
Closed-circuit television (CCTV), also known as video surveillance, is the use of video cameras to transmit a signal to a specific place, on a limited set of monitors. It differs from broadcast television in that the signal is not openly transmitted, though it may employ point-to-point (P2P), point-to-multipoint (P2MP), or mesh wired or wireless links. Even though almost all video cameras fit this definition, the term is most often applied to those used for surveillance in areas that require additional security or ongoing monitoring.

Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception.
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored.

Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, such as organizations like the NSA, but it may also be carried out by corporations. Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is also often distinguished from targeted surveillance.

A janitor, also known as a janny, custodian, porter, cleanser, cleaner or caretaker, is a person who cleans and maintains buildings. In some cases, they will also carry out maintenance and security duties. A similar position, but usually with more managerial duties and not including cleaning, is occupied by building superintendents in the United States and Canada and by site managers in schools in the United Kingdom. Cleaning is one of the most commonly outsourced services.

A cubicle is a partially enclosed office workspace that is separated from neighboring workspaces by partitions that are usually 5–6 feet (1.5–1.8 m) tall. Its purpose is to isolate office workers and managers from the sights and noises of an open workspace so that they may concentrate with fewer distractions. Cubicles are composed of modular elements such as walls, work surfaces, overhead bins, drawers, and shelving, which can be configured depending on the user's needs. Installation is generally performed by trained personnel, although some cubicles allow configuration changes to be performed by users without specific training.
The office of the future is a collection of ideas for redesigning the office. As technology and society have evolved, the definition of the office of the future has changed. Current concepts, dating from the 1940s, are now known as the "paperless office".

The Office Assistant is a discontinued intelligent user interface for Microsoft Office that assisted users by way of an interactive animated character which interfaced with the Office help content. It was included in Microsoft Office for Windows, in Microsoft Publisher and Microsoft Project, Microsoft FrontPage, and Microsoft Office for Mac. The Office Assistant used technology initially from Microsoft Bob and later Microsoft Agent, offering advice based on Bayesian algorithms.

The computer desk and related ergonomic desk are furniture pieces designed to comfortably and aesthetically provide a working surface and house or conceal office equipment including computers, peripherals and cabling for office and home-office users.

Carnivore, later renamed DCS1000, was a system implemented by the Federal Bureau of Investigation (FBI) that was designed to monitor email and electronic communications. It used a customizable packet sniffer that could monitor all of a target user's Internet traffic. Carnivore was implemented in October 1997. By 2005 it had been replaced with improved commercial software.
Surveillance abuse is the use of surveillance methods or technology to monitor the activity of an individual or group of individuals in a way which violates the social norms or laws of a society.

Computer rage refers to negative psychological responses towards a computer due to heightened anger or frustration. Examples of computer rage include cursing or yelling at a computer, slamming or throwing a keyboard or a mouse, and assaulting the computer or monitor with an object or weapon.
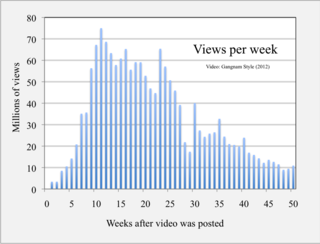
A viral video is a video that becomes popular through a viral process of Internet sharing, typically through video sharing websites such as YouTube as well as social media and email. For a video to be shareable or spreadable, it must focus on the social logics and cultural practices that have enabled and popularized these new platforms.
Verint Systems is a Melville, New York–based analytics company which was founded in 2002. The company sells software and hardware products for customer engagement management and business intelligence. Their products are designed to assist clients in data analysis, specifically large data sets.
A computer virus hoax is a message warning the recipients of a non-existent computer virus threat. The message is usually a chain e-mail that tells the recipients to forward it to everyone they know, but it can also be in the form of a pop-up window.

IvanAnywhere is a simple, remote-controlled telepresence robot created by Sybase iAnywhere programmers to enable their co-worker, Ivan Bowman, to efficiently remote work. The robot enables Bowman to be virtually present at conferences and presentations, and to discuss product development with other developers face-to-face. IvanAnywhere is powered by SAP's mobile database product, SQL Anywhere.
Employee monitoring is the surveillance of workers' activity. Organizations engage in employee monitoring for different reasons such as to track performance, to avoid legal liability, to protect trade secrets, and to address other security concerns. This practice may impact employee satisfaction due to its impact on the employee's privacy. Among organizations, the extent and methods of employee monitoring differ.
Viral phenomena or viral sensation are objects or patterns that are able to replicate themselves or convert other objects into copies of themselves when these objects are exposed to them. Analogous to the way in which viruses propagate, the term viral pertains to a video, image, or written content spreading to numerous online users within a short time period. This concept has become a common way to describe how thoughts, information, and trends move into and through a human population.
Corporate surveillance describes the practice of businesses monitoring and extracting information from their users, clients, or staff. This information may consist of online browsing history, email correspondence, phone calls, location data, and other private details. Acts of corporate surveillance frequently look to boost results, detect potential security problems, or adjust advertising strategies. These practices have been criticized for violating ethical standards and invading personal privacy. Critics and privacy activists have called for businesses to incorporate rules and transparency surrounding their monitoring methods to ensure they are not misusing their position of authority or breaching regulatory standards.
Storyful is a social media intelligence agency headquartered in Dublin, Ireland that is a subsidiary of Rupert Murdoch's News Corp offering services such as social news monitoring, video licensing, and reputation risk management tools for corporate clients. The startup was launched as the first social media newswire, a content aggregator, verifying news sources and online content in Dublin in 2010 by Mark Little, a former journalist with RTÉ News. Storyful was acquired by Rupert Murdoch’s News Corp in 2013 for USD$25 million.










