Related Research Articles

SOAP is a messaging protocol specification for exchanging structured information in the implementation of web services in computer networks. It uses XML Information Set for its message format, and relies on application layer protocols, most often Hypertext Transfer Protocol (HTTP), although some legacy systems communicate over Simple Mail Transfer Protocol (SMTP), for message negotiation and transmission.
The Organization for the Advancement of Structured Information Standards is a nonprofit consortium that works on the development, convergence, and adoption of open standards for cybersecurity, blockchain, Internet of things (IoT), emergency management, cloud computing, legal data exchange, energy, content technologies, and other areas.
XML Signature defines an XML syntax for digital signatures and is defined in the W3C recommendation XML Signature Syntax and Processing. Functionally, it has much in common with PKCS #7 but is more extensible and geared towards signing XML documents. It is used by various Web technologies such as SOAP, SAML, and others.
Security Assertion Markup Language is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is an XML-based markup language for security assertions. SAML is also:
XML Key Management Specification (XKMS) uses the web services framework to make it easier for developers to secure inter-application communication using public key infrastructure (PKI). XML Key Management Specification is a protocol developed by W3C which describes the distribution and registration of public keys. Services can access an XKMS compliant server in order to receive updated key information for encryption and authentication.
SOA security addresses the issue of combining services in a service-oriented architecture (SOA) in a secure manner. These issues arise as an effect of the main premise of SOA, which is to erase application boundaries and technology differences. Prior to the application of SOA methodologies, security models have traditionally been hardcoded into applications, and when capabilities of an application are opened up for use by other applications, the existing built-in security models may not be good enough.

Apache Axis2 is a web service engine. It is a redesign and re-write of the widely used Apache Axis SOAP stack. Implementations of Axis2 are available in Java and C.
Security Assertion Markup Language (SAML) is an XML standard for exchanging authentication and authorization data between security domains. SAML is a product of the OASIS (organization) Security Services Technical Committee.
Security Assertion Markup Language 2.0 (SAML 2.0) is a version of the SAML standard for exchanging authentication and authorization identities between security domains. SAML 2.0 is an XML-based protocol that uses security tokens containing assertions to pass information about a principal between a SAML authority, named an Identity Provider, and a SAML consumer, named a Service Provider. SAML 2.0 enables web-based, cross-domain single sign-on (SSO), which helps reduce the administrative overhead of distributing multiple authentication tokens to the user. SAML 2.0 was ratified as an OASIS Standard in March 2005, replacing SAML 1.1. The critical aspects of SAML 2.0 are covered in detail in the official documents SAMLCore, SAMLBind, SAMLProf, and SAMLMeta.
Web Services Enhancements (WSE) is an obsolete add-on to the Microsoft .NET Framework, which includes a set of classes that implement additional WS-* web service specifications chiefly in areas such as security, reliable messaging, and sending attachments. Web services are business logic components which provide functionality via the Internet using standard protocols such as HTTP. Web services communicate via either SOAP or REST messages. WSE provides extensions to the SOAP protocol and allows the definition of custom security, reliable messaging, policy, etc. Developers can add these capabilities at design time using code or at deployment time through the use of a policy file.
WS-Trust is a WS-* specification and OASIS standard that provides extensions to WS-Security, specifically dealing with the issuing, renewing, and validating of security tokens, as well as with ways to establish, assess the presence of, and broker trust relationships between participants in a secure message exchange.
WS-SecurityPolicy is a web services specification, created by IBM and 12 co-authors, that has become an OASIS standard as of version 1.2. It extends the fundamental security protocols specified by the WS-Security, WS-Trust and WS-SecureConversation by offering mechanisms to represent the capabilities and requirements of web services as policies. Security policy assertions are based on the WS-Policy framework.
WS-SecureConversation is a Web Services specification, created by IBM and others, that works in conjunction with WS-Security, WS-Trust and WS-Policy to allow the creation and sharing of security contexts. Extending the use cases of WS-Security, the purpose of WS-SecureConversation is to establish security contexts for multiple SOAP message exchanges, reducing the overhead of key establishment.
The Microsoft Open Specification Promise is a promise by Microsoft, published in September 2006, to not assert its patents, in certain conditions, against implementations of a certain list of specifications.
AS4 is an open standard for the secure and payload-agnostic exchange of Business-to-business documents using Web services. Secure document exchange is governed by aspects of WS-Security, including XML Encryption and XML Digital Signatures. Payload agnosticism refers to the document type not being tied to any defined SOAP action or operation.
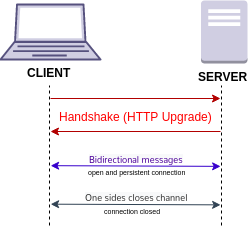
WebSocket is a computer communications protocol, providing full-duplex communication channels over a single TCP connection. The WebSocket protocol was standardized by the IETF as RFC 6455 in 2011. The current API specification allowing web applications to use this protocol is known as WebSockets. It is a living standard maintained by the WHATWG and a successor to The WebSocket API from the W3C.
Electronic Business using eXtensible Markup Language, commonly known as e-business XML, or ebXML as it is typically referred to, is a family of XML based standards sponsored by OASIS and UN/CEFACT whose mission is to provide an open, XML-based infrastructure that enables the global use of electronic business information in an interoperable, secure, and consistent manner by all trading partners.
WS-Security is a flexible and feature-rich extension to SOAP to apply security to web services. It is a member of the WS-* family of web service specifications and was published by OASIS. Closely related to WS-Security is WS-Trust, also a WS-* specification and OASIS standard that provides extensions to WS-Security.
The SAML metadata standard belongs to the family of XML-based standards known as the Security Assertion Markup Language (SAML) published by OASIS in 2005. A SAML metadata document describes a SAML deployment such as a SAML identity provider or a SAML service provider. Deployments share metadata to establish a baseline of trust and interoperability.
References
- ↑ Sabarnij, Sergej. "Padding Oracle Attacks – breaking theoretical secure cryptosystems in the real world" (PDF). Ruhr Universität Bochum.
- ↑ "Hongbin Liu, Shrideep Pallickara, Geoffrey Fox: Performance of Web Services Security" (PDF). Archived from the original (PDF) on 24 February 2021. Retrieved 12 January 2010.
- ↑ Francois Lascelles, Aaron Flint: WS Security Performance. Secure Conversation versus the X509 Profile
- ↑ Bob Atkinson, et al.: Web Services Security (WS-Security)
- ↑ Bob Atkinson, et al.: Web Services Security (WS-Security)
- ↑ Giovanni Della-Libera, Phillip Hallam-Baker Maryann Hondo: Web Services Security Addendum
- ↑ OASIS Web Services Security TC
- ↑ Web Services Security: SOAP Message Security – Working Draft 13
- ↑ schemas.xmlsoap.org