This article needs additional citations for verification .(May 2015) |
AWF (or Agent.AWF) is a malicious Trojan downloader affecting the Microsoft Windows operating system. [1] [2] [3]
This article needs additional citations for verification .(May 2015) |
AWF (or Agent.AWF) is a malicious Trojan downloader affecting the Microsoft Windows operating system. [1] [2] [3]
This Trojan is considered obsolete, and there are no known variants in the wild.[ citation needed ]
The following operating systems are known to be affected. [1]
Agent.AWF displays virus activity in that it replaces files on a user's computer with a copy of itself, and moves the original, legitimate file to a back sub-folder. It is known to attempt to terminate security software, and the Trojan downloads a backdoor onto the computer, allowing the attacker to further compromise the computer. It is also known to modify the Windows registry.[ citation needed ] Agent.AWF does not spread automatically: it needs an attacking user's intervention in order to reach the affected computer. The means of transmission used include, among others, floppy disks, CD-ROMs, emails with attached files, Internet downloads, FTP, IRC channels, peer-to-peer (P2P) file sharing networks, etc. [1]
During installation, the following files are created, and may be present on a compromised system.[ citation needed ]
Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types.

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.

Windows Update is a Microsoft service for the Windows 9x and Windows NT families of the Microsoft Windows operating system, which automates downloading and installing Microsoft Windows software updates over the Internet. The service delivers software updates for Windows, as well as the various Microsoft antivirus products, including Windows Defender and Microsoft Security Essentials. Since its inception, Microsoft has introduced two extensions of the service: Microsoft Update and Windows Update for Business. The former expands the core service to include other Microsoft products, such as Microsoft Office and Microsoft Expression Studio. The latter is available to business editions of Windows 10 and permits postponing updates or receiving updates only after they have undergone rigorous testing.
A dialer or dialler is an electronic device that is connected to a telephone line to monitor the dialed numbers and alter them to seamlessly provide services that otherwise require lengthy national or international access codes to be dialed. A dialer automatically inserts and modifies the numbers depending on the time of day, country or area code dialed, allowing the user to subscribe to the service providers who offer the best rates. For example, a dialer could be programmed to use one service provider for international calls and another for cellular calls. This process is known as prefix insertion or least cost routing. A line-powered dialer does not need any external power but instead takes the power it needs from the telephone line.
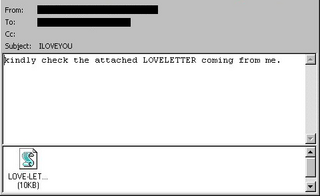
ILOVEYOU, sometimes referred to as the Love Bug or Loveletter, was a computer worm that infected over ten million Windows personal computers on and after 5 May 2000. It started spreading as an email message with the subject line "ILOVEYOU" and the attachment "LOVE-LETTER-FOR-YOU.TXT.vbs". At the time, Windows computers often hid the latter file extension by default because it is an extension for a file type that Windows knows, leading unwitting users to think it was a normal text file. Opening the attachment activates the Visual Basic script. First, the worm inflicts damage on the local machine, overwriting random files, then, it copies itself to all addresses in the Windows Address Book used by Microsoft Outlook, allowing it to spread much faster than any other previous email worm.
Graybird is a Trojan horse that hides its presence on compromised computers and downloads files from remote Web sites. There are many variations of this virus.
Browser hijacking is a form of unwanted software that modifies a web browser's settings without a user's permission, to inject unwanted advertising into the user's browser. A browser hijacker may replace the existing home page, error page, or search engine with its own. These are generally used to force hits to a particular website, increasing its advertising revenue.
The Vundo Trojan is either a Trojan horse or a computer worm that is known to cause popups and advertising for rogue antispyware programs, and sporadically other misbehavior including performance degradation and denial of service with some websites including Google and Facebook. It also is used to deliver other malware to its host computers. Later versions include rootkits and ransomware.

The Storm Worm is a phishing backdoor Trojan horse that affects computers using Microsoft operating systems, discovered on January 17, 2007. The worm is also known as:

Orbit Downloader is a discontinued download manager for Microsoft Windows. Launched in 2006, its developers abandoned it in 2009. In 2013, Orbit Downloader was classified as malware by antivirus software after ESET discovered a botnet in the application.

The Storm botnet or Storm Worm botnet was a remotely controlled network of "zombie" computers that had been linked by the Storm Worm, a Trojan horse spread through e-mail spam. At its height in September 2007, the Storm botnet was running on anywhere from 1 million to 50 million computer systems, and accounted for 8% of all malware on Microsoft Windows computers. It was first identified around January 2007, having been distributed by email with subjects such as "230 dead as storm batters Europe," giving it its well-known name. The botnet began to decline in late 2007, and by mid-2008 had been reduced to infecting about 85,000 computers, far less than it had infected a year earlier.
Koobface is a network worm that attacks Microsoft Windows, Mac OS X, and Linux platforms. This worm originally targeted users of networking websites such as Facebook, Skype, Yahoo Messenger, and email websites such as GMail, Yahoo Mail, and AOL Mail. It also targets other networking websites, such as MySpace, Twitter, and it can infect other devices on the same local network. Technical support scammers also fraudulently claim to their intended victims that they have a Koobface infection on their computer by using fake popups and using built-in Windows programs.
Form grabbing is a form of malware that works by retrieving authorization and log-in credentials from a web data form before it is passed over the Internet to a secure server. This allows the malware to avoid HTTPS encryption. This method is more effective than keylogger software because it will acquire the user’s credentials even if they are input using virtual keyboard, auto-fill, or copy and paste. It can then sort the information based on its variable names, such as email, account name, and password. Additionally, the form grabber will log the URL and title of the website the data was gathered from.
MS Antivirus is a scareware rogue anti-virus which purports to remove virus infections found on a computer running Microsoft Windows. It attempts to scam the user into purchasing a "full version" of the software. The company and the individuals behind Bakasoftware operated under other different 'company' names, including Innovagest2000, Innovative Marketing Ukraine, Pandora Software, LocusSoftware, etc.
Sality is the classification for a family of malicious software (malware), which infects Microsoft Windows systems files. Sality was first discovered in 2003 and has advanced to become a dynamic, enduring and full-featured form of malicious code. Systems infected with Sality may communicate over a peer-to-peer (P2P) network to form a botnet to relay spam, proxying of communications, exfiltrating sensitive data, compromising web servers and/or coordinating distributed computing tasks to process intensive tasks. Since 2010, certain variants of Sality have also incorporated rootkit functions as part of an ongoing evolution of the malware family. Because of its continued development and capabilities, Sality is considered one of the most complex and formidable forms of malware to date.
Slenfbot is the classification for a family of malicious software (malware), which infects files on Microsoft Windows systems. Slenfbot was first discovered in 2007 and, since then, numerous variants have followed; each with slightly different characteristics and new additions to the worm's payload, such as the ability to provide the attacker with unauthorized access to the compromised host. Slenfbot primarily spreads by luring users to follow links to websites, which contain a malicious payload. Slenfbot propagates via instant messaging applications, removable drives and/or the local network via network shares. The code for Slenfbot appears to be closely managed, which may provide attribution to a single group and/or indicate that a large portion of the code is shared amongst multiple groups. The inclusion of other malware families and variants as well as its own continuous evolution, makes Slenfbot a highly effective downloader with a propensity to cause even more damage to compromised systems.
Absolute Home & Office is a proprietary laptop theft recovery software. The persistent security features are built into the firmware of devices. Absolute Home & Office has services of an investigations and recovery team who partners with law enforcement agencies to return laptops to their owners. Absolute Software licensed the name LoJack from the vehicle recovery service LoJack in 2005.
A Trojan:Win32/Agent is the definition of a Trojan downloader, Trojan dropper, or Trojan spy. Its first known detection was January 2018, according to Microsoft Malware Protection Center. Trojans may allow an attacker to access users' personal information such as banking information, passwords, or personal identity. It can also delete a user's files or infect other devices connected to the network. It can be removed by a virus scanning and removal tool such as Microsoft Defender.
Trojan.Win32.DNSChanger is a backdoor trojan that redirects users to various malicious websites through the means of altering the DNS settings of a victim's computer. The malware strain was first discovered by Microsoft Malware Protection Center on December 7, 2006 and later detected by McAfee Labs on April 19, 2009.
The Zealot Campaign is a cryptocurrency mining malware collected from a series of stolen National Security Agency (NSA) exploits, released by the Shadow Brokers group on both Windows and Linux machines to mine cryptocurrency, specifically Monero. Discovered in December 2017, these exploits appeared in the Zealot suite include EternalBlue, EternalSynergy, and Apache Struts Jakarta Multipart Parser attack exploit, or CVE-2017-5638. The other notable exploit within the Zealot vulnerabilities includes vulnerability CVE-2017-9822, known as DotNetNuke (DNN) which exploits a content management system so that the user can install a Monero miner software. An estimated USD $8,500 of Monero having been mined on a single targeted computer. The campaign was discovered and studied extensively by F5 Networks in December 2017.