Related Research Articles
Adware, often called advertising-supported software by its developers, is software that generates revenue for its developer by automatically generating online advertisements in the user interface of the software or on a screen presented to the user during the installation process. The software may generate two types of revenue: one is for the display of the advertisement and another on a "pay-per-click" basis, if the user clicks on the advertisement. Some advertisements also act as spyware, collecting and reporting data about the user, to be sold or used for targeted advertising or user profiling. The software may implement advertisements in a variety of ways, including a static box display, a banner display, a full screen, a video, a pop-up ad or in some other form. All forms of advertising carry health, ethical, privacy and security risks for users.
Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types.
Spyware is any software with malicious behavior that aims to gather information about a person or organization and send it to another entity in a way that harms the user by violating their privacy, endangering their device's security, or other means. This behavior may be present in malware and in legitimate software. Websites may engage in spyware behaviors like web tracking. Hardware devices may also be affected.
In computing, a Trojan horse is any malware that misleads users of its true intent by disguising itself as a standard program. The term is derived from the ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy.
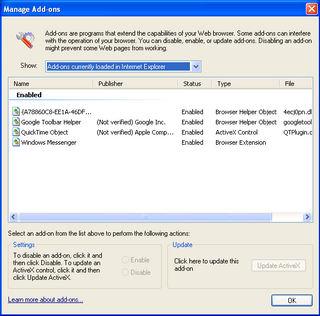
A Browser Helper Object (BHO) is a DLL module designed as a plugin for the Microsoft Internet Explorer web browser to provide added functionality. BHOs were introduced in October 1997 with the release of version 4 of Internet Explorer. Most BHOs are loaded once by each new instance of Internet Explorer. However, in the case of Windows Explorer, a new instance is launched for each window.
PDFCreator is an application for converting documents into Portable Document Format (PDF) format on Microsoft Windows operating systems. It works by creating a virtual printer that prints to PDF files, and thereby allows practically any application to create PDF files by choosing to print from within the application and then printing to the PDFCreator printer.
Browser hijacking is a form of unwanted software that modifies a web browser's settings without a user's permission, to inject unwanted advertising into the user's browser. A browser hijacker may replace the existing home page, error page, or search engine with its own. These are generally used to force hits to a particular website, increasing its advertising revenue.

FrostWire is a free and open-source BitTorrent client first released in September 2004, as a fork of LimeWire. It was initially very similar to LimeWire in appearance and functionality, but over time developers added more features, including support for the BitTorrent protocol. In version 5, support for the Gnutella network was dropped entirely, and FrostWire became a BitTorrent-only client.

Zango,, formerly ePIPO, 180solutions and Hotbar, was a software company that provided users access to its partners' videos, games, tools and utilities in exchange for viewing targeted advertising placed on their computers. Zango software is listed as adware by Symantec, and is also labeled as a potentially unwanted program by McAfee. Zango was co-founded by two brothers: Keith Smith, who served as the CEO; and Ken Smith, who served as the CTO.
Google Pack was a collection of software tools offered by Google to download in a single archive. It was announced at the 2006 Consumer Electronics Show, on January 6. Google Pack was only available for Windows XP, Windows Vista, and Windows 7.
The Vundo Trojan is either a Trojan horse or a computer worm that is known to cause popups and advertising for rogue antispyware programs, and sporadically other misbehavior including performance degradation and denial of service with some websites including Google and Facebook. It also is used to deliver other malware to its host computers. Later versions include rootkits and ransomware.
Rogue security software is a form of malicious software and internet fraud that misleads users into believing there is a virus on their computer and aims to convince them to pay for a fake malware removal tool that actually installs malware on their computer. It is a form of scareware that manipulates users through fear, and a form of ransomware. Rogue security software has been a serious security threat in desktop computing since 2008. An early example that gained infamy was SpySheriff and its clones, such as Nava Shield.
A browser toolbar is a toolbar that resides within a browser's window. All major web browsers provide support to browser toolbar development as a way to extend the browser's GUI and functionality. Browser toolbars are considered to be a particular kind of browser extensions that present a toolbar. Browser toolbars are specific to each browser, which means that a toolbar working on a browser does not work on another one. All browser toolbars must be installed in the corresponding browser before they can be used and require updates when new versions are released.

Malwarebytes Inc. is an American Internet security company that specializes in protecting home computers, smartphones, and companies from malware and other threats. It has offices in Santa Clara, California; Clearwater, Florida; Tallinn, Estonia; Bastia Umbra, Italy; and Cork, Ireland.

Genieo Innovation is an Israeli company, specializing in unwanted software which includes advertising and user tracking software, commonly referred to as a potentially unwanted program, adware, privacy-invasive software, grayware, or malware. They are best known for Genieo, an application of this type. They also own and operate InstallMac which distributes additional 'optional' search modifying software with other applications. In 2014, Genieo Innovation was acquired for $34 million by Somoto, another company which "bundles legitimate applications with offers for additional third party applications that may be unwanted by the user". This sector of the Israeli software industry is frequently referred to as Download Valley.
PUM.bad.proxy is a form of malware known as a "registry hack", an unauthorized alteration to the Windows Registry file that specifically redirects LAN settings within Internet Explorer, the popular web browser commonly installed as the default web browser for Microsoft Windows. First spotted by users of Malwarebytes' Anti-Malware security software on 22 January 2011, it was reported to Malwarebytes Software over 200 times the first day alone.

Torch was a Chromium-based web browser and Internet suite developed by the North Carolina–based Torch Media. As of November 2022, downloads for Torch are no longer available, and upon clicking the download button, users are redirected to the Torch Search extension on the Chrome Web Store.
Download Valley is a cluster of software companies in Israel, producing and delivering adware to be installed alongside downloads of other software. The primary purpose is to monetize shareware and downloads. These software items are commonly browser toolbars, adware, browser hijackers, spyware, and malware. Another group of products are download managers, possibly designed to induce or trick the user to install adware, when downloading a piece of desired software or mobile app from a certain source.
A potentially unwanted program (PUP) or potentially unwanted application (PUA) is software that a user may perceive as unwanted or unnecessary. It is used as a subjective tagging criterion by security and parental control products. Such software may use an implementation that can compromise privacy or weaken the computer's security. Companies often bundle a wanted program download with a wrapper application and may offer to install an unwanted application, and in some cases without providing a clear opt-out method. Antivirus companies define the software bundled as potentially unwanted programs which can include software that displays intrusive advertising (adware), or tracks the user's Internet usage to sell information to advertisers (spyware), injects its own advertising into web pages that a user looks at, or uses premium SMS services to rack up charges for the user. A growing number of open-source software projects have expressed dismay at third-party websites wrapping their downloads with unwanted bundles, without the project's knowledge or consent. Nearly every third-party free download site bundles their downloads with potentially unwanted software. The practice is widely considered unethical because it violates the security interests of users without their informed consent. Some unwanted software bundles install a root certificate on a user's device, which allows hackers to intercept private data such as banking details, without a browser giving security warnings. The United States Department of Homeland Security has advised removing an insecure root certificate, because they make computers vulnerable to serious cyberattacks. Software developers and security experts recommend that people always download the latest version from the official project website, or a trusted package manager or app store.
WiperSoft is an anti-spyware program developed by Wiper Software. It is designed to help users protect their computers from such threats as adware, browser hijackers, worms, potentially unwanted programs (PUPs), trojans, and viruses. Currently available only for Microsoft Windows.
References
- ↑ Valeros, Maria Eleanor E. "Meet Paperghost - the ethical hacker". Philstar.com.
- ↑ "Paperghost is now Haunting Malwarebytes!" . Retrieved 6 December 2013.
- ↑ Leyden, John (22 November 2004). "Bofra exploit tied to 'massive botnet'".
- ↑ "Alternative Browsers and Java Lead Spyware to IE".
- ↑ "Fake Private Videos Offer Surveys, EXEs and .XPI Installs | Malwarebytes Labs". Malwarebytes. 31 July 2014.
- ↑ "Facebook profile viewer scams meddle with Firefox and Chrome browsers". Graham Cluley. 4 July 2013.
- ↑ "Spyware Floods In Through BitTorrent".
- ↑ "GFI LABS Blog".
- ↑ Dvorak, John C. (2005-06-20). "The Scheme to Discredit BitTorrent". PC Magazine.
- ↑ "There Is No Conspiracy Against BitTorrent".
- ↑ "P2P Downloads Fuel Spyware".
- ↑ "Fake Google Toolbars Go Phishing".
- ↑ "AIM Rootkit Attack Traced to Middle East".
- ↑ "Botnet Uses BitTorrent to Push Movie Files".
- ↑ "Zango - Zealot or Fanatic". Archived from the original on 2006-01-28.
- ↑ Brazen Botnets Steal From E-Shopping Carts - Security Technology News by TechWeb
- ↑ "GFI LABS Blog".
- ↑ Techworld.com - Hijack browser installed by new worm
- ↑ Zango Blasted For Targeting MySpace As Adware Channel – News – InformationWeek
- ↑ Researchers Watch AIM Bot Being Built – Security Technology News by TechWeb
- ↑ "Botnet Tactics Enable Click Fraud - SecurityProNews".
- ↑ MySpace worm exploits QuickTime feature | InfoWorld | News | 2006-12-04 | By Jeremy Kirk, IDG News Service Archived 2006-12-10 at the Wayback Machine