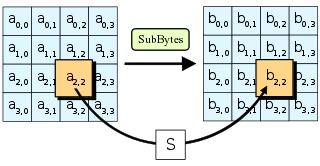
The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
The U.S. National Security Agency (NSA) ranks cryptographic products or algorithms by a certification called product types. Product types are defined in the National Information Assurance Glossary which defines Type 1, 2, 3, and 4 products.

A secure cryptoprocessor is a dedicated computer-on-a-chip or microprocessor for carrying out cryptographic operations, embedded in a packaging with multiple physical security measures, which give it a degree of tamper resistance. Unlike cryptographic processors that output decrypted data onto a bus in a secure environment, a secure cryptoprocessor does not output decrypted data or decrypted program instructions in an environment where security cannot always be maintained.
_NSAKEY was a variable name discovered in an operating system from Microsoft in 1999. The variable contained a 1024-bit public key; such keys are used in cryptography for encryption and authentication. Due to the name it was speculated that the key was owned by the United States National Security Agency which would allow the intelligence agency to subvert any Windows user's security. Microsoft denied the speculation and said that the key's name came from the NSA being the technical review authority for U.S. cryptography export controls.
The Federal Information Processing Standard Publication 140-2,, is a U.S. government computer security standard used to approve cryptographic modules. The title is Security Requirements for Cryptographic Modules. Initial publication was on May 25, 2001 and was last updated December 3, 2002.

The Cryptographic Module Validation Program (CMVP) is a joint American and Canadian security accreditation program for cryptographic modules. The program is available to any vendors who seek to have their products certified for use by the U.S. Government and regulated industries that collect, store, transfer, share and disseminate "sensitive, but not classified" information. All of the tests under the CMVP are handled by third-party laboratories that are accredited as Cryptographic Module Testing Laboratories by the National Voluntary Laboratory Accreditation Program (NVLAP). Product certifications under the CMVP are performed in accordance with the requirements of FIPS 140-2.
The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S. Federal Information Processing Standard (FIPS), including:

TLS acceleration is a method of offloading processor-intensive public-key encryption for Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL) to a hardware accelerator.
The 140 series of Federal Information Processing Standards (FIPS) are U.S. government computer security standards that specify requirements for cryptography modules. As of December 2016, the current version of the standard is FIPS 140-2, issued on 25 May 2001. Its successor FIPS 140-3 was approved on March 22, 2019 and will become effective on September 22, 2019. FIPS 140-3 testing will begin September 22, 2020. After FIPS 140-3 testing begins, FIPS 140-2 testing will continue for at least a year, making the two standards to coexist for some time.
NSA Suite B Cryptography was a set of cryptographic algorithms promulgated by the National Security Agency as part of its Cryptographic Modernization Program. It was to serve as an interoperable cryptographic base for both unclassified information and most classified information.
The Microsoft Windows platform specific Cryptographic Application Programming Interface is an application programming interface included with Microsoft Windows operating systems that provides services to enable developers to secure Windows-based applications using cryptography. It is a set of dynamically linked libraries that provides an abstraction layer which isolates programmers from the code used to encrypt the data. The Crypto API was first introduced in Windows NT 4.0 and enhanced in subsequent versions.

A hardware security module (HSM) is a physical computing device that safeguards and manages digital keys for strong authentication and provides cryptoprocessing. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server. A hardware security module contains one or more secure cryptoprocessor chips.
NSA Suite A Cryptography is NSA cryptography which "contains classified algorithms that will not be released." "Suite A will be used for the protection of some categories of especially sensitive information ."
In computing, Network Security Services (NSS) comprises a set of libraries designed to support cross-platform development of security-enabled client and server applications with optional support for hardware TLS/SSL acceleration on the server side and hardware smart cards on the client side. NSS provides a complete open-source implementation of cryptographic libraries supporting Transport Layer Security (TLS) / Secure Sockets Layer (SSL) and S/MIME. Previously tri-licensed under the Mozilla Public License 1.1, the GNU General Public License, and the GNU Lesser General Public License, NSS upgraded to GPL-compatible MPL 2.0 with release 3.14.
A Cryptographic Module Testing Laboratory (CMTL) is an information technology (IT) computer security testing laboratory that is accredited to conduct cryptographic module evaluations for conformance to the FIPS 140-2 U.S. Government standard.

Automated teller machines (ATMs) are targets for fraud, robberies and other security breaches. In the past, the main purpose of ATMs was to deliver cash in the form of banknotes, and to debit a corresponding bank account. However, ATMs are becoming more complicated, and they now serve numerous functions, thus becoming a high priority target for robbers and hackers.
The Federal Information Processing Standard (FIPS) Publication 140-3 is an announced update to the U.S. government computer security standard used to accredit cryptographic modules. The title of the standard is Security Requirements for Cryptographic Modules and FIPS 140-2 remains the currently approved version. Efforts to update FIPS 140-2 date back to the early 2000s. The FIPS 140-3 was scheduled for signature by the Secretary of Commerce in August 2013, however that never happened and the draft was subsequently abandoned. In 2014, NIST released a substantially different draft of FIPS 140-3, this version effectively directing the use of an International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) standard, 19790:2012, as the replacement for FIPS 140-2. The 2014 draft of FIPS 140-3 was also abandoned. On August 12, 2015, NIST formally released a statement on the Federal Register asking for comments on the potential use of portions of ISO/IEC 19790:2014 in the update of FIPS 140-2. The reference to a 2014-version of ISO/IEC 19790 was an inadvertent error in the Federal Registry posting, as 2012 is the most recent version.
Crypto++ is a free and open-source C++ class library of cryptographic algorithms and schemes written by Wei Dai. Crypto++ has been widely used in academia, student projects, open source and non-commercial projects, as well as businesses. Released in 1995, the library fully supports 32-bit and 64-bit architectures for many major operating systems and platforms, including Android, Apple, BSD, Cygwin, IBM AIX and S/390, Linux, MinGW, Solaris, Windows, Windows Phone and Windows RT. The project also supports compilation using C++03, C++11 and C++17 runtime libraries; and a variety of compilers and IDEs, including Borland Turbo C++, Borland C++ Builder, Clang, CodeWarrior Pro, GCC, Intel C++ Compiler (ICC), Microsoft Visual C/C++, and Sun Studio.
Utimaco Atalla, founded as Atalla Technovation and formerly known as Atalla Corporation or HP Atalla, is a security vendor, active in the market segments of data security and cryptography. Atalla provides government-grade end-to-end products in network security, and hardware security modules (HSMs) used in automated teller machines (ATMs) and Internet security. The company was founded by Egyptian engineer Mohamed M. Atalla in 1972. Atalla HSMs are the payment card industry's de facto standard, protecting 250 million card transactions daily as of 2013, and securing the majority of the world's ATM transactions as of 2014.

Hardware-based encryption is the use of computer hardware to assist software, or sometimes replace software, in the process of data encryption. Typically, this is implemented as part of the processor's instruction set. For example, the AES encryption algorithm can be implemented using the AES instruction set on the ubiquitous x86 architecture. Such instructions also exist on the ARM architecture. However, more unusual systems exist where the cryptography module is separate from the central processor, instead being implemented as a coprocessor, in particular a secure cryptoprocessor or cryptographic accelerator, of which an example is the IBM 4758, or its successor, the IBM 4764. Hardware implementations can be faster and less prone to exploitation than traditional software implementations, and furthermore can be protected against tampering.






