Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991.

In cryptography, CAST-128 is a symmetric-key block cipher used in a number of products, notably as the default cipher in some versions of GPG and PGP. It has also been approved for Government of Canada use by the Communications Security Establishment. The algorithm was created in 1996 by Carlisle Adams and Stafford Tavares using the CAST design procedure.
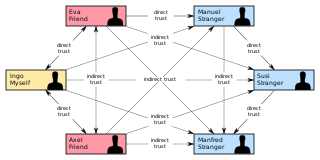
In cryptography, a web of trust is a concept used in PGP, GnuPG, and other OpenPGP-compatible systems to establish the authenticity of the binding between a public key and its owner. Its decentralized trust model is an alternative to the centralized trust model of a public key infrastructure (PKI), which relies exclusively on a certificate authority. As with computer networks, there are many independent webs of trust, and any user can be a part of, and a link between, multiple webs.

Werner Koch is a German free software developer. He is best known as the principal author of the GNU Privacy Guard. He was also Head of Office and German Vice-Chancellor of the Free Software Foundation Europe. He is the winner of Award for the Advancement of Free Software in 2015 for founding GnuPG.

Enigmail is a data encryption and decryption extension for Mozilla Thunderbird and the Postbox that provides OpenPGP public key e-mail encryption and signing. Enigmail works under Microsoft Windows, Unix-like, and Mac OS X operating systems. Enigmail can operate with other mail clients compatible with PGP/MIME and inline PGP such as: Microsoft Outlook with Gpg4win package installed, Gnome Evolution, KMail, Claws Mail, Gnus, Mutt. Its cryptographic functionality is handled by GNU Privacy Guard.
In cryptography, Camellia is a symmetric key block cipher with a block size of 128 bits and key sizes of 128, 192 and 256 bits. It was jointly developed by Mitsubishi Electric and NTT of Japan. The cipher has been approved for use by the ISO/IEC, the European Union's NESSIE project and the Japanese CRYPTREC project. The cipher has security levels and processing abilities comparable to the Advanced Encryption Standard.
S/MIME is a standard for public-key encryption and signing of MIME data. S/MIME is on an IETF standards track and defined in a number of documents, most importantly RFC 8551. It was originally developed by RSA Data Security, and the original specification used the IETF MIME specification with the de facto industry standard PKCS #7 secure message format. Change control to S/MIME has since been vested in the IETF, and the specification is now layered on Cryptographic Message Syntax (CMS), an IETF specification that is identical in most respects with PKCS #7. S/MIME functionality is built into the majority of modern email software and interoperates between them. Since it is built on CMS, MIME can also hold an advanced digital signature.
In computer security, a key server is a computer that receives and then serves existing cryptographic keys to users or other programs. The users' programs can be running on the same network as the key server or on another networked computer.

Seahorse is a GNOME front-end application for managing passwords, PGP and SSH keys. Seahorse integrates with a number of apps including Nautilus file manager, Epiphany browser and Evolution e-mail suite. It has HKP and LDAP key server support.

WinPT or Windows Privacy Tray is frontend to the Gnu Privacy Guard (GnuPG) for the Windows platform. Released under GPL, it is compatible with OpenPGP compliant software.

Tinfoil Hat Linux (THL) was a compact security-focused Linux distribution designed for high security developed by The Shmoo Group. The first version (1.000) was released in February 2002. By 2013, it had become a low-priority project. Its image files and source are available in gzip format. THL can be used on modern PCs using an Intel 80386 or better, with at least 8 MB of RAM. The distribution fits on a single HD floppy disk. The small footprint provides additional benefits beyond making the system easy to understand and verify. The computer need not even have a hard drive, making it easier to "sanitize" the computer after use.

Gpg4win is an email and file encryption package for most versions of Microsoft Windows and Microsoft Outlook, which utilises the GnuPG framework for symmetric and public-key cryptography, such as data encryption, digital signatures, hash calculations etc.

KDE Wallet Manager (KWallet) is free and open-source password management software written in C++ for UNIX-style operating systems. KDE Wallet Manager runs on a Linux-based OS and Its main feature is storing encrypted passwords in KDE Wallets. The main feature of KDE wallet manager (KWallet) is to collect user's credentials such as passwords or IDs and encrypt them through Blowfish symmetric block cipher algorithm or GNU Privacy Guard encryption.

In cryptography, the OpenPGP card is an ISO/IEC 7816-4, -8 compatible smart card that is integrated with many OpenPGP functions. Using this smart card, various cryptographic tasks can be performed. It allows secure storage of secret key material; all versions of the protocol state, "Private keys and passwords cannot be read from the card with any command or function." However, new key pairs may be loaded onto the card at any time, overwriting the existing ones.
In cryptography, Curve25519 is an elliptic curve used in elliptic-curve cryptography (ECC) offering 128 bits of security and designed for use with the Elliptic-curve Diffie–Hellman (ECDH) key agreement scheme. It is one of the fastest curves in ECC, and is not covered by any known patents. The reference implementation is public domain software.
eCryptfs is a package of disk encryption software for Linux. Its implementation is a POSIX-compliant filesystem-level encryption layer, aiming to offer functionality similar to that of GnuPG at the operating system level, and has been part of the Linux kernel since version 2.6.19.
Libgcrypt is a cryptography library developed as a separated module of GnuPG. It can also be used independently of GnuPG, but depends on its error-reporting library Libgpg-error.

GPG Mail is a commercial extension for Apple Mail which comes as part of GPG Suite, a software collection that provides easy access to a collection of tools designed to secure your communications and encrypt files. GPG Mail provides public key email encryption and signing. It integrates with the default email client Apple Mail under macOS and the actual cryptographic functionality is handled by GNU Privacy Guard.
The tables below compare cryptography libraries that deal with cryptography algorithms and have API function calls to each of the supported features.
SigSpoof is a family of security vulnerabilities that affected the software package GNU Privacy Guard ("GnuPG") since version 0.2.2, that was released in 1998. Several other software packages that make use of GnuPG were also affected, such as Pass and Enigmail.