Related Research Articles
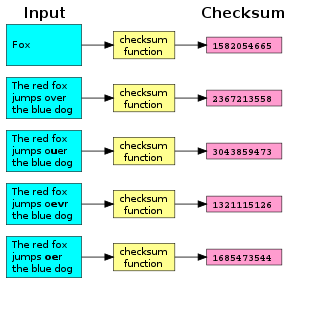
A checksum is a small-sized block of data derived from another block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage. By themselves, checksums are often used to verify data integrity but are not relied upon to verify data authenticity.
LZ77 and LZ78 are the two lossless data compression algorithms published in papers by Abraham Lempel and Jacob Ziv in 1977 and 1978. They are also known as LZ1 and LZ2 respectively. These two algorithms form the basis for many variations including LZW, LZSS, LZMA and others. Besides their academic influence, these algorithms formed the basis of several ubiquitous compression schemes, including GIF and the DEFLATE algorithm used in PNG and ZIP.

In Africa, the Big five game animals are the lion, leopard, rhinoceros, elephant, and African buffalo. The term was coined by big-game hunters to refer to the five most difficult animals in Africa to hunt on foot, but is now more widely used by game viewing tourists and safari tour operators. They are examples of charismatic megafauna, featuring prominently in popular culture, and are among the most famous of Africa's large animals.
The Lempel–Ziv–Markov chain algorithm (LZMA) is an algorithm used to perform lossless data compression. It has been under development since either 1996 or 1998 by Igor Pavlov and was first used in the 7z format of the 7-Zip archiver. This algorithm uses a dictionary compression scheme somewhat similar to the LZ77 algorithm published by Abraham Lempel and Jacob Ziv in 1977 and features a high compression ratio and a variable compression-dictionary size, while still maintaining decompression speed similar to other commonly used compression algorithms.
CipherSaber is a simple symmetric encryption protocol based on the RC4 stream cipher. Its goals are both technical and political: it gives reasonably strong protection of message confidentiality, yet it's designed to be simple enough that even novice programmers can memorize the algorithm and implement it from scratch. According to the designer, a CipherSaber version in the QBASIC programming language takes just sixteen lines of code. Its political aspect is that because it's so simple, it can be reimplemented anywhere at any time, and so it provides a way for users to communicate privately even if government or other controls make distribution of normal cryptographic software completely impossible.
rzip is a huge-scale data compression computer program designed around initial LZ77-style string matching on a 900 MB dictionary window, followed by bzip2-based Burrows–Wheeler transform and entropy coding (Huffman) on 900 kB output chunks.

In computer science, a radix tree is a data structure that represents a space-optimized trie in which each node that is the only child is merged with its parent. The result is that the number of children of every internal node is at most the radix r of the radix tree, where r = 2x for some integer x ≥ 1. Unlike regular trees, edges can be labeled with sequences of elements as well as single elements. This makes radix trees much more efficient for small sets and for sets of strings that share long prefixes.
In Unix-like operating systems, find is a command-line utility that locates files based on some user-specified criteria and either prints the pathname of each matched object or, if another action is requested, performs that action on each matched object.

Frederick Courteney Selous, DSO was a British explorer, officer, professional hunter, and conservationist, famous for his exploits in Southeast Africa. His real-life adventures inspired Sir Henry Rider Haggard to create the fictional character Allan Quatermain. Selous was a friend of Theodore Roosevelt, Cecil Rhodes and Frederick Russell Burnham. He was pre-eminent within a group of big game hunters that included Abel Chapman and Arthur Henry Neumann. He was the older brother of the ornithologist and writer Edmund Selous.

Trophy hunting is a form of hunting for sport in which parts of the hunted wild animals are kept and displayed as trophies. The animal being targeted, known as the "game", is typically a mature male specimen from a popular species of collectable interests, usually of large sizes, holding impressive horns, antlers, furs, or manes. Most trophies consist of only select parts of the animal, which are prepared for display by a taxidermist. The parts most commonly kept vary by species but often include the head, hide, tusks, horns, or antlers.
In computer programming, a sentinel value is a special value in the context of an algorithm which uses its presence as a condition of termination, typically in a loop or recursive algorithm.
A bounding volume hierarchy (BVH) is a tree structure on a set of geometric objects. All geometric objects, which form the leaf nodes of the tree, are wrapped in bounding volumes. These nodes are then grouped as small sets and enclosed within larger bounding volumes. These, in turn, are also grouped and enclosed within other larger bounding volumes in a recursive fashion, eventually resulting in a tree structure with a single bounding volume at the top of the tree. Bounding volume hierarchies are used to support several operations on sets of geometric objects efficiently, such as in collision detection and ray tracing.

In computer science, recursion is a method of solving a computational problem where the solution depends on solutions to smaller instances of the same problem. Recursion solves such recursive problems by using functions that call themselves from within their own code. The approach can be applied to many types of problems, and recursion is one of the central ideas of computer science.
The power of recursion evidently lies in the possibility of defining an infinite set of objects by a finite statement. In the same manner, an infinite number of computations can be described by a finite recursive program, even if this program contains no explicit repetitions.
Intrusion detection system evasion techniques are modifications made to attacks in order to prevent detection by an intrusion detection system (IDS). Almost all published evasion techniques modify network attacks. The 1998 paper Insertion, Evasion, and Denial of Service: Eluding Network Intrusion Detection popularized IDS evasion, and discussed both evasion techniques and areas where the correct interpretation was ambiguous depending on the targeted computer system. The 'fragroute' and 'fragrouter' programs implement evasion techniques discussed in the paper. Many web vulnerability scanners, such as 'Nikto', 'whisker' and 'Sandcat', also incorporate IDS evasion techniques.

Wild Africa is a British nature documentary series created and produced by the BBC. It explores the natural history of the African continent. It was first transmitted on 7 November 2001 on BBC Two in the United Kingdom and comprises six episodes. Each concentrates on a particular environment. The producers use aerial photography and wildlife footage to show how natural phenomena such as seasonal changes influence the patterns of life. Wild Africa was produced by the BBC Natural History Unit and narrated by Fergal Keane.
In mathematical optimization and computer science, heuristic is a technique designed for problem solving more quickly when classic methods are too slow for finding an exact or approximate solution, or when classic methods fail to find any exact solution in a search space. This is achieved by trading optimality, completeness, accuracy, or precision for speed. In a way, it can be considered a shortcut.
bcrypt is a password-hashing function designed by Niels Provos and David Mazières, based on the Blowfish cipher and presented at USENIX in 1999. Besides incorporating a salt to protect against rainbow table attacks, bcrypt is an adaptive function: over time, the iteration count can be increased to make it slower, so it remains resistant to brute-force search attacks even with increasing computation power.
Computer humour, also known as hacker humour, is humour on the subject of computers or their users.

The Knysna elephants were the relicts of once substantial herds of African bush elephant in the Outeniqua/Tsitsikamma region of southernmost South Africa. As of 2022, the herds have been reduced to a lone adult female. The elephant herds roamed the southern tip of Africa into the 19th century and the 20th century, when contact with European farmers and hunters led to their decimation. It is conjectured that about 1,000 elephants historically roamed the Outeniqua/Tsitsikamma area. A 2006 DNA analysis of dung samples revealed the presence of at least 5 cows and possibly some bulls and calves, moving within an area of 121,000 hectares of forest managed by SANParks – the only unfenced elephant group in South Africa. However, by 2019, researchers realised that a mature female at the Knysna Forest was the last to survive.

Elephant meat is the flesh and other edible parts of elephants. Elephants have been hunted for their meat since prehistoric times, with traditional elephant hunting being historically practiced by some modern African hunter-gatherer groups. Elephant meat is also widely illegally sold as bushmeat in parts of Africa, which has sparked concerns that the demand for bushmeat is driving poaching.
References
- 1 2 Olsen, Peter C. (September 1989), "Pachydermic Personnel Prediction", Stop Bit, Byte , p. 404
- ↑ Steuben, Michael (1998). Twenty Years Before the Blackboard. Cambridge University Press. p. 62. ISBN 9780883855256.