This article needs additional citations for verification .(August 2012) |
A key code is a series of alphanumeric characters used by locksmiths to create a key. There are two kinds of key codes: blind codes and bitting codes.
This article needs additional citations for verification .(August 2012) |
A key code is a series of alphanumeric characters used by locksmiths to create a key. There are two kinds of key codes: blind codes and bitting codes.
These are codes that require a chart or computer program to translate the blind code to a bitting code, which is used to create the actual key. Most key codes are blind codes, and publication of code books or software is restricted to licensed locksmiths in most jurisdictions for security reasons[ citation needed ]. Some locksmiths also create their own blind coding systems for identifying key systems they installed, or for customer identification and authorization in high security systems. Example: 23N7 (General Motors) or X2100 (Nissan) are examples of blind codes used for automotive ignition keys.
Many computer and manually generated master keying charts also utilize blind codes for identifying individual change keys and masters within the system.
The bitting code is the translated blind code which the locksmith actually uses to cut each blank key. Example: padlock blind code W123 translates to bitting code 25313, to which the locksmith would cut the key with his code machine by setting it to 25313.
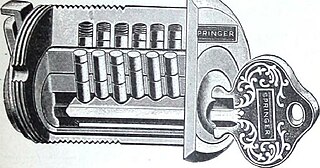
The bitting code is used in conjunction with a key's Depth and Spacing Number to completely determine all relevant information regarding the key's geometry. [1] Each number in the bitting code corresponds to a cut on the key blade. For example, a bitting code of 11111 with Depth and Spacing Number 46 specifies a Kwikset key with five shallow cuts. Conversely, a bitting code of 77777 and Depth with Spacing Number 46 specifies a Kwikset key with five deep cuts.
Experienced locksmiths might be able to figure out a bitting code from looking at a picture of a key. This happened to Diebold voting machines in 2007 after they posted a picture of their master key online, people were able to make their own key to match it and open the machines. [2] [3]
Extended Binary Coded Decimal Interchange Code is an eight-bit character encoding used mainly on IBM mainframe and IBM midrange computer operating systems. It descended from the code used with punched cards and the corresponding six-bit binary-coded decimal code used with most of IBM's computer peripherals of the late 1950s and early 1960s. It is supported by various non-IBM platforms, such as Fujitsu-Siemens' BS2000/OSD, OS-IV, MSP, and MSP-EX, the SDS Sigma series, Unisys VS/9, Unisys MCP and ICL VME.

A hash function is any function that can be used to map data of arbitrary size to fixed-size values, though there are some hash functions that support variable length output. The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to index a fixed-size table called a hash table. Use of a hash function to index a hash table is called hashing or scatter storage addressing.

Keykode is an Eastman Kodak Company advancement on edge numbers, which are letters, numbers and symbols placed at regular intervals along the edge of 35 mm and 16 mm film to allow for frame-by-frame specific identification. It was introduced in 1990.

In computer programming, machine code is computer code consisting of machine language instructions, which are used to control a computer's central processing unit (CPU). Although decimal computers were once common, the contemporary marketplace is dominated by binary computers; for those computers, machine code is "the binary representation of a computer program which is actually read and interpreted by the computer. A program in machine code consists of a sequence of machine instructions ."

Punched tape or perforated paper tape is a form of data storage device that consists of a long strip of paper through which small holes are punched. It was developed from and was subsequently used alongside punched cards, the difference being that the tape is continuous.

Lock picking is the practice of unlocking a lock by manipulating the components of the lock device without the original key.
Premier Election Solutions, formerly Diebold Election Systems, Inc. (DESI), was a subsidiary of Diebold that made and sold voting machines.

PETSCII, also known as CBM ASCII, is the character set used in Commodore Business Machines' 8-bit home computers.

A lock is a mechanical or electronic fastening device that is released by a physical object, by supplying secret information, by a combination thereof, or it may only be able to be opened from one side, such as a door chain.
Registration authorities exist for many standards organizations, such as ANNA, the Object Management Group, W3C, and others. In general, registration authorities all perform a similar function, in promoting the use of a particular standard through facilitating its use. This may be by applying the standard, where appropriate, or by verifying that a particular application satisfies the standard's tenants. Maintenance agencies, in contrast, may change an element in a standard based on set rules – such as the creation or change of a currency code when a currency is created or revalued. The Object Management Group has an additional concept of certified provider, which is deemed an entity permitted to perform some functions on behalf of the registration authority, under specific processes and procedures documented within the standard for such a role.

A key blank is a key that has not been cut to a specific bitting. The blank has a specific cross-sectional profile to match the keyway in a corresponding lock cylinder. Key blanks can be stamped with a manufacturer name, end-user logo or with a phrase, the most commonly seen being 'Do not duplicate'. Blanks are typically stocked by locksmiths for duplicating keys. The profile of the key bow, or the large, flat end, is often characteristic of an individual manufacturer.

Bitting is the depth of key cuts on a cylinder key for a pin tumbler lock, often expressed as a number. Bitting also refers to the combination of key cuts on a bit key for a warded lock or lever tumbler lock.

A car key or an automobile key is a key used to open and/or start an automobile. Modern key designs are usually symmetrical, and some use grooves on both sides, rather than a cut edge, to actuate the lock. It has multiple uses for the automobile with which it was sold. A car key can open the doors, as well as start the ignition, open the glove compartment and also open the trunk (boot) of the car. Some cars come with an additional key known as a valet key that starts the ignition and opens the driver's side door, but prevents the valet from gaining access to valuables that are located in the trunk or the glove box. Some valet keys, particularly those to high-performance vehicles, go so far as to restrict the engine's power output to prevent joyriding. Recently, features such as coded immobilizers have been implemented in newer vehicles. More sophisticated systems make ignition dependent on electronic devices, rather than the mechanical keyswitch. A number of these systems, such as KeeLoq and Megamos Crypto have been demonstrated to be weak and vulnerable to cryptanalytic attacks.
ISO 8583 is an international standard for financial transaction card originated interchange messaging. It is the International Organization for Standardization standard for systems that exchange electronic transactions initiated by cardholders using payment cards.
Rekeying a lock is replacing the old lock pins with new lock pins.
A master key operates a set of several locks. Usually, there is nothing different about the key. The differences are in the locks the key will operate. These master-keyed locks are configured to operate with two, or more, different keys: one specific to each lock, which cannot operate any of the others in the set, and the master key, which operates all the locks in the set. Locks that have master keys have a second set of the mechanism used to operate them that is identical to all of the others in the set of locks. For example, master keyed pin tumbler locks often have two shear points at each pin position, one for the change key and one for the master key. A far more secure system has two cylinders in each lock, one for the change key and one for the master key.
In the design of modern computers, memory geometry describes the internal structure of random-access memory. Memory geometry is of concern to consumers upgrading their computers, since older memory controllers may not be compatible with later products. Memory geometry terminology can be confusing because of the number of overlapping terms.
The term digital card can refer to a physical item, such as a memory card on a camera, or, increasingly since 2017, to the digital content hosted as a virtual card or cloud card, as a digital virtual representation of a physical card. They share a common purpose: Identity Management, Credit card, Debit card or driver license. A non-physical digital card, unlike a Magnetic stripe card can emulate (imitate) any kind of card.
This is a glossary of locksmithing terms.

Key duplication refers to the process of creating a key based on an existing key. Key cutting is the primary method of key duplication: a flat key is fitted into a vise in a machine, with a blank attached to a parallel vise, and the original key is moved along a guide, while the blank is moved against a blade, which cuts it. After cutting, the new key is deburred: scrubbed with a wire brush, either built into the machine, or in a bench grinder, to remove burrs which, were they not removed, would be dangerously sharp and, further, foul locks.