Related Research Articles
A virtual private network (VPN) is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet.
In computer networking, promiscuous mode is a mode for a wired network interface controller (NIC) or wireless network interface controller (WNIC) that causes the controller to pass all traffic it receives to the central processing unit (CPU) rather than passing only the frames that the controller is specifically programmed to receive. This mode is normally used for packet sniffing that takes place on a router or on a computer connected to a wired network or one being part of a wireless LAN. Interfaces are placed into promiscuous mode by software bridges often used with hardware virtualization.
The Intelligent Platform Management Interface (IPMI) is a set of computer interface specifications for an autonomous computer subsystem that provides management and monitoring capabilities independently of the host system's CPU, firmware and operating system. IPMI defines a set of interfaces used by system administrators for out-of-band management of computer systems and monitoring of their operation. For example, IPMI provides a way to manage a computer that may be powered off or otherwise unresponsive by using a network connection to the hardware rather than to an operating system or login shell. Another use case may be installing a custom operating system remotely. Without IPMI, installing a custom operating system may require an administrator to be physically present near the computer, insert a DVD or a USB flash drive containing the OS installer and complete the installation process using a monitor and a keyboard. Using IPMI, an administrator can mount an ISO image, simulate an installer DVD, and perform the installation remotely.
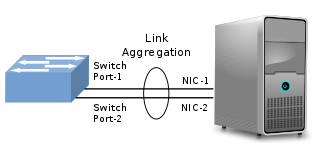
In computer networking, link aggregation is the combining of multiple network connections in parallel by any of several methods. Link aggregation increases total throughput beyond what a single connection could sustain, and provides redundancy where all but one of the physical links may fail without losing connectivity. A link aggregation group (LAG) is the combined collection of physical ports.

A computer network is a set of computers sharing resources located on or provided by network nodes. Computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies.
The following is a timeline of virtualization development. In computing, virtualization is the use of a computer to simulate another computer. Through virtualization, a host simulates a guest by exposing virtual hardware devices, which may be done through software or by allowing access to a physical device connected to the machine.
Desktop virtualization is a software technology that separates the desktop environment and associated application software from the physical client device that is used to access it.

VMware ESXi is an enterprise-class, type-1 hypervisor developed by VMware, a subsidiary of Broadcom, for deploying and serving virtual computers. As a type-1 hypervisor, ESXi is not a software application that is installed on an operating system (OS); instead, it includes and integrates vital OS components, such as a kernel.
Split tunneling is a computer networking concept which allows a user to access dissimilar security domains like a public network and a local area network or wide area network at the same time, using the same or different network connections. This connection state is usually facilitated through the simultaneous use of a LAN network interface controller (NIC), radio NIC, Wireless LAN (WLAN) NIC, and VPN client software application without the benefit of an access control.

A computer appliance is a computer system with a combination of hardware, software, or firmware that is specifically designed to provide a particular computing resource. Such devices became known as appliances because of the similarity in role or management to a home appliance, which are generally closed and sealed, and are not serviceable by the user or owner. The hardware and software are delivered as an integrated product and may even be pre-configured before delivery to a customer, to provide a turn-key solution for a particular application. Unlike general purpose computers, appliances are generally not designed to allow the customers to change the software and the underlying operating system, or to flexibly reconfigure the hardware.
Infrastructure as a service (IaaS) is a cloud computing service model by means of which computing resources are supplied by a cloud services provider. The IaaS vendor provides the storage, network, servers, and virtualization. This service enables users to free themselves from maintaining an on-premises data center. The IaaS provider is hosting these resources in either the public cloud, the private cloud, or the hybrid cloud.

Zeroshell is a small open-source Linux distribution for servers and embedded systems which aims to provide network services. Its administration relies on a web-based graphical interface; no shell is needed to administer and configure it. Zeroshell is available as Live CD and CompactFlash images, and VMware virtual machines.
A virtual security switch is a software Ethernet switch with embedded security controls within it that runs within virtual environments such as VMware vSphere, Citrix XenDesktop, Microsoft Hyper-V and Virtual Iron. The primary purpose of a virtual security switch is to provide security measures such as isolation, control and content inspection between virtual machines.
In computing, virtualization or virtualisation in British English is the act of creating a virtual version of something at the same abstraction level, including virtual computer hardware platforms, storage devices, and computer network resources.
A virtual firewall (VF) is a network firewall service or appliance running entirely within a virtualized environment and which provides the usual packet filtering and monitoring provided via a physical network firewall. The VF can be realized as a traditional software firewall on a guest virtual machine already running, a purpose-built virtual security appliance designed with virtual network security in mind, a virtual switch with additional security capabilities, or a managed kernel process running within the host hypervisor.
CloudStack is open-source Infrastructure-as-a-Service cloud computing software for creating, managing, and deploying infrastructure cloud services. It uses existing hypervisor platforms for virtualization, such as KVM, VMware vSphere, including ESXi and vCenter, XenServer/XCP and XCP-ng. In addition to its own API, CloudStack also supports the Amazon Web Services (AWS) API and the Open Cloud Computing Interface from the Open Grid Forum.
The Data Plane Development Kit (DPDK) is an open source software project managed by the Linux Foundation. It provides a set of data plane libraries and network interface controller polling-mode drivers for offloading TCP packet processing from the operating system kernel to processes running in user space. This offloading achieves higher computing efficiency and higher packet throughput than is possible using the interrupt-driven processing provided in the kernel.
Distributed Overlay Virtual Ethernet (DOVE) is a tunneling and virtualization technology for computer networks, created and backed by IBM. DOVE allows creation of network virtualization layers for deploying, controlling, and managing multiple independent and isolated network applications over a shared physical network infrastructure.

Open vSwitch, sometimes abbreviated as OVS, is an open-source implementation of a distributed virtual multilayer switch. The main purpose of Open vSwitch is to provide a switching stack for hardware virtualization environments, while supporting multiple protocols and standards used in computer networks.

Endian Firewall is an open-source router, firewall and gateway security Linux distribution developed by the South Tyrolean company Endian. The product is available as either free software, commercial software with guaranteed support services, or as a hardware appliance.
References
- ↑ P. Martinez-Julia, A. F. Skarmeta, A. Galis. "Towards a Secure Network Virtualization Architecture for the Future Internet" Future Internet Assembly, 2013, doi : 10.1007/978-3-642-38082-2_12.
- ↑ A. Galis, S. Clayman, A. Fischer, A. Paler, Y. Al-Hazmi, H. De Meer, A. Cheniour, O. Mornard, J. Patrick Gelas and L. Lefevre, et al. "Future Internet Management Platforms for Network Virtualisation and Service Clouds"- ServiceWave 2010, December 2010, http://servicewave.eu/2010/joint-demonstration-evening/ Archived 2014-07-31 at the Wayback Machine and in "Towards A Service-Based Internet" Lecture Notes in Computer Science, 2010, Volume 6481/2010, 235-237, doi : 10.1007/978-3-642-17694-4_39
- ↑ Liang, C.; Yu, F. R. (2015). "Wireless Network Virtualization: A Survey, Some Research Issues and Challenges". IEEE Communications Surveys and Tutorials. 17 (1): 358–380. doi:10.1109/COMST.2014.2352118. S2CID 14838118.
- Victor Moreno and Kumar Reddy (2006). Network Virtualization. Indianapolis: Cisco Press.