Related Research Articles

Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception.
A covert listening device, more commonly known as a bug or a wire, is usually a combination of a miniature radio transmitter with a microphone. The use of bugs, called bugging, or wiretapping is a common technique in surveillance, espionage and police investigations.
Wiretapping, also known as wire tapping or telephone tapping, is the monitoring of telephone and Internet-based conversations by a third party, often by covert means. The wire tap received its name because, historically, the monitoring connection was an actual electrical tap on an analog telephone or telegraph line. Legal wiretapping by a government agency is also called lawful interception. Passive wiretapping monitors or records the traffic, while active wiretapping alters or otherwise affects it.
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored.
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, such as organizations like the NSA, but it may also be carried out by corporations. Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is also often distinguished from targeted surveillance.

The Clipper chip was a chipset that was developed and promoted by the United States National Security Agency (NSA) as an encryption device that secured "voice and data messages" with a built-in backdoor that was intended to "allow Federal, State, and local law enforcement officials the ability to decode intercepted voice and data transmissions." It was intended to be adopted by telecommunications companies for voice transmission. Introduced in 1993, it was entirely defunct by 1996.

A cell site, cell phone tower, cell base tower, or cellular base station is a cellular-enabled mobile device site where antennas and electronic communications equipment are placed to create a cell, or adjacent cells, in a cellular network. The raised structure typically supports antenna and one or more sets of transmitter/receivers transceivers, digital signal processors, control electronics, a GPS receiver for timing, primary and backup electrical power sources, and sheltering.
Secure communication is when two entities are communicating and do not want a third party to listen in. For this to be the case, the entities need to communicate in a way that is unsusceptible to eavesdropping or interception. Secure communication includes means by which people can share information with varying degrees of certainty that third parties cannot intercept what is said. Other than spoken face-to-face communication with no possible eavesdropper, it is probable that no communication is guaranteed to be secure in this sense, although practical obstacles such as legislation, resources, technical issues, and the sheer volume of communication serve to limit surveillance.
Harris Corporation was an American technology company, defense contractor, and information technology services provider that produced wireless equipment, tactical radios, electronic systems, night vision equipment and both terrestrial and spaceborne antennas for use in the government, defense, emergency service, and commercial sectors. They specialized in surveillance solutions, microwave weaponry, and electronic warfare. In 2019, it merged with L3 Technologies to form L3Harris Technologies.
Surveillance abuse is the use of surveillance methods or technology to monitor the activity of an individual or group of individuals in a way which violates the social norms or laws of a society.

Mobile phone tracking is a process for identifying the location of a mobile phone, whether stationary or moving. Localization may be affected by a number of technologies, such as the multilateration of radio signals between (several) cell towers of the network and the phone or by simply using GNSS. To locate a mobile phone using multilateration of mobile radio signals, the phone must emit at least the idle signal to contact nearby antenna towers and does not require an active call. The Global System for Mobile Communications (GSM) is based on the phone's signal strength to nearby antenna masts.
An international mobile subscriber identity-catcher, or IMSI-catcher, is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking location data of mobile phone users. Essentially a "fake" mobile tower acting between the target mobile phone and the service provider's real towers, it is considered a man-in-the-middle (MITM) attack. The 3G wireless standard offers some risk mitigation due to mutual authentication required from both the handset and the network. However, sophisticated attacks may be able to downgrade 3G and LTE to non-LTE network services which do not require mutual authentication.
Triggerfish describes a technology of cell phone interception and surveillance using a mobile cellular base station. The devices are also known as cell-site simulators or digital analyzers.

The StingRay is an IMSI-catcher, a cellular phone surveillance device, manufactured by Harris Corporation. Initially developed for the military and intelligence community, the StingRay and similar Harris devices are in widespread use by local and state law enforcement agencies across Canada, the United States, and in the United Kingdom. Stingray has also become a generic name to describe these kinds of devices.
During the 2010s, international media news reports revealed new operational details about the Anglophone cryptographic agencies' global surveillance of both foreign and domestic nationals. The reports mostly relate to top secret documents leaked by ex-NSA contractor Edward Snowden. The documents consist of intelligence files relating to the U.S. and other Five Eyes countries. In June 2013, the first of Snowden's documents were published, with further selected documents released to various news outlets through the year.
Global mass surveillance can be defined as the mass surveillance of entire populations across national borders.
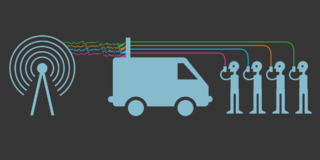
Cellphone surveillance may involve tracking, bugging, monitoring, eavesdropping, and recording conversations and text messages on mobile phones. It also encompasses the monitoring of people's movements, which can be tracked using mobile phone signals when phones are turned on.
Catherine Crump is an American law professor and civil liberties expert focused on the effects of digital surveillance technology on privacy and free speech. She is the Director of the Samuelson Law, Technology and Public Policy Clinic, Co-Director of Berkeley Center for Law and Technology, and a Clinical Professor of Law at the UC Berkeley School of Law. Crump's expertise on digital data collection and the law is regularly featured in the media. In 2023, Crump served as a senior policy advisor for criminal justice for the White House Domestic Policy Council.
The use of stingrays by United States law enforcement is an investigative technique used by both federal and local law enforcement in the United States to obtain information from cell phones by mimicking a cell phone tower. The devices which accomplish this are generically known as IMSI-catchers, but are commonly called stingrays, a brand sold by the Harris Corporation.
Carpenter v. United States, 585 U.S. ___, 138 S.Ct. 2206 (2018), is a landmark United States Supreme Court case concerning the privacy of historical cell site location information (CSLI). The Court held that the government violates the Fourth Amendment to the United States Constitution when it accesses historical CSLI records containing the physical locations of cellphones without a search warrant.
References
- 1 2 3 4 5 6 7 The Boeing Company (11 June 2010). "Technical Approaches to Preventing Contraband Cell Phone Use in Prisons;Docket No. 100504212-0212-01" (PDF). National Telecommunications and Information Administration. p. 7. Archived (PDF) from the original on 19 October 2011. Retrieved 16 November 2014.
- ↑ "DRT Products". Digital Receiver Technology, Inc. n.d. Retrieved 16 November 2014.
- 1 2 3 4 5 6 7 8 Devlin Barrett (13 November 2014). "Americans' Cellphones Targeted in Secret U.S. Spy Program". The Wall Street Journal. Dow Jones & Company. Retrieved 14 November 2014.
- 1 2 3 4 5 6 Winston, Ali (2015-08-07). "Chicago and Los Angeles have used 'dirt box' surveillance for a decade". Revealnews, Center of Investigative Reporting. Retrieved 26 April 2016.
- ↑ Kim Zetter (14 November 2014). "The Feds Are Now Using 'Stingrays' in Planes to Spy on Our Phone Calls". Wired. Condé Nast. Retrieved 16 November 2014.
- ↑ Iain Thomson (14 November 2014). "US Marshals commit DIRTBOX INTRUSION on Americans, says report". The Register. Situation Publishing. Retrieved 16 November 2014.
- ↑ Devlin Barrett (21 November 2014). "U.S. Marshals Service Personnel Dressed as Mexican Marines Pursue Cartel Bosses". The Wall Street Journal. Retrieved 21 November 2014.
- ↑ P/K (27 November 2013). "DRTBOX and the DRT surveillance systems". Top Level Telecommunications. electrospaces.net. Retrieved 16 November 2014.
- ↑ Stephanie K. Pell; Christopher Soghoian (May 15, 2014). "Your Secret Stingray's No Secret Anymore: The Vanishing Government Monopoly Over Cell Phone Surveillance and Its Impact on National Security and Consumer Privacy". Harvard Journal of Law & Technology. Social Science Electronic Publishing, Inc. 28 (1): 67. SSRN 2437678.
- ↑ Jacques Follorou, Glenn Greenwald (21 October 2013). "France in the NSA's crosshair : phone networks under surveillance". Le Monde.fr. Le Monde. Retrieved 27 May 2016.
- ↑ FedBizOpps (2 April 2007). "59 -- Portable Receiving System". FedBizOpps.gov. Retrieved 17 November 2014.
- 1 2 3 Devlin Barrett and Gautham Nagesh (14 November 2014). "U.S. Defends Marshals in Wake of Secret Cellphone Spying Report". The Wall Street Journal. Dow Jones Co. Retrieved 16 November 2014.
- ↑ Staff (January 02, 2015) "Senate wants more answers from feds about fake cell towers, other devices that collect smartphone data" Fox News, retrieved 26 April 2016
- ↑ Mark Weinstein (16 November 2014). "U.S. Marshals and Their "Dirtbox" Declare the 4th Amendment Dead". The Huffington Post. Retrieved 16 November 2014.
- ↑ Megan Geuss (13 November 2014). "Feds gather phone data from the sky with aircraft mimicking cell towers". Ars Technica. Condé Nast. Retrieved 16 November 2014.
- ↑ Spencer Ackerman; Dominic Rushe; Paul Lewis (14 November 2014). "US government planes mimic cellphone towers to collect user data – report". The Guardian. Retrieved 16 November 2014.