an infected file is executed, Acme may infect an EXE in the current directory by creating a hidden 247 byte long read-only COM file with the same base name. Acme is a variant of Clonewar, a spawning virus. Acme is also perhaps a descendant of the small single-step infector Zeno, which is not to be confused with the Zeno programming language.
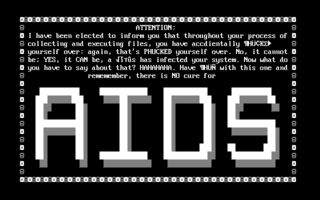
AIDS is a DOS computer virus which overwrites COM files.
Mobile malware is malicious software that targets mobile phones or wireless-enabled Personal digital assistants (PDA), by causing the collapse of the system and loss or leakage of confidential information. As wireless phones and PDA networks have become more and more common and have grown in complexity, it has become increasingly difficult to ensure their safety and security against electronic attacks in the form of viruses or other malware.
Jerusalem is a logic bomb DOS virus first detected at Hebrew University of Jerusalem, in October 1987. On infection, the Jerusalem virus becomes memory resident, and then infects every executable file run, except for COMMAND.COM. COM files grow by 1,813 bytes when infected by Jerusalem and are not re-infected. Executable files grow by 1,808 to 1,823 bytes each time they are infected, and are then re-infected each time the files are loaded until they are too large to load into memory. Some .EXE files are infected but do not grow because several overlays follow the genuine .EXE file in the same file. Sometimes .EXE files are incorrectly infected, causing the program to fail to run as soon as it is executed.
Ontario is a family of computer viruses, named after its point of isolation, the Canadian province of Ontario. This family of computer virus consists of Ontario.1024, Ontario.512 and Ontario.2048. The first variant Ontario.512 was discovered in July 1990. Because Ontario.1024 was also discovered in Ontario, it is likely that both viruses originate from within the province. By the Ontario.2048 variant, the author had adopted "Ontario" as the family's name and even included the name "Ontario-3" in the virus code.
CTX is a computer virus created in Spain in 1999. CTX was initially discovered as part of the Cholera worm, with which the author intentionally infected with CTX. Although the Cholera worm had the capability to send itself via email, the CTX worm quickly surpassed it in prevalence. Cholera is now considered obsolete, while CTX remains in the field, albeit with only rare discoveries.

Stoned is a boot sector computer virus created in 1987. It is one of the first viruses and is thought to have been written by a student in Wellington, New Zealand. By 1989 it had spread widely in New Zealand and Australia, and variants became very common worldwide in the early 1990s.
4k is a computer virus which infects COM files and EXE files. The virus was one of the first file infectors to employ stealth tactics. Infected systems will hang, after September 22 every year, which is also the date of birth of Bilbo Baggins, a character from The Lord of the Rings. The code was intended to display the message Frodo Lives, but hangs in all known variants.

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.
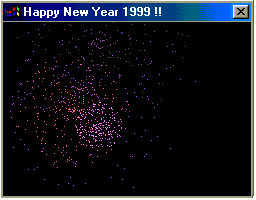
Happy99 is a computer worm for Microsoft Windows. It first appeared in mid-January 1999, spreading through email and usenet. The worm installs itself and runs in the background of a victim's machine, without their knowledge. It is generally considered the first virus to propagate by email, and has served as a template for the creation of other self-propagating viruses. Happy99 has spread on multiple continents, including North America, Europe, and Asia.
MS Antivirus is a scareware rogue anti-virus which purports to remove virus infections found on a computer running Microsoft Windows. It attempts to scam the user into purchasing a "full version" of the software. The company and the individuals behind Bakasoftware operated under other different 'company' names, including Innovagest2000, Innovative Marketing Ukraine, Pandora Software, LocusSoftware, etc.

Locky is ransomware malware released in 2016. It is delivered by email with an attached Microsoft Word document that contains malicious macros. When the user opens the document, it appears to be full of gibberish, and includes the phrase "Enable macro if data encoding is incorrect," a social engineering technique. If the user does enable macros, they save and run a binary file that downloads the actual encryption Trojan, which will encrypt all files that match particular extensions. Filenames are converted to a unique 16 letter and number combination. Initially, only the .locky file extension was used for these encrypted files. Subsequently, other file extensions have been used, including .zepto, .odin, .aesir, .thor, and .zzzzz. After encryption, a message instructs them to download the Tor browser and visit a specific criminal-operated Web site for further information.







