
The Intel 80186, also known as the iAPX 186, or just 186, is a microprocessor and microcontroller introduced in 1982. It was based on the Intel 8086 and, like it, had a 16-bit external data bus multiplexed with a 20-bit address bus. The 80188 variant, with an 8-bit external data bus was also available.
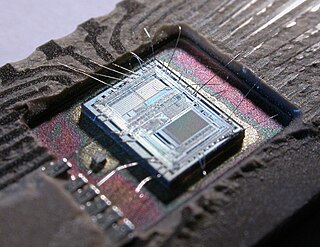
A microcontroller or microcontroller unit (MCU) is a small computer on a single integrated circuit. A microcontroller contains one or more CPUs along with memory and programmable input/output peripherals. Program memory in the form of ferroelectric RAM, NOR flash or OTP ROM is also often included on chip, as well as a small amount of RAM. Microcontrollers are designed for embedded applications, in contrast to the microprocessors used in personal computers or other general purpose applications consisting of various discrete chips.

AVR is a family of microcontrollers developed since 1996 by Atmel, acquired by Microchip Technology in 2016. These are modified Harvard architecture 8-bit RISC single-chip microcontrollers. AVR was one of the first microcontroller families to use on-chip flash memory for program storage, as opposed to one-time programmable ROM, EPROM, or EEPROM used by other microcontrollers at the time.

A system on a chip or system-on-chip is an integrated circuit that integrates most or all components of a computer or other electronic system. These components almost always include on-chip central processing unit (CPU), memory interfaces, input/output devices and interfaces, and secondary storage interfaces, often alongside other components such as radio modems and a graphics processing unit (GPU) – all on a single substrate or microchip. SoCs may contain digital and also analog, mixed-signal and often radio frequency signal processing functions.
ISO/IEC 14443Identification cards -- Contactless integrated circuit cards -- Proximity cards is an international standard that defines proximity cards used for identification, and the transmission protocols for communicating with it.
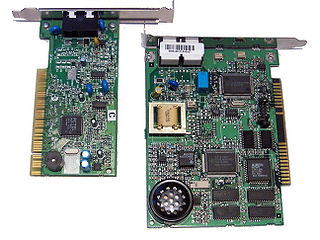
A software modem, commonly referred to as a softmodem, is a modem with minimal hardware that uses software running on the host computer, and the computer's resources, in place of the hardware in a conventional modem.

Near-field communication (NFC) is a set of communication protocols that enables communication between two electronic devices over a distance of 4 cm (1.57 in) or less. NFC offers a low-speed connection through a simple setup that can be used to bootstrap more capable wireless connections. Like other "proximity card" technologies, NFC is based on inductive coupling between two antennas present on NFC-enabled devices—for example a smartphone and a printer—communicating in one or both directions, using a frequency of 13.56 MHz in the globally available unlicensed radio frequency ISM band using the ISO/IEC 18000-3 air interface standard at data rates ranging from 106 to 848 kbit/s.

A TV tuner card is a kind of television tuner that allows television signals to be received by a computer. Most TV tuners also function as video capture cards, allowing them to record television programs onto a hard disk much like the digital video recorder (DVR) does.
JTAG is an industry standard for verifying designs and testing printed circuit boards after manufacture.

MIFARE is a series of integrated circuit (IC) chips used in contactless smart cards and proximity cards.
Java Card OpenPlatform (JCOP) is a smart card operating system for the Java Card platform developed by IBM Zürich Research Laboratory. On 31 January 2006 the development and support responsibilities transferred to the IBM Smart Card Technology team in Böblingen, Germany. Since July 2007 support and development activities for the JCOP operating system on NXP / Philips silicon are serviced by NXP Semiconductors.
HID Global is an American manufacturer of secure identity products. The company is an independent brand of Assa Abloy, a Swedish door and access control conglomerate. Björn Lidefelt was appointed CEO on 27 January 2020. He succeeded Stefan Widing, who led HID Global for over four years.

Minimig is an open source re-implementation of an Amiga 500 using a field-programmable gate array (FPGA).
RuBee is a two-way active wireless protocol designed for harsh environments and high-security asset visibility applications. RuBee utilizes longwave signals to send and receive short data packets in a local regional network. The protocol is similar to the IEEE 802 protocols in that RuBee is networked by using on-demand, peer-to-peer, and active radiating transceivers. RuBee is different in that it uses a low frequency (131 kHz) carrier. One result is that RuBee is slow compared to other packet-based network data standards (Wi-Fi). 131 kHz as an operating frequency provides RuBee with the advantages of ultra-low power consumption and normal operation near steel and/or water. These features make it easy to deploy sensors, controls, or even actuators and indicators.

Crypto1 is a proprietary encryption algorithm and authentication protocol created by NXP Semiconductors for its MIFARE Classic RFID contactless smart cards launched in 1994. Such cards have been used in many notable systems, including Oyster card, CharlieCard and OV-chipkaart.
MIFARE4Mobile is a technical specification published by NXP Semiconductors in December 2008 to manage MIFARE-based applications in mobile devices. The specification provides mobile network operators and service providers with a single, interoperable programming interface, easing the use of the contactless MIFARE technology in future mobile Near Field Communication (NFC) devices.

The YubiKey is a hardware authentication device manufactured by Yubico to protect access to computers, networks, and online services that supports one-time passwords (OTP), public-key cryptography, and authentication, and the Universal 2nd Factor (U2F) and FIDO2 protocols developed by the FIDO Alliance. It allows users to securely log into their accounts by emitting one-time passwords or using a FIDO-based public/private key pair generated by the device. YubiKey also allows for storing static passwords for use at sites that do not support one-time passwords. Google, Amazon, Microsoft, Twitter, and Facebook use YubiKey devices to secure employee accounts as well as end user accounts. Some password managers support YubiKey. Yubico also manufactures the Security Key, a similar lower cost device with only FIDO2/WebAuthn and FIDO/U2F support.

Karsten Nohl is a German cryptography expert and hacker. His areas of research include Global System for Mobile Communications (GSM) security, radio-frequency identification (RFID) security, and privacy protection.

Flipper Zero is a portable Tamagotchi-like multi-functional device developed for interaction with access control systems. The device is able to read, copy, and emulate RFID and NFC tags, radio remotes, iButton, and digital access keys, along with a GPIO interface. It was first announced in August 2020 through the Kickstarter crowdfunding campaign, which raised $4.8 million. The first devices were delivered to backers 18 months after completion of the crowdfunding campaign. The device's user interface embodies a pixel-art dolphin virtual pet. The interaction with the virtual pet is the device's core game mechanic. The usage of the device's functions defines the appearance and emotions of the pet.

















