The Simple Mail Transfer Protocol (SMTP) is a communication protocol for electronic mail transmission. As an Internet standard, SMTP was first defined in 1982 by RFC 821, and updated in 2008 by RFC 5321 to Extended SMTP additions, which is the protocol variety in widespread use today. Mail servers and other message transfer agents use SMTP to send and receive mail messages. Proprietary systems such as Microsoft Exchange and IBM Notes and webmail systems such as Outlook.com, Gmail and Yahoo! Mail may use non-standard protocols internally, but all use SMTP when sending to or receiving email from outside their own systems. SMTP servers commonly use the Transmission Control Protocol on port number 25.

An open mail relay is an SMTP server configured in such a way that it allows anyone on the Internet to send e-mail through it, not just mail destined to or originating from known users. This used to be the default configuration in many mail servers; indeed, it was the way the Internet was initially set up, but open mail relays have become unpopular because of their exploitation by spammers and worms. Many relays were closed, or were placed on blacklists by other servers.
A Domain Name System-based Blackhole List (DNSBL) or Real-time Blackhole List (RBL) is an effort to stop email spamming. It is a "blacklist" of locations on the Internet reputed to send email spam. The locations consist of IP addresses which are most often used to publish the addresses of computers or networks linked to spamming; most mail server software can be configured to reject or flag messages which have been sent from a site listed on one or more such lists. The term "Blackhole List" is sometimes interchanged with the term "blacklist" and "blocklist".
Various anti-spam techniques are used to prevent email spam.
Sender Policy Framework (SPF) is an email authentication method designed to detect forged sender addresses in emails, a technique often used in phishing and email spam.
Greylisting is a method of defending e-mail users against spam. A mail transfer agent (MTA) using greylisting will "temporarily reject" any email from a sender it does not recognize. If the mail is legitimate, the originating server will try again after a delay, and if sufficient time has elapsed, the email will be accepted.
A bounce message or just "bounce" is an automated message from a mail system, informing the sender of a previous message that that message had not been delivered. The original message is said to have "bounced". More formal terms for bounce message include "Non-Delivery Report" or "Non-Delivery Receipt" (NDR), [Failed] "Delivery Status Notification" (DSN) message, or a "Non-Delivery Notification" (NDN).
Email authentication, or validation, is a collection of techniques aimed at providing verifiable information about the origin of email messages and validating the identities of the any message MTAs who participated in transferring and possibly modifying a message.
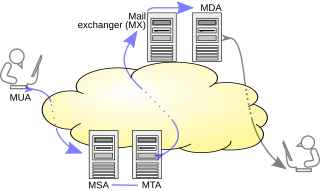
A message submission agent (MSA) or mail submission agent is a computer program or software agent that receives electronic mail messages from a mail user agent (MUA) and cooperates with a mail transfer agent (MTA) for delivery of the mail. It uses ESMTP, a variant of the Simple Mail Transfer Protocol (SMTP), as specified in RFC 6409.
Disposable email addressing, also known as DEA or dark mail, refers to an approach where a unique email address is used for every contact or entity. The benefit is that if anyone compromises the address or utilises it in connection with email abuse, the address owner can easily cancel it without affecting any of their other contacts.
For a mail transfer agent (MTA), the Sender Rewriting Scheme (SRS) is a scheme for rewriting the envelope sender address of an email message, in view of remailing it. In this context, remailing is a kind of email forwarding. SRS was devised in order to forward email without breaking the Sender Policy Framework (SPF), in 2003.
Variable envelope return path (VERP) is a technique used by some electronic mailing list software to enable automatic detection and removal of undeliverable e-mail addresses. It works by using a different return path for each recipient of a message.
Email spoofing is the creation of email messages with a forged sender address.
A smart host or smarthost is an email server via which third parties can send emails and have them forwarded on to the email recipients' email servers.
A challenge–response system is a type of spam filter that automatically sends a reply with a challenge to the (alleged) sender of an incoming e-mail. It was originally designed in 1997 by Stan Weatherby, and was called Email Verification. In this reply, the sender is asked to perform some action to assure delivery of the original message, which would otherwise not be delivered. The action to perform typically takes relatively little effort to do once, but great effort to perform in large numbers. This effectively filters out spammers. Challenge–response systems only need to send challenges to unknown senders. Senders that have previously performed the challenging action, or who have previously been sent e-mail(s) to, would be automatically whitelisted.
A bounce address is an email address to which bounce messages are delivered. There are many variants of the name, none of them used universally, including return path, reverse path, envelope from, envelope sender, MAIL FROM, 5321-FROM, return address, From_, Errors-to, etc. It is not uncommon for a single document to use several of these names.
Invisible mail, also referred to as iMail, i-mail or Bote mail, is a method of exchanging digital messages from an author to one or more recipients in a secure and untraceable way. It is an open protocol and its java implementation (I2P-Bote) is free and open-source software, licensed under the GPLv3.
People tend to be much less bothered by spam slipping through filters into their mail box, than having desired e-mail ("ham") blocked. Trying to balance false negatives vs false positives is critical for a successful anti-spam system. As servers are not able to block all spam there are some tools for individual users to help control over this balance.