Related Research Articles
Internetworking is the practice of interconnecting multiple computer networks, such that any pair of hosts in the connected networks can exchange messages irrespective of their hardware-level networking technology. The resulting system of interconnected networks are called an internetwork, or simply an internet.
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address. For example, an error is indicated when a requested service is not available or that a host or router could not be reached. ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications.
The Internet protocol suite, commonly known as TCP/IP, is a framework for organizing the set of communication protocols used in the Internet and similar computer networks according to functional criteria. The foundational protocols in the suite are the Transmission Control Protocol (TCP), the User Datagram Protocol (UDP), and the Internet Protocol (IP). Early versions of this networking model were known as the Department of Defense (DoD) model because the research and development were funded by the United States Department of Defense through DARPA.

The Open Systems Interconnection model is a reference model from the International Organization for Standardization (ISO) that "provides a common basis for the coordination of standards development for the purpose of systems interconnection." In the OSI reference model, the communications between systems are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application.

The protocol stack or network stack is an implementation of a computer networking protocol suite or protocol family. Some of these terms are used interchangeably but strictly speaking, the suite is the definition of the communication protocols, and the stack is the software implementation of them.

A router is a computer and a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions between networks and on the global Internet. Data sent through a network, such as a web page or email, is in the form of data packets. A packet is typically forwarded from one router to another router through the networks that constitute an internetwork until it reaches its destination node.

Wake-on-LAN is an Ethernet or Token Ring computer networking standard that allows a computer to be turned on or awakened from sleep mode by a network message.
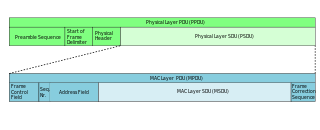
In telecommunications, a protocol data unit (PDU) is a single unit of information transmitted among peer entities of a computer network. It is composed of protocol-specific control information and user data. In the layered architectures of communication protocol stacks, each layer implements protocols tailored to the specific type or mode of data exchange.

In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end communication services for applications. It provides services such as connection-oriented communication, reliability, flow control, and multiplexing.
A virtual private network (VPN) is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet.
The data link layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers data between nodes on a network segment across the physical layer. The data link layer provides the functional and procedural means to transfer data between network entities and may also provide the means to detect and possibly correct errors that can occur in the physical layer.
A multilayer switch (MLS) is a computer networking device that switches on OSI layer 2 like an ordinary network switch and provides extra functions on higher OSI layers. The MLS was invented by engineers at Digital Equipment Corporation.
An overlay network is a computer network that is layered on top of another network. The concept of overlay networking is distinct from the traditional model of OSI layered networks, and almost always assumes that the underlay network is an IP network of some kind.
Networking hardware, also known as network equipment or computer networking devices, are electronic devices that are required for communication and interaction between devices on a computer network. Specifically, they mediate data transmission in a computer network. Units which are the last receiver or generate data are called hosts, end systems or data terminal equipment.
A network socket is a software structure within a network node of a computer network that serves as an endpoint for sending and receiving data across the network. The structure and properties of a socket are defined by an application programming interface (API) for the networking architecture. Sockets are created only during the lifetime of a process of an application running in the node.
The internet layer is a group of internetworking methods, protocols, and specifications in the Internet protocol suite that are used to transport network packets from the originating host across network boundaries; if necessary, to the destination host specified by an IP address. The internet layer derives its name from its function facilitating internetworking, which is the concept of connecting multiple networks with each other through gateways.

In routing, the forwarding plane, sometimes called the data plane or user plane, defines the part of the router architecture that decides what to do with packets arriving on an inbound interface. Most commonly, it refers to a table in which the router looks up the destination address of the incoming packet and retrieves the information necessary to determine the path from the receiving element, through the internal forwarding fabric of the router, and to the proper outgoing interface(s).
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any variation of a physical quantity. The protocol defines the rules, syntax, semantics, and synchronization of communication and possible error recovery methods. Protocols may be implemented by hardware, software, or a combination of both.

SoftEther VPN is free open-source, cross-platform, multi-protocol VPN client and VPN server software, developed as part of Daiyuu Nobori's master's thesis research at the University of Tsukuba. VPN protocols such as SSL VPN, L2TP/IPsec, OpenVPN, and Microsoft Secure Socket Tunneling Protocol are provided in a single VPN server. It was released using the GPLv2 license on January 4, 2014. The license was switched to Apache License 2.0 on January 21, 2019.
The Protocol Wars were a long-running debate in computer science that occurred from the 1970s to the 1990s, when engineers, organizations and nations became polarized over the issue of which communication protocol would result in the best and most robust networks. This culminated in the Internet–OSI Standards War in the 1980s and early 1990s, which was ultimately "won" by the Internet protocol suite (TCP/IP) by the mid-1990s when it became the dominant protocol through rapid adoption of the Internet.
References
- ↑ D. Cerović, V. Del Piccolo, A. Amamou, K. Haddadou and G. Pujolle, Fast Packet Processing: A Survey, in IEEE Communications Surveys & Tutorials, vol. 20, no. 4, pp. 3645-3676, Fourthquarter 2018. doi: 10.1109/COMST.2018.2851072
- ↑ International Organization for Standardization
- ↑ International Telecommunication Union)
- ↑ ISO/IEC 10731:1994. Information technology -- Open Systems Interconnection -- Basic Reference Model -- Conventions for the definition of OSI services
- ↑ ITU-T X.200-199407, X.200 : Information technology - Open Systems Interconnection - Basic Reference Model: The basic model
- ↑ Tech-FAQ. The OSI Model – What It Is; Why It Matters; Why It Doesn’t Matter
- ↑ Computer Networking Notes. Advantages of OSI 7 Layer Model
- ↑ "DARPA - Defense Advanced Research Projects Agency". Archived from the original on 2020-01-15. Retrieved 2012-01-05.
- ↑ Living Internet. ARPANET -- The First Internet
- ↑ W3 Schools, TCP/IP Tutorial
- ↑ Sheldon, Tom. Packets and Packet Processing Networks. Linktionary, 2001.
- ↑ Copeland, Lee. QuickStudy: Packet-Switched vs. Circuit-Switched Networks. Computerworld, March 2000.
- ↑ Negroponte, N. Being Digital. Vintage, Jan. 1996.
- ↑ Reding, Viviane. Digital convergence: a whole new way of life. Digital Lifestyle Exhibition, May 2006.
- ↑ Peterson, L. and Davie, B. Computer Networks (5th Edition): A Systems Approach. Morgon Kaufmann, March 2011.
- ↑ RFC Sourcebook. IP, Internet Protocol.
- ↑ Streenstrup, M. Routing in Communications Networks. Prentice Hall, April 1995.
- ↑ Anderson, P. and James, L. Performance soars, features vary - Review: Load Balancers. NetworkWorldFusion, June 1999.
- ↑ Murthy, S. Routing in Packet-Switched Networks Using Path-Finding Algorithms. UC Santa Cruz, 1996.
- ↑ U. of Maryland. Introduction, Rate and Latency. 2009
- ↑ Nokia Communications Framework Guide. What are Planes?. February 2010.
- ↑ Vin, H. Packet Processing Applications: An Overview. Univ. of Texas, Fall 2003.
- ↑ Reddy, M. Video Transcoding & Transrating - Video in 31 Flavors!. Vela, Sep. 2011.
- ↑ Elhanany, I. and Hamdi, M. High Performance Packet Switching Architectures. Springer, November 2011.
- ↑ Selissen, M. Packet Processing Needs Balanced Between Architecture, Network. EE Times, Aug 2002.
- ↑ Foong, A., Fung, J. and Newell, D. Improved Linux SMP Scaling: User-directed Processor Affinity. Intel Software Network, October 2008.
- ↑ CDC Innovation. 6WIND Provides 10x Acceleration of Packet Processing Functions on New multicore Intel® Platforms. March, 2010.
- ↑ NetLogic Microsystems. Advanced Algorithmic Knowledge-based Processors.
- ↑ Intel. Packet Processing with Intel® multicore Processors. 2008.
- ↑ Cheerla, R. Architecture Comparison For High Performance WAN Optimization Systems. Infineta, Cardinal Directions, March 2011.
- ↑ Cavium. OCTEON II CN63XX multicore MIPS64 Internet Application Processors
- ↑ NetLogic Microsystems. multicore Processor Solutions
- ↑ dpacket.org Introduction to Deep Packet Inspection/Processing.
- ↑ Multicore Packet Processing Forum