The topic of this article may not meet Wikipedia's general notability guideline .(August 2013) |
A fail-silent system is a type of system that either provides the correct service, or provides no service at all (becomes silent). [1]
The topic of this article may not meet Wikipedia's general notability guideline .(August 2013) |
A fail-silent system is a type of system that either provides the correct service, or provides no service at all (becomes silent). [1]

In computing, BIOS is firmware used to provide runtime services for operating systems and programs and to perform hardware initialization during the booting process. The BIOS firmware comes pre-installed on an IBM PC or IBM PC compatible's system board and exists in some UEFI-based systems to maintain compatibility with operating systems that do not support UEFI native operation. The name originates from the Basic Input/Output System used in the CP/M operating system in 1975. The BIOS originally proprietary to the IBM PC has been reverse engineered by some companies looking to create compatible systems. The interface of that original system serves as a de facto standard.
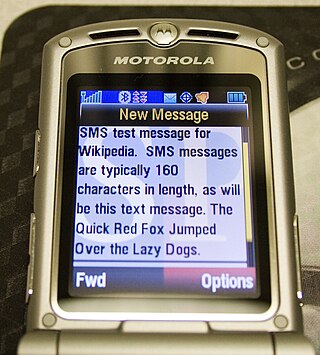
Short Message/Messaging Service, commonly abbreviated as SMS, is a text messaging service component of most telephone, Internet and mobile device systems. It uses standardized communication protocols that let mobile devices exchange short text messages. An intermediary service can facilitate a text-to-voice conversion to be sent to landlines.

A safety-critical system or life-critical system is a system whose failure or malfunction may result in one of the following outcomes:
Installation of a computer program, is the act of making the program ready for execution. Installation refers to the particular configuration of software or hardware with a view to making it usable with the computer. A soft or digital copy of the piece of software (program) is needed to install it. There are different processes of installing a piece of software (program). Because the process varies for each program and each computer, programs often come with an installer, a specialised program responsible for doing whatever is needed for the installation. Installation may be part of a larger software deployment process.
A Byzantine fault is a condition of a computer system, particularly distributed computing systems, where components may fail and there is imperfect information on whether a component has failed. The term takes its name from an allegory, the "Byzantine generals problem", developed to describe a situation in which, to avoid catastrophic failure of the system, the system's actors must agree on a concerted strategy, but some of these actors are unreliable.

Data corruption refers to errors in computer data that occur during writing, reading, storage, transmission, or processing, which introduce unintended changes to the original data. Computer, transmission, and storage systems use a number of measures to provide end-to-end data integrity, or lack of errors.
Data scrubbing is an error correction technique that uses a background task to periodically inspect main memory or storage for errors, then corrects detected errors using redundant data in the form of different checksums or copies of data. Data scrubbing reduces the likelihood that single correctable errors will accumulate, leading to reduced risks of uncorrectable errors.

A solid-state drive (SSD) is a solid-state storage device that uses integrated circuit assemblies to store data persistently, typically using flash memory, and functions as secondary storage in the hierarchy of computer storage. It is also sometimes called a semiconductor storage device, a solid-state device, or a solid-state disk, even though SSDs lack the physical spinning disks and movable read-write heads used in hard disk drives (HDDs) and floppy disks. SSD also has rich internal parallelism for data processing.

This comparison of orbital launch systems lists the attributes of all individual rocket configurations designed to reach orbit. A first list contains rockets that are operational or in development as of 2023; a second list includes all upcoming rockets and a third list includes all retired rockets For the simple list of all conventional launcher families, see: Comparison of orbital launchers families. For the list of predominantly solid-fueled orbital launch systems, see: Comparison of solid-fueled orbital launch systems.

SafeNet, Inc. was an information security company based in Belcamp, Maryland, United States, which was acquired in August 2014 by the French security company Gemalto. Gemalto was, in turn, acquired by Thales Group in 2019. The former SafeNet's products include solutions for enterprise authentication, data encryption, and key management. SafeNet's software monetization products are sold under the Thales Sentinel brand.

Cloud computing is the on-demand availability of computer system resources, especially data storage and computing power, without direct active management by the user. Large clouds often have functions distributed over multiple locations, each of which is a data center. Cloud computing relies on sharing of resources to achieve coherence and typically uses a pay-as-you-go model, which can help in reducing capital expenses but may also lead to unexpected operating expenses for users.
Essential Utilities is an American utility company that has stakes in Illinois, Indiana, New Jersey, North Carolina, Ohio, Pennsylvania, Texas and Virginia The company provides drinking water and wastewater treatment infrastructure and services. Essential Utilities is the publicly traded ($WTRG) parent company that oversees the continued business of Aqua America and Peoples Natural Gas, who both continue to do business under their original names.
Special Temporary Authority (STA) 74 CFR 73.1635 in U.S. broadcast law is a type of broadcast license which temporarily allows a broadcast station to operate outside of its normal technical or legal parameters. In the Federal Communications Commission (FCC) station database (CDBS), broadcast STA applications have a prefix of BSTA (general), BLSTA (legal), BESTA (engineering), or BLESTA (both). STAs can also be issued for other telecommunication services under FCC regulation. Often an STA is necessary due to an unforeseen event. A station operator must exhibit why the STA is necessary and serves the public good.
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet.

An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software interface, offering a service to other pieces of software. A document or standard that describes how to build or use such a connection or interface is called an API specification. A computer system that meets this standard is said to implement or expose an API. The term API may refer either to the specification or to the implementation. Whereas a system's user interface dictates how its end-users interact with the system in question, its API dictates how to write code that takes advantage of that system's capabilities.

Cameron International Corporation (formerly Cooper Cameron Corporation (CCC) and Cooper Oil Tool, Cameron Iron Works) though now operating under Schlumberger, is a global provider of pressure control, production, processing, and flow control systems as well as project management and aftermarket services for the oil and gas and process industries. Cameron was acquired by Schlumberger (SLB) in 2016, and now operates as 'Cameron, an SLB Company.' At the start of the SLB acquisition in 2015, Cameron employed approximately 23,000 people and delivered $9.8 billion in revenue.
Police brutality is the abuse of authority by the unwarranted infliction of excessive force by personnel involved in law enforcement while performing their official duties. Police brutality can also include psychological harm through the use of intimidation tactics beyond the scope of officially sanctioned police procedure. In the United States, Native Americans experience disproportionately high amounts of violence from law enforcement.

GSAT-6A was a communication satellite launched by the Indian Space Research Organisation (ISRO) It featured a 6-metre (20 ft) unfurlable S-band antenna similar to the one used on GSAT-6. Around 17 minutes after lift-off, the three stage GSLV Mk.II rocket flying on GSLV F08 mission successfully injected the satellite into a geosynchronous transfer orbit. Due to power failure during its orbit raising burns the communication was lost with GSAT-6A before it could reach its final circular geostationary orbit (GSO).

The Shallow Water Combat Submersible (SWCS) is a crewed submersible and a type of swimmer delivery vehicle that is planned to be used to deliver United States Navy SEALs and their equipment for special operations missions. It will replace the current Mark 8 SEAL Delivery Vehicle. The Navy planned to introduce the SWCS in 2018, although "slippage in the development" has delayed its introduction until 2019. In 2020, the U.S. Navy stated that it was undergoing sea trials and testing. As of October 2018, two subs have been delivered to the Navy while another two were in production. The SWCS will serve alongside the Dry Combat Submersible (DCS), a midget submarine with a dry interior being developed by Lockheed Martin as a replacement for the cancelled Advanced SEAL Delivery System (ASDS).
MICA was the codename of the operating system developed for the DEC PRISM architecture. MICA was designed by a team at Digital Equipment Corporation led by Dave Cutler. MICA's design was driven by Digital's need to provide a migration path to PRISM for Digital's VAX/VMS customers, as well as allowing PRISM systems to compete in the increasingly important Unix market. MICA attempted to address these requirements by implementing VMS and ULTRIX user interfaces on top of a common kernel that could support the system calls, libraries and utilities needed for both environments.