
In computing, a denial-of-service attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.

A web hosting service is a type of Internet hosting service that allows individuals and organizations to make their website accessible via the World Wide Web. Web hosts are companies that provide space on a server owned or leased for use by clients, as well as providing Internet connectivity, typically in a data center. Web hosts can also provide data center space and connectivity to the Internet for other servers located in their data center, called colocation, also known as housing in Latin America or France.
Network security consists of the policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs: conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: it secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password.

A botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and "network". The term is usually used with a negative or malicious connotation.
Internet security is a branch of computer security specifically related to not only Internet, often involving browser security and the World Wide Web, but also network security as it applies to other applications or operating systems as a whole. Its objective is to establish rules and measures to use against attacks over the Internet. The Internet represents an insecure channel for exchanging information, which leads to a high risk of intrusion or fraud, such as phishing, online viruses, trojans, worms and more.

The Spamhaus Project is an international organisation, based in both London and Geneva, founded in 1998 by Steve Linford to track email spammers and spam-related activity. The name spamhaus, a pseudo-German expression, was coined by Linford to refer to an Internet service provider, or other firm, which spams or knowingly provides service to spammers.
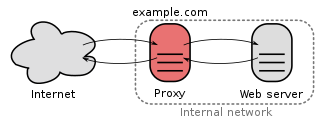
In computer networks, a reverse proxy is a type of proxy server that retrieves resources on behalf of a client from one or more servers. These resources are then returned to the client, appearing as if they originated from the reverse proxy server itself. Unlike a forward proxy, which is an intermediary for its associated clients to contact any server, a reverse proxy is an intermediary for its associated servers to be contacted by any client. In other words, a proxy is associated with the client(s), while a reverse proxy is associated with the server(s); a reverse proxy is usually an internal-facing proxy used as a 'front-end' to control and protect access to a server on a private network.
Distributed denial-of-service attacks on root nameservers are Internet events in which distributed denial-of-service attacks target one or more of the thirteen Domain Name System root nameserver clusters. The root nameservers are critical infrastructure components of the Internet, mapping domain names to IP addresses and other resource record (RR) data.

F5, Inc. is an American company that specializes in application services and application delivery networking (ADN). F5 technologies focus on the delivery, security, performance, and availability of web applications, including the availability of computing, storage, and network resources. F5 is headquartered in Seattle, Washington, with additional development, manufacturing, and administrative offices worldwide.
In networking, black holes refer to places in the network where incoming or outgoing traffic is silently discarded, without informing the source that the data did not reach its intended recipient.
DNS hijacking, DNS poisoning, or DNS redirection is the practice of subverting the resolution of Domain Name System (DNS) queries. This can be achieved by malware that overrides a computer's TCP/IP configuration to point at a rogue DNS server under the control of an attacker, or through modifying the behaviour of a trusted DNS server so that it does not comply with internet standards.
Prolexic Technologies was a US-based provider of security solutions for protecting web sites, data centers, and enterprise IP applications from Distributed Denial of Service (DDoS) attacks at the network, transport, and application layers. It operated a DDoS mitigation platform and a global network of traffic scrubbing centers. Real-time monitoring and mitigation services were provided from a 24/7 security operations control center (SOCC). Prolexic indicated its DDoS mitigation services make websites, data centers and enterprise IP applications harder to take down via DDoS attacks.
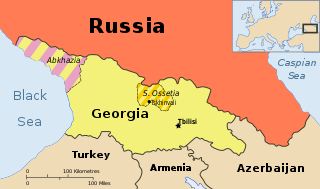
During the Russo-Georgian War a series of cyberattacks swamped and disabled websites of numerous South Ossetian, Georgian, Russian and Azerbaijani organisations. The attacks were initiated three weeks before the shooting war began in what is regarded as "the first case in history of a coordinated cyberspace domain attack synchronized with major combat actions in the other warfighting domains ."

Linode, LLC is an American privately-owned cloud hosting company that provides virtual private servers. It is based in Philadelphia, Pennsylvania.
Imperva Incapsula is an American cloud-based application delivery platform. It uses a global content delivery network to provide web application security, DDoS mitigation, content caching, application delivery, load balancing and failover services.
In computers and computer networks an attack is any attempt to expose, alter, disable, destroy, steal or gain unauthorized access to or make unauthorized use of an asset. A cyberattack is any type of offensive maneuver that targets computer information systems, infrastructures, computer networks, or personal computer devices. An attacker is a person or process that attempts to access data, functions or other restricted areas of the system without authorization, potentially with malicious intent. Depending on context, cyberattacks can be part of cyberwarfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, society or organizations, and it may originate from an anonymous source. A product that facilitates a cyberattack is sometimes called a cyberweapon.
Lizard Squad was a black hat hacking group, mainly known for their claims of distributed denial-of-service (DDoS) attacks primarily to disrupt gaming-related services.
Mirai is a malware that turns networked devices running Linux into remotely controlled bots that can be used as part of a botnet in large-scale network attacks. It primarily targets online consumer devices such as IP cameras and home routers. The Mirai botnet was first found in August 2016 by MalwareMustDie, a white hat malware research group, and has been used in some of the largest and most disruptive distributed denial of service (DDoS) attacks, including an attack on 20 September 2016 on computer security journalist Brian Krebs' web site, an attack on French web host OVH, and the October 2016 Dyn cyberattack. According to a chat log between Anna-senpai and Robert Coelho, Mirai was named after the 2011 TV anime series Mirai Nikki.

The 2016 Dyn cyberattack was a series of distributed denial-of-service attacks on October 21, 2016, targeting systems operated by Domain Name System (DNS) provider Dyn. The attack caused major Internet platforms and services to be unavailable to large swathes of users in Europe and North America. The groups Anonymous and New World Hackers claimed responsibility for the attack, but scant evidence was provided.
The BlackNurse attack is a form of denial of service attack based on ICMP flooding. The attack is special because a modest bandwidth of 20Mbit/s can be effective for disrupting a victim's network.







