
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the German military. The Enigma machine was considered so secure that it was used to encipher the most top-secret messages.

In the history of cryptography, Typex machines were British cipher machines used from 1937. It was an adaptation of the commercial German Enigma with a number of enhancements that greatly increased its security. The cipher machine was used until the mid-1950s when other more modern military encryption systems came into use.

In the history of cryptography, the ECM Mark II was a cipher machine used by the United States for message encryption from World War II until the 1950s. The machine was also known as the SIGABA or Converter M-134 by the Army, or CSP-888/889 by the Navy, and a modified Navy version was termed the CSP-2900.
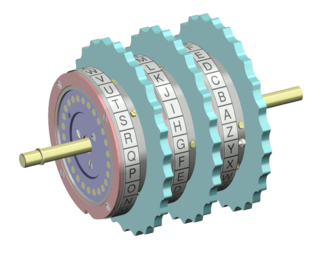
In cryptography, a rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting messages. Rotor machines were the cryptographic state-of-the-art for much of the 20th century; they were in widespread use in the 1920s–1970s. The most famous example is the German Enigma machine, the output of which was deciphered by the Allies during World War II, producing intelligence code-named Ultra.

Hans-Thilo Schmidt codenamed Asché or Source D, was a spy who sold secrets about the German Enigma machine to the French during World War II. The materials he provided facilitated Polish mathematician Marian Rejewski's reconstruction of the wiring in the Enigma's rotors and reflector; thereafter the Poles were able to read a large proportion of Enigma-enciphered traffic.

The bombe was an electro-mechanical device used by British cryptologists to help decipher German Enigma-machine-encrypted secret messages during World War II. The US Navy and US Army later produced their own machines to the same functional specification, albeit engineered differently both from each other and from Polish and British bombes.

The bomba, or bomba kryptologiczna, was a special-purpose machine designed around October 1938 by Polish Cipher Bureau cryptologist Marian Rejewski to break German Enigma-machine ciphers.

In cryptography, the M-209, designated CSP-1500 by the United States Navy is a portable, mechanical cipher machine used by the US military primarily in World War II, though it remained in active use through the Korean War. The M-209 was designed by Swedish cryptographer Boris Hagelin in response to a request for such a portable cipher machine, and was an improvement of an earlier machine, the C-36.

Cryptanalysis of the Enigma ciphering system enabled the western Allies in World War II to read substantial amounts of Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military intelligence which, along with that from other decrypted Axis radio and teleprinter transmissions, was given the codename Ultra.

The TSEC/KL-7, also known as Adonis was an off-line non-reciprocal rotor encryption machine. The KL-7 had rotors to encrypt the text, most of which moved in a complex pattern, controlled by notched rings. The non-moving rotor was fourth from the left of the stack. The KL-7 also encrypted the message indicator.
In the history of cryptography, the NEMA (NEue MAschine) ("new machine"), also designated the T-D (Tasten-Druecker-Maschine) ("key-stroke machine"), was a 10-wheel rotor machine designed by the Swiss Army during the World War II as a replacement for their Enigma machines.

In cryptography, Fialka (M-125) is the name of a Cold War-era Soviet cipher machine. A rotor machine, the device uses 10 rotors, each with 30 contacts along with mechanical pins to control stepping. It also makes use of a punched card mechanism. Fialka means "violet" in Russian. Information regarding the machine was quite scarce until c. 2005 because the device had been kept secret.
Banburismus was a cryptanalytic process developed by Alan Turing at Bletchley Park in Britain during the Second World War. It was used by Bletchley Park's Hut 8 to help break German Kriegsmarine (naval) messages enciphered on Enigma machines. The process used sequential conditional probability to infer information about the likely settings of the Enigma machine. It gave rise to Turing's invention of the ban as a measure of the weight of evidence in favour of a hypothesis. This concept was later applied in Turingery and all the other methods used for breaking the Lorenz cipher.
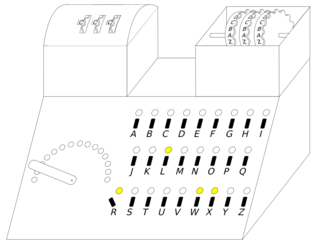
The cyclometer was a cryptologic device designed, "probably in 1934 or 1935," by Marian Rejewski of the Polish Cipher Bureau's German section (BS-4), to catalog the cycle structure of Enigma permutations, thereby facilitating the decryption of German Enigma ciphertext.
In cryptography, the clock was a method devised by Polish mathematician-cryptologist Jerzy Różycki, at the Polish General Staff's Cipher Bureau, to facilitate decrypting German Enigma ciphers. The method determined the rightmost rotor in the German Enigma by exploiting the different turnover positions. For the Poles, learning the rightmost rotor reduced the rotor-order search space by a factor of 3. The British improved the method, and it allowed them to use their limited number of bombes more effectively.
The card catalog, or "catalog of characteristics," in cryptography, was a system designed by Polish Cipher Bureau mathematician-cryptologist Marian Rejewski, and first completed about 1935 or 1936, to facilitate decrypting German Enigma ciphers.
The grill method, in cryptology, was a method used chiefly early on, before the advent of the cyclometer, by the mathematician-cryptologists of the Polish Cipher Bureau in decrypting German Enigma machine ciphers. The Enigma rotor cipher machine changes plaintext characters into cipher text using a different permutation for each character, and so implements a polyalphabetic substitution cipher.
John William Jamieson Herivel was a British science historian and World War II codebreaker at Bletchley Park.

Marian Adam Rejewski was a Polish mathematician and cryptologist who in late 1932 reconstructed the sight-unseen Nazi German military Enigma cipher machine, aided by limited documents obtained by French military intelligence. Over the next nearly seven years, Rejewski and fellow mathematician-cryptologists Jerzy Różycki and Henryk Zygalski developed and used techniques and equipment to decrypt the German machine ciphers, even as the Germans introduced modifications to their equipment and encryption procedures.
The Schlüsselgerät 39 (SG-39) was an electrically operated rotor cipher machine, invented by the German Fritz Menzer during World War II. The device was the evolution of the Enigma rotors coupled with three Hagelin pin wheels to provide variable stepping of the rotors. All three wheels stepped once with each encipherment. Rotors stepped according to normal Enigma rules, except that an active pin at the reading station for a pin wheel prevented the coupled rotor from stepping. The cycle for a normal Enigma was 17,576 characters. When the Schlüsselgerät 39 was correctly configured, its cycle length was characters, which was more than 15,000 times longer than a standard Enigma. The Schlüsselgerät 39 was fully automatic, in that when a key was pressed, the plain and cipher letters were printed on separate paper tapes, divided into five-digit groups. The Schlüsselgerät 39 was abandoned by German forces in favour of the Schlüsselgerät 41.



















