Related Research Articles

A SIM card is an integrated circuit (IC) intended to securely store the international mobile subscriber identity (IMSI) number and its related key, which are used to identify and authenticate subscribers on mobile telephony devices. Technically the actual physical card is known as a universal integrated circuit card (UICC); this smart card is usually made of PVC with embedded contacts and semiconductors, with the SIM as its primary component. In practise the term "SIM card" refers to the entire unit and not simply the IC.

Near-field communication (NFC) is a set of communication protocols that enables communication between two electronic devices over a distance of 4 cm or less. NFC offers a low-speed connection through a simple setup that can be used to bootstrap more-capable wireless connections. Like other "proximity card" technologies, NFC is based on inductive coupling between two so-called antennas present on NFC-enabled devices—for example a smartphone and a printer—communicating in one or both directions, using a frequency of 13.56 MHz in the globally available unlicensed radio frequency ISM band using the ISO/IEC 18000-3 air interface standard at data rates ranging from 106 to 424 kbit/s.

The universal integrated circuit card (UICC) is the smart card used in mobile terminals in GSM and UMTS networks. The UICC ensures the integrity and security of all kinds of personal data, and it typically holds a few hundred kilobytes. The official definition for UICC is found in ETSI TR 102 216, where it is defined as a "smart card that conforms to the specifications written and maintained by the ETSI Smart Card Platform project". In addition, the definition has a note that states that "UICC is neither an abbreviation nor an acronym". NIST SP 800-101 Rev. 1 and NIST Computer Security Resource Center Glossary state that, "A UICC may be referred to as a SIM, USIM, RUIM or CSIM, and is used interchangeably with those terms", though this is an over-simplification. The primary component of a UICC is a SIM card.
Java Card is a software technology that allows Java-based applications (applets) to be run securely on smart cards and more generally on similar secure small memory footprint deviceswhich are called “secure elements” (SE). Today, a Secure Element is not limited to its smart cards and other removable cryptographic tokens form factors; embedded SEs soldered onto a device board and new security designs embedded into general purpose chips are also widely used. Java Card addresses this hardware fragmentation and specificities while retaining code portability brought forward by Java.
Java Card OpenPlatform (JCOP) is a smart card operating system for the Java Card platform developed by IBM Zürich Research Laboratory. On 31 January 2006 the development and support responsibilities transferred to the IBM Smart Card Technology team in Böblingen, Germany. Since July 2007 support and development activities for the JCOP operating system on NXP / Philips silicon are serviced by NXP Semiconductors.

Trusted Platform Module is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys. The term can also refer to a chip conforming to the standard.
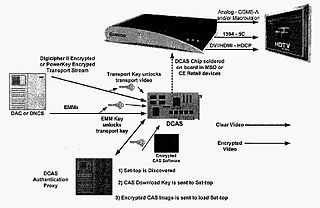
Downloadable Conditional Access System or DCAS was a proposal advanced by CableLabs for secure software download of a specific Conditional Access client which controls digital rights management (DRM) into an OCAP-compliant host consumer media device. The National Cable & Telecommunications Association (NCTA) proposed that DCAS be used as a substitute for physical CableCARDs, a standard also created by CableLabs for which products began appearing in August 2004 as part of industry compliance to the FCC mandate, which in turn is pursuant to the Telecommunications Act of 1996. DCAS is growing in popularity as a less expensive alternative for CableCARD, with major North American operator deployments from Cablevision and Charter. DCAS deployments can be expected to grow in the coming years, thanks to favorable regulatory view from the STELA Reauthorization Act of 2014 and FCC appointing a Downloadable Security Technical Advisory Committee, and wider support for key ladder (K-LAD) functionality from system-on-chip (SoC) vendors and set-top box manufacturers.
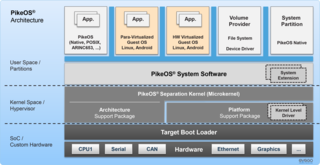
PikeOS is a commercial, hard real-time operating system (RTOS) that offers a separation kernel based hypervisor with multiple logical partition types for many other operating systems (OS), each called a GuestOS, and applications. It enables users to build certifiable smart devices for the Internet of things (IoT) according to the high quality, safety and security standards of different industries. For safety and security critical real-time applications on controller-based systems without memory management unit (MMU) but with memory protection unit (MPU) PikeOS for MPU is available.
A mobile signature is a digital signature generated either on a mobile phone or on a SIM card on a mobile phone.

Contactless payment systems are credit cards and debit cards, key fobs, smart cards, or other devices, including smartphones and other mobile devices, that use radio-frequency identification (RFID) or near-field communication for making secure payments. The embedded integrated circuit chip and antenna enable consumers to wave their card, fob, or handheld device over a reader at the point of sale terminal. Contactless payments are made in close physical proximity, unlike other types of mobile payments which use broad-area cellular or WiFi networks and do not involve close physical proximity.
Digital Security refers to various ways of protecting a computer's internet account and files from intrusion by an outside user or a hacker.
MIFARE4Mobile is a technical specification published by NXP Semiconductors in December 2008 to manage MIFARE-based applications in mobile devices. The specification provides mobile network operators and service providers with a single, interoperable programming interface, easing the use of the contactless MIFARE technology in future mobile Near Field Communication (NFC) devices.
InterChip USB (IC-USB), sometimes referred to as USB-IC or Inter-chip USB, is an addendum to the USB Implementers Forum (USB-IF) USB 2.0 specification. IC-USB is intended as a low-power variant of the standard physical USB interface, intended for direct chip-to-chip communications. The IC-USB bus's maximum length of 10 cm results in a lower inductance and capacitance and therefore allows lower power requirements. IC-USB is used primarily in embedded systems; for example, ETSI has standardized on IC-USB as the official high-speed interface for connections between the main chipset of a smartphone and the SIM card or UICC card.
The (U)SIM interface is the connecting point of the mobile phone and the UICC with its SIM or USIM application.
Payanywhere is a payments platform that allows business owners in the United States to accept credit and debit card payments in-store, online, and on the go. Merchants may accept payments on their smartphone or tablet via a Bluetooth credit card reader, or on a Payanywhere Smart Solution. Payanywhere offers an app and credit card readers that are compatible with both Apple iOS and Android devices.
A trusted execution environment (TEE) is a secure area of a main processor. It guarantees code and data loaded inside to be protected with respect to confidentiality and integrity, Data integrity — prevents unauthorized entities from altering data when any entity outside the TEE processes data, Code integrity — the code in the TEE cannot be replaced or modified by unauthorized entities, which may also be the computer owner itself as in certain DRM schemes described in SGX. This is done by implementing unique, immutable, and confidential architectural security such as Intel® Software Guard Extensions which offers hardware-based memory encryption that isolates specific application code and data in memory. Intel® SGX allows user-level code to allocate private regions of memory, called enclaves, which are designed to be protected from processes running at higher privilege levels. A TEE as an isolated execution environment provides security features such as isolated execution, integrity of applications executing with the TEE, along with confidentiality of their assets. In general terms, the TEE offers an execution space that provides a higher level of security for trusted applications running on the device than a rich operating system (OS) and more functionality than a 'secure element' (SE).
Host card emulation (HCE) is the software architecture that provides exact virtual representation of various electronic identity cards using only software. Prior to the HCE architecture, near field communication (NFC) transactions were mainly carried out using hardware-based secure elements.

An eSIM (embedded-SIM) is a form of programmable SIM card that is embedded directly into a device. Instead of an integrated circuit located on a removable universal integrated circuit card (UICC), typically made of PVC, an eSIM consists of software installed onto an eUICC chip permanently attached to a device.
Remote SIM provisioning is a specification realized by GSMA that allows consumers to remotely activate the subscriber identity module (SIM) embedded in a portable device such as a smart phone, smart watch, fitness band or tablet computer. The specification was originally part of the GSMA's work on eSIM and it is important to note that remote SIM provisioning is just one of the aspects that this eSIM specification includes. The other aspects being that the SIM is now structured into "domains" that separate the operator profile from the security and application "domains". In practise "eSIM upgrade" in the form of a normal SIM card is possible or eSIM can be included into an SOC. The requirement of GSMA certification is that personalisation packet is decoded inside the chip and so there is no way to dump Ki, OPc and 5G keys. Another important aspect is that the eSIM is owned by the enterprise, and this means that the enterprise now has full control of the security and applications in the eSIM, and which operators profiles are to be used.

Platform Security Architecture (PSA) Certified is a security certification scheme for Internet of Things (IoT) hardware, software and devices. It was created by Arm Holdings, Brightsight, CAICT, Prove & Run, Riscure, TrustCB and UL as part of a global partnership.
References
- ↑ Bertrand, Cambou. "Enhancing Secure Elements - Technology and Architecture" (PDF). Northern Arizona University.
- ↑ "What is Secure Element?". Kaspersky.
- ↑ "Security IC Platform Protection Profile with Augmentation Packages" (PDF). Common Criteria.
- ↑ "Worldwide Market of Secure Elements Confirms its Resiliency in 2021". Eurosmart.
- ↑ Lee, Nicole (June 6, 2013). "SD Association adds secure NFC support to its smartSD memory cards". Engadget.
- ↑ Mehta, Tushar (April 4, 2022). "What is Integrated SIM (iSIM)? How is it better than eSIM?". Digital Trends.
- ↑ Page, Carly (October 5, 2021). "Yubico's new hardware key features a fingerprint reader for passwordless logins". TechCrunch.
- 1 2 "The Open Application Platform for Secure Elements" (PDF). Oracle.
- ↑ "How Apple Pay keeps users' purchases protected". Apple.
- ↑ "Samsung Elevates Data Protection for Mobile Devices with New Security Chip Solution". Samsung. May 26, 2020.
- ↑ "Smart Cards; Remote APDU structure for UICC based applications (Release 12)" (PDF). ETSI.
- ↑ "GlobalPlatform Technology Secure Element Protection Profile Version 1.0" (PDF). Common Criteria.