Related Research Articles

Wake-on-LAN is an Ethernet or Token Ring computer networking standard that allows a computer to be turned on or awakened from sleep mode by a network message.

A packet analyzer, also known as packet sniffer, protocol analyzer, or network analyzer, is a computer program or computer hardware such as a packet capture appliance that can analyze and log traffic that passes over a computer network or part of a network. Packet capture is the process of intercepting and logging traffic. As data streams flow across the network, the analyzer captures each packet and, if needed, decodes the packet's raw data, showing the values of various fields in the packet, and analyzes its content according to the appropriate RFC or other specifications.
IEEE 802.1X is an IEEE Standard for port-based network access control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN.

Server Message Block (SMB) is a communication protocol used to share files, printers, serial ports, and miscellaneous communications between nodes on a network. On Microsoft Windows, the SMB implementation consists of two vaguely named Windows services: "Server" and "Workstation". It uses NTLM or Kerberos protocols for user authentication. It also provides an authenticated inter-process communication (IPC) mechanism.
Internet Connection Sharing (ICS) is a Windows service that enables one Internet-connected computer to share its Internet connection with other computers on a local area network (LAN). The computer that shares its Internet connection serves as a gateway device, meaning that all traffic between other computers and the Internet go through this computer. ICS provides Dynamic Host Configuration Protocol (DHCP) and network address translation (NAT) services for the LAN computers.

Kismet is a network detector, packet sniffer, and intrusion detection system for 802.11 wireless LANs. Kismet will work with any wireless card which supports raw monitoring mode, and can sniff 802.11a, 802.11b, 802.11g, and 802.11n traffic. The program runs under Linux, FreeBSD, NetBSD, OpenBSD, and macOS. The client can also run on Microsoft Windows, although, aside from external drones, there's only one supported wireless hardware available as packet source.
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in RFC 3748, which made RFC 2284 obsolete, and is updated by RFC 5247. EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods. There are many methods defined by RFCs, and a number of vendor-specific methods and new proposals exist. EAP is not a wire protocol; instead it only defines the information from the interface and the formats. Each protocol that uses EAP defines a way to encapsulate by the user EAP messages within that protocol's messages.

Microsoft Forefront Threat Management Gateway, formerly known as Microsoft Internet Security and Acceleration Server, is a discontinued network router, firewall, antivirus program, VPN server and web cache from Microsoft Corporation. It ran on Windows Server and works by inspecting all network traffic that passes through it.
In the field of computer network administration, pcap is an application programming interface (API) for capturing network traffic. While the name is an abbreviation of packet capture, that is not the API's proper name. Unix-like systems implement pcap in the libpcap library; for Windows, there is a port of libpcap named WinPcap that is no longer supported or developed, and a port named Npcap for Windows 7 and later that is still supported.

Wireless security is the prevention of unauthorized access or damage to computers or data using wireless networks, which include Wi-Fi networks. The term may also refer to the protection of the wireless network itself from adversaries seeking to damage the confidentiality, integrity, or availability of the network. The most common type is Wi-Fi security, which includes Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is an old IEEE 802.11 standard from 1997. It is a notoriously weak security standard: the password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP was superseded in 2003 by WPA, a quick alternative at the time to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP. Enterprises often enforce security using a certificate-based system to authenticate the connecting device, following the standard 802.11X.

A bus analyzer is a type of a protocol analysis tool, used for capturing and analyzing communication data across a specific interface bus, usually embedded in a hardware system. The bus analyzer functionality helps design, test and validation engineers to check, test, debug and validate their designs throughout the design cycles of a hardware-based product. It also helps in later phases of a product life cycle, in examining communication interoperability between systems and between components, and clarifying hardware support concerns.
Monitor mode, or RFMON mode, allows a computer with a wireless network interface controller (WNIC) to monitor all traffic received on a wireless channel. Unlike promiscuous mode, which is also used for packet sniffing, monitor mode allows packets to be captured without having to associate with an access point or ad hoc network first. Monitor mode only applies to wireless networks, while promiscuous mode can be used on both wired and wireless networks. Monitor mode is one of the eight modes that 802.11 wireless adapter can operate in: Master, Managed, Ad hoc, Repeater, Mesh, Wi-Fi Direct, TDLS and Monitor mode.

Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, the project was renamed Wireshark in May 2006 due to trademark issues.
There are a number of security and safety features new to Windows Vista, most of which are not available in any prior Microsoft Windows operating system release.
Link Layer Topology Discovery (LLTD) is a proprietary link layer protocol for network topology discovery and quality of service diagnostics. Microsoft developed it as part of the Windows Rally set of technologies. The LLTD protocol operates over both wired as well as wireless networks.
Omnipeek is a packet analyzer software tool from Savvius, a LiveAction company, for network troubleshooting and protocol analysis. It supports an application programming interface (API) for plugins.
In computing, Microsoft's Windows Vista and Windows Server 2008 introduced in 2007/2008 a new networking stack named Next Generation TCP/IP stack, to improve on the previous stack in several ways. The stack includes native implementation of IPv6, as well as a complete overhaul of IPv4. The new TCP/IP stack uses a new method to store configuration settings that enables more dynamic control and does not require a computer restart after a change in settings. The new stack, implemented as a dual-stack model, depends on a strong host-model and features an infrastructure to enable more modular components that one can dynamically insert and remove.
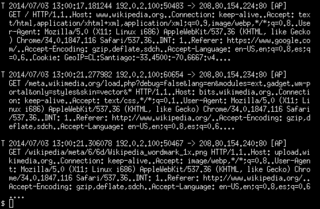
ngrep is a network packet analyzer written by Jordan Ritter. It has a command-line interface, and relies upon the pcap library and the GNU regex library.
CommView is an application for network monitoring, packet analysis, and decoding. There are two editions of CommView: the standard edition for Ethernet networks and the wireless edition for 802.11 networks named CommView for WiFi. The application runs on Microsoft Windows. It is developed by TamoSoft, a privately held New Zealand company founded in 1998.

The Sniffer was a computer network packet and protocol analyzer developed and first sold in 1986 by Network General Corporation of Mountain View, CA. By 1994 the Sniffer had become the market leader in high-end protocol analyzers. According to SEC 10-K filings and corporate annual reports, between 1986 and March 1997 about $933M worth of Sniffers and related products and services had been sold as tools for network managers and developers.
References
- ↑ "[MS-WININTBLOGLP]: Microsoft Message Analyzer Blog". Microsoft Docs. November 25, 2019.
- ↑ Paul E Long (17 September 2012). "Meet the successor to Microsoft Network Monitor!". Microsoft TechNet.
- ↑ greggigwg. "Microsoft Message Analyzer Operating Guide - Message Analyzer". docs.microsoft.com. Retrieved 2021-08-26.