
Jart Armin is an investigator, analyst and writer on cybercrime and computer security, and researcher of cybercrime mechanisms and assessment.

Jart Armin is an investigator, analyst and writer on cybercrime and computer security, and researcher of cybercrime mechanisms and assessment.
Armin first came into the public eye in 2007 from his exposure of the RBN (Russian Business Network). Throughout 2007, via a dedicated blog entitled RBNExploit, he provided reports and analysis on the undercover operations of the RBN criminal gang, despite constant DDoS attempts and artificially-created mirror websites.
It was via the RBN blog that Armin provided the first reports of cyber attacks, used in conjunction with the invasion of Georgia by Russian troops, [1] three days in advance of the attack in August 2008.
As an advocate of an open source community approach to the fight against cybercrime, Armin established HostExploit as an educational website aimed at exposing internet bad actors and cybercriminal organizations which deliver crimeware through hosts and registrars.
In August 2008, Jart Armin, via HostExploit, published a report "Atrivo - Cyber Crime USA", [2] stating that Atrivo (aka Intercage) - a Concord, California-based website hosting provider deliberately allowed cyber criminals to use its services. This brought about the shutdown of Atrivo with a related 10% drop in botnet and spam activity worldwide.
In November 2008, Armin published a further report, "McColo - Cyber Crime USA", [3] with contributions from StopBadware, Trend Micro, Emerging Threats, KnujOn, Sunbelt, CastleCops, The Spamhaus Project, Arbor Networks, Malwaredomains, Threat Expert, SecureWorks, aa419, Malwaredatabase and Robtex. The report, and press coverage used in conjunction to the report, [4] were instrumental in the demise of McColo by revealing the web hosting service provider to be deliberately funding criminal activities and illegal child sexual abuse content.
The cybercriminal activities of EstDomains were tracked by Armin and his allies in RBN blog postings and HostExploit reports. [2] Exposing the link between the RBN and EstDomains in the October 2008 report entitled "RBN – Farewell to EstDomains" [5] lead to the operational closure of the EstDomains [6] business and to its customer base moving to the Asian registrar Directi.
In a joint venture with Andrew Martin of MartinSecurity.net, Armin issued the report "Real Host Latvia – RBN Resurgence or Clone?" [7] in August 2009, providing further evidence of continuing RBN involvement in internet fraud. Telia, the hosting registrar, suspended all involvement with Real Host when provided with the evidence contained within the report.
In November 2009, in another joint venture with Andrew Martin [8] and Scott Logan, Jart Armin and HostExploit released a report called "MALfi, A Cybercrime International Report - A Silent Threat". [9] The report describes how hackers and cybercriminals use blended attacks - a combination of RFI (remote file inclusion), LFI (local file inclusion), cross-server attack, and RCE (remote code execution) - to compromise websites and servers.
In August 2010, Armin and the HostExploit team released a report [10] [11] providing an analysis of Demand Media's persistent position as "No 1 Bad Host" in HostExploit’s Top 50 Bad Hosts list.
Armin has spoken to audiences at Cambridge University and Tallinn, Estonia, APWG, NATO CCDOE and the Italian Senate, among others, on subjects ranging from the RBN, "Pocket Botnets" and "The Son of Stuxnet". He is a regular commentator on cybercrime and cybersecurity [12] He took part in a BBC World Service program on hacking in July 2011.[ citation needed ] He was a regular contributor on security topics to the website Internet Evolution.
At a workshop held at the 2015 ARES Conference in Toulouse, France, Armin presented the jointly authored paper, '2020 Cybercrime Economic Costs: No Measure No Solution', [13] a result of the EU FP7 Project CyberROAD. Armin presented on the subject of 0-Day Vulnerabilities and Cybercrime at the same venue.
Presentations on the subjects of Cyber Threat Intelligence (CTI) and cyber security metrics are regularly delivered at conferences including ARES 2018 at Hamburg, Germany, where Armin represented the Criminal Use of Information Hiding Initiative (CUING). In October 2018, Armin presented at the Global IEEE 5G-IoT Summit, Marrakesh, on the subject of IOT devices.
Armin regularly participates in EU funded projects (FP7 and H2020) such as ACDC 2013–2015, SWEPT 2014–2017, CyberROAD 2015–2017, SISSDEN 2016–2019, and SAINT 2017–2019.
Armin is a member of the ENISA Threat Landscape Stakeholder Group.
Armin has been cited in books on cybercrime and cyberwarfare. [14] [15]
HostExploit [16] was set up by Armin as an offshoot from the RBN blog to explore wider cybercrime themes. It operates as an open source community project to inform on topics relating to cybercrime with links to daily news items, articles and reports written by Jart Armin and others.
HostExploit reports are regularly cited in academic research papers. [17] [18]

Cybercrime is a crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target. Cybercrime may harm someone's security and financial health.
Domain hijacking or domain theft is the act of changing the registration of a domain name without the permission of its original registrant, or by abuse of privileges on domain hosting and registrar software systems.

A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and "network". The term is usually used with a negative or malicious connotation.
The Australian High Tech Crime Centre (AHTCC) are hosted by the Australian Federal Police (AFP) at their headquarters in Canberra. Under the auspices of the AFP, the AHTCC is party to the formal Joint Operating Arrangement established between the AFP, the Australian Security Intelligence Organisation and the Computer Network Vulnerability Team of the Australian Signals Directorate.

The Spamhaus Project is an international organisation based in the Principality of Andorra, founded in 1998 by Steve Linford to track email spammers and spam-related activity. The name spamhaus, a pseudo-German expression, was coined by Linford to refer to an internet service provider, or other firm, which spams or knowingly provides service to spammers.

Bulletproof hosting (BPH) is technical infrastructure service provided by a web hosting provider that is resilient to complaints of illicit activities, which serves criminal actors as a basic building block for streamlining various cyberattacks. BPH providers allow online gambling, illegal pornography, botnet command and control servers, spam, copyrighted materials, hate speech and misinformation, despite takedown court orders and law enforcement subpoenas, allowing such material in their acceptable use policies.
Brian Krebs is an American journalist and investigative reporter. He is best known for his coverage of profit-seeking cybercriminals. Krebs is the author of a daily blog, KrebsOnSecurity.com, covering computer security and cybercrime. From 1995 to 2009, Krebs was a reporter for The Washington Post and covered tech policy, privacy and computer security as well as authoring the Security Fix blog. He is also known for interviewing hacker 0x80.

The Storm botnet or Storm worm botnet was a remotely controlled network of "zombie" computers that had been linked by the Storm Worm, a Trojan horse spread through e-mail spam. At its height in September 2007, the Storm botnet was running on anywhere from 1 million to 50 million computer systems, and accounted for 8% of all malware on Microsoft Windows computers. It was first identified around January 2007, having been distributed by email with subjects such as "230 dead as storm batters Europe," giving it its well-known name. The botnet began to decline in late 2007, and by mid-2008 had been reduced to infecting about 85,000 computers, far less than it had infected a year earlier.
The Russian Business Network is a multi-faceted cybercrime organization, specializing in and in some cases monopolizing personal identity theft for resale. It is the originator of MPack and an alleged operator of the now defunct Storm botnet.
Srizbi BotNet is considered one of the world's largest botnets, and responsible for sending out more than half of all the spam being sent by all the major botnets combined. The botnets consist of computers infected by the Srizbi trojan, which sent spam on command. Srizbi suffered a massive setback in November 2008 when hosting provider Janka Cartel was taken down; global spam volumes reduced up to 93% as a result of this action.
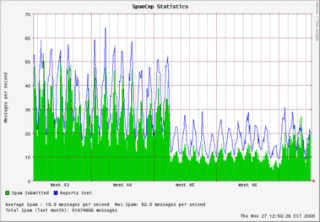
McColo was a US-based web hosting service provider that was, for a long time, the source of the majority of spam-sending activities for the entire world. In late 2008, the company was shut down by two upstream providers, Global Crossing and Hurricane Electric, because a significant amount of malware and botnets had been trafficking from the McColo servers.
Avalanche was a criminal syndicate involved in phishing attacks, online bank fraud, and ransomware. The name also refers to the network of owned, rented, and compromised systems used to carry out that activity. Avalanche only infected computers running the Microsoft Windows operating system.
The Grum botnet, also known by its alias Tedroo and Reddyb, was a botnet mostly involved in sending pharmaceutical spam e-mails. Once the world's largest botnet, Grum can be traced back to as early as 2008. At the time of its shutdown in July 2012, Grum was reportedly the world's third largest botnet, responsible for 18% of worldwide spam traffic.
There is no commonly agreed single definition of “cybercrime”. It refers to illegal internet-mediated activities that often take place in global electronic networks. Cybercrime is "international" or "transnational" – there are ‘no cyber-borders between countries'. International cybercrimes often challenge the effectiveness of domestic and international law, and law enforcement. Because existing laws in many countries are not tailored to deal with cybercrime, criminals increasingly conduct crimes on the Internet in order to take advantages of the less severe punishments or difficulties of being traced. No matter, in developing or developed countries, governments and industries have gradually realized the colossal threats of cybercrime on economic and political security and public interests. However, complexity in types and forms of cybercrime increases the difficulty to fight back. In this sense, fighting cybercrime calls for international cooperation. Various organizations and governments have already made joint efforts in establishing global standards of legislation and law enforcement both on a regional and on an international scale. China–United States cooperation is one of the most striking progress recently, because they are the top two source countries of cybercrime.

The Cyber Division (CyD) is a Federal Bureau of Investigation division which heads the national effort to investigate and prosecute internet crimes, including "cyber based terrorism, espionage, computer intrusions, and major cyber fraud." This division of the FBI uses the information it gathers during investigation to inform the public of current trends in cyber crime. It focuses around three main priorities: computer intrusion, identity theft, and cyber fraud. It was created in 2002.
Virut is a cybercrime malware botnet, operating at least since 2006, and one of the major botnets and malware distributors on the Internet. In January 2013 its operations were disrupted by the Polish organization Naukowa i Akademicka Sieć Komputerowa.

The Microsoft Digital Crimes Unit (DCU) is a Microsoft sponsored team of international legal and internet security experts employing the latest tools and technologies to stop or interfere with cyber crime and cyber threats. The Microsoft Digital Crimes Unit was assembled in 2008. In 2013, a Cybercrime center for the DCU was opened in Redmond, Washington. There are about 100 members of the DCU stationed just in Redmond, Washington at the original Cybercrime Center. Members of the DCU include lawyers, data scientists, investigators, forensic analysts, and engineers. The DCU has international offices located in major cities such as: Beijing, Berlin, Bogota, Delhi, Dublin, Hong Kong, Sydney, and Washington, D.C. The DCU's main focuses are child protection, copyright infringement and malware crimes. The DCU must work closely with law enforcement to ensure the perpetrators are punished to the full extent of the law. The DCU has taken down many major botnets such as the Citadel, Rustock, and Zeus. Around the world malware has cost users about $113 billion and the DCU's jobs is to shut them down in accordance with the law.

dark0de, also known as Darkode, is a cybercrime forum and black marketplace described by Europol as "the most prolific English-speaking cybercriminal forum to date". This site which was launched in 2007, serves as a venue for the sale and trade of hacking services, botnets, malware, stolen personally identifiable information, credit card information, hacked server credentials, and other illicit goods and services.
A threat actor or malicious actor is either a person or a group of people that take part in an action that is intended to cause harm to the cyber realm including: computers, devices, systems, or networks. The term is typically used to describe individuals or groups that perform malicious acts against a person or an organization of any type or size. Threat actors engage in cyber related offenses to exploit open vulnerabilities and disrupt operations. Threat actors have different educational backgrounds, skills, and resources. The frequency and classification of cyber attacks changes rapidly. The background of threat actors helps dictate who they target, how they attack, and what information they seek. There are a number of threat actors including: cyber criminals, nation-state actors, ideologues, thrill seekers/trolls, insiders, and competitors. These threat actors all have distinct motivations, techniques, targets, and uses of stolen data.
Ghana has one of the highest rates of cybercrime in the world, ranking 7th in a 2008 Internet Crime Survey. The most popular form of cybercrime in Ghana is cyberfraud and is typically achieved via credit card fraud. However, recent decreases in universal credit card usage has seen the expansion of other cybercrimes such as blackmail and hacking. This growth in crime has warranted a government response, with policies specifically addressing the cyberspace being developed. This has necessitated various studies including a cyber security maturity study which was inaugurated by the Ministry of Communications and conducted by the Global Cyber Security Capacity Center (GCSCC) of the University of Oxford in collaboration with the World Bank.