The Goodtimes virus, also styled as Good Times virus, was a computer virus hoax that spread during the early years of the Internet's popularity. Warnings about a computer virus named "Good Times" began being passed around among Internet users in 1994. The Goodtimes virus was supposedly transmitted via an email bearing the subject header "Good Times" or "Goodtimes", hence the virus's name, and the warning recommended deleting any such email unread. The virus described in the warnings did not exist, but the warnings themselves were, in effect, virus-like. In 1997 the Cult of the Dead Cow hacker collective announced that they had been responsible for the perpetration of the "Good Times" virus hoax as an exercise to "prove the gullibility of self-proclaimed 'experts' on the Internet".
A chain letter is a message that attempts to convince the recipient to make a number of copies and pass them on to a certain number of recipients. The "chain" is an exponentially growing pyramid that cannot be sustained indefinitely.

A hoax is a widely publicised falsehood created to deceive its audience with false and often astonishing information, with the either malicious or humorous intent of causing shock and interest in as many people as possible.

Homestar Runner is an American comedy animated web series and website created by Mike and Matt Chapman, known collectively as The Brothers Chaps. The series centers on the adventures of a large and diverse cast of characters, headed by the titular character, Homestar Runner. It uses a blend of surreal humor, self-parody, satire, and references to popular culture, in particular video games, classic television, and popular music.

Antivirus software, also known as anti-malware, is a computer program used to prevent, detect, and remove malware.
Linux malware includes viruses, Trojans, worms and other types of malware that affect the Linux family of operating systems. Linux, Unix and other Unix-like computer operating systems are generally regarded as very well-protected against, but not immune to, computer viruses.

Email spam, also referred to as junk email, spam mail, or simply spam, is unsolicited messages sent in bulk by email (spamming). The name comes from a Monty Python sketch in which the name of the canned pork product Spam is ubiquitous, unavoidable, and repetitive. Email spam has steadily grown since the early 1990s, and by 2014 was estimated to account for around 90% of total email traffic.
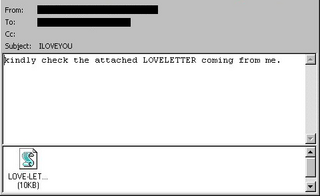
ILOVEYOU, sometimes referred to as the Love Bug or Loveletter, was a computer worm that infected over ten million Windows personal computers on and after 5 May 2000. It started spreading as an email message with the subject line "ILOVEYOU" and the attachment "LOVE-LETTER-FOR-YOU.TXT.vbs". At the time, Windows computers often hid the latter file extension by default because it is an extension for a file type that Windows knows, leading unwitting users to think it was a normal text file. Opening the attachment activates the Visual Basic script. First, the worm inflicts damage on the local machine, overwriting random files, then, it copies itself to all addresses in the Windows Address Book used by Microsoft Outlook, allowing it to spread much faster than any other previous email worm.
Ransomware is a type of malware that permanently blocks access to the victim's personal data unless a "ransom" is paid. While some simple ransomware may lock the system without damaging any files, more advanced malware uses a technique called cryptoviral extortion. It encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. In a properly implemented cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem, and difficult-to-trace digital currencies such as paysafecard or Bitcoin and other cryptocurrencies are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
Tuxissa is a fictional computer virus hoax made up by Humorix, a humor website on Linux.
Cryptovirology refers to the study of cryptography use in malware, such as ransomware and asymmetric backdoors. Traditionally, cryptography and its applications are defensive in nature, and provide privacy, authentication, and security to users. Cryptovirology employs a twist on cryptography, showing that it can also be used offensively. It can be used to mount extortion based attacks that cause loss of access to information, loss of confidentiality, and information leakage, tasks which cryptography typically prevents.
A computer virus hoax is a message warning the recipients of a non-existent computer virus threat. The message is usually a chain e-mail that tells the recipients to forward it to everyone they know, but it can also be in the form of a pop-up window.
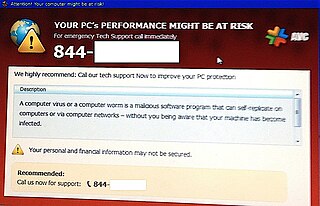
Rogue security software is a form of malicious software and internet fraud that misleads users into believing there is a virus on their computer and aims to convince them to pay for a fake malware removal tool that actually installs malware on their computer. It is a form of scareware that manipulates users through fear, and a form of ransomware. Rogue security software has been a serious security threat in desktop computing since 2008. An early example that gained infamy was SpySheriff and its clones, such as Nava Shield.

April Fools' Day or All Fools' Day is an annual custom on 1 April consisting of practical jokes and hoaxes. Jokesters often expose their actions by shouting "April Fools!" at the recipient. Mass media can be involved with these pranks, which may be revealed as such the following day. The custom of setting aside a day for playing harmless pranks upon one's neighbour has been relatively common in the world historically.

Swatting is a criminal harassment act of deceiving an emergency service into sending a police or emergency service response team to another person's address. This is triggered by false reporting of a serious law enforcement emergency, such as a bomb threat, murder, hostage situation, or a false report of a mental health emergency, such as reporting that a person is suicidal or homicidal and may be armed, among other things.
Koobface is a network worm that attacks Microsoft Windows, Mac OS X, and Linux platforms. This worm originally targeted users of networking websites such as Facebook, Skype, Yahoo Messenger, and email websites such as GMail, Yahoo Mail, and AOL Mail. It also targets other networking websites, such as MySpace, Twitter, and it can infect other devices on the same local network. Technical support scammers also fraudulently claim to their intended victims that they have a Koobface infection on their computer by using fake popups and using built-in Windows programs.
The Pikachu virus, also referred to as Pokey or the Pokémon virus, was a computer worm believed to be the first malware geared at children, due to its incorporation of Pikachu, the mascot species of the Pokémon media franchise. It was considered similar to the Love Bug, albeit slower in its spread and less dangerous.
Zeus is a Trojan horse malware package that runs on versions of Microsoft Windows. It is often used to steal banking information by man-in-the-browser keystroke logging and form grabbing. Zeus is spread mainly through drive-by downloads and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation, it became more widespread in March 2009. In June 2009 security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on websites of such companies as the Bank of America, NASA, Monster.com, ABC, Oracle, Play.com, Cisco, Amazon, and BusinessWeek. Similarly to Koobface, Zeus has also been used to trick victims of technical support scams into giving the scam artists money through pop-up messages that claim the user has a virus, when in reality they might have no viruses at all. The scammers may use programs such as Command prompt or Event viewer to make the user believe that their computer is infected.
Mac Defender is an internet rogue security program that targets computers running macOS. The Mac security firm Intego discovered the fake antivirus software on 2 May 2011, with a patch not being provided by Apple until 31 May. The software has been described as the first major malware threat to the Macintosh platform. However, it is not the first Mac-specific Trojan, and is not self-propagating.

A technical support scam, or tech support scam, is a type of scam in which a scammer claims to offer a legitimate technical support service. Victims contact scammers in a variety of ways, often through fake pop-ups resembling error messages or via fake "help lines" advertised on websites owned by the scammers. Technical support scammers use social engineering and a variety of confidence tricks to persuade their victim of the presence of problems on their computer or mobile device, such as a malware infection, when there are no issues with the victim's device. The scammer will then persuade the victim to pay to fix the fictitious "problems" that they claim to have found. Payment is made to the scammer via gift cards, which are hard to trace and have few consumer protections in place. Technical support scams have occurred as early as 2008. A 2017 study of technical support scams found that of the IPs that could be geolocated, 85% could be traced to locations in India, 7% to locations in the United States and 3% to locations in Costa Rica. Research into tech support scams suggests that millennials and those in generation Z have the highest exposure to such scams; however, senior citizens are more likely to fall for these scams and lose money to them. Technical support scams were named by Norton as the top phishing threat to consumers in October 2021; Microsoft found that 60% of consumers who took part in a survey had been exposed to a technical support scam within the previous twelve months. Responses to technical support scams include lawsuits brought against companies responsible for running fraudulent call centres and scam baiting.








