Related Research Articles

The United States Foreign Intelligence Surveillance Court is a U.S. federal court established under the Foreign Intelligence Surveillance Act of 1978 (FISA) to oversee requests for surveillance warrants against foreign spies inside the United States by federal law enforcement and intelligence agencies. Such requests are made most often by the National Security Agency (NSA) and the Federal Bureau of Investigation (FBI). Congress created FISA and its court as a result of the recommendations by the U.S. Senate's Church Committee.

The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The existence of the NSA was not revealed until 1975. The NSA has roughly 32,000 employees.
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored.
Surveillance abuse is the use of surveillance methods or technology to monitor the activity of an individual or group of individuals in a way which violates the social norms or laws of a society.

James Bamford is an American author, journalist and documentary producer noted for his writing about United States intelligence agencies, especially the National Security Agency (NSA). The New York Times has called him "the nation's premier journalist on the subject of the National Security Agency" and The New Yorker named him "the NSA's chief chronicler." Bamford has taught at the University of California, Berkeley as a distinguished visiting professor and has written for The New York Times Magazine, The Atlantic, Harper's, and many other publications. In 2006, he won the National Magazine Award for Reporting for his writing on the war in Iraq published in Rolling Stone. He is also an Emmy nominated documentary producer for PBS and spent a decade as the Washington investigative producer for ABC's World News Tonight. In 2015 he became the national security columnist for Foreign Policy magazine and he also writes for The New Republic. His most recent book, The Shadow Factory: The Ultra-Secret NSA From 9/11 to the Eavesdropping on America, became a New York Times bestseller and was named by The Washington Post as one of "The Best Books of the Year." It is the third in a trilogy by Bamford on the NSA, following The Puzzle Palace (1982) and Body of Secrets (2001), also New York Times bestsellers.

NSA warrantless surveillance — also commonly referred to as "warrantless-wiretapping" or "-wiretaps" — refers to the surveillance of persons within the United States, including U.S. citizens, during the collection of notionally foreign intelligence by the National Security Agency (NSA) as part of the Terrorist Surveillance Program. In late 2001, the NSA was authorized to monitor, without obtaining a FISA warrant, the phone calls, Internet activity, text messages and other communication involving any party believed by the NSA to be outside the U.S., even if the other end of the communication lay within the U.S.

Russell D. Tice is a former intelligence analyst for the United States Air Force, Office of Naval Intelligence, Defense Intelligence Agency (DIA), and National Security Agency (NSA).

The Five Eyes (FVEY) is an intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States. These countries are parties to the multilateral UKUSA Agreement, a treaty for joint cooperation in signals intelligence.
The Privacy and Civil Liberties Oversight Board (PCLOB) is an independent agency within the executive branch of the United States government, established by Congress in 2004 to advise the President and other senior executive branch officials to ensure that concerns with respect to privacy and civil liberties in the United States are appropriately considered in the development and implementation of all laws, regulations, and executive branch policies related to terrorism.

MAINWAY is a database maintained by the United States' National Security Agency (NSA) containing metadata for hundreds of billions of telephone calls made through the four largest telephone carriers in the United States: AT&T, SBC, BellSouth and Verizon.

James Robert Clapper Jr. is a retired lieutenant general in the United States Air Force and former Director of National Intelligence. Clapper has held several key positions within the United States Intelligence Community. He served as director of the Defense Intelligence Agency (DIA) from 1992 until 1995. He was the first director of defense intelligence within the Office of the Director of National Intelligence and simultaneously the Under Secretary of Defense for Intelligence. He served as the director of the National Geospatial-Intelligence Agency (NGA) from September 2001 until June 2006.

PRISM is a code name for a program under which the United States National Security Agency (NSA) collects internet communications from various U.S. internet companies. The program is also known by the SIGAD US-984XN. PRISM collects stored internet communications based on demands made to internet companies such as Google LLC under Section 702 of the FISA Amendments Act of 2008 to turn over any data that match court-approved search terms. Among other things, the NSA can use these PRISM requests to target communications that were encrypted when they traveled across the internet backbone, to focus on stored data that telecommunication filtering systems discarded earlier, and to get data that is easier to handle.

Edward Joseph Snowden is an American former computer intelligence consultant who leaked highly classified information from the National Security Agency (NSA) in 2013, when he was an employee and subcontractor. His disclosures revealed numerous global surveillance programs, many run by the NSA and the Five Eyes Intelligence Alliance with the cooperation of telecommunication companies and European governments, and prompted a cultural discussion about national security and individual privacy.

The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveillance continued throughout the Cold War period, via programs such as the Black Chamber and Project SHAMROCK. The formation and growth of federal law-enforcement and intelligence agencies such as the FBI, CIA, and NSA institutionalized surveillance used to also silence political dissent, as evidenced by COINTELPRO projects which targeted various organizations and individuals. During the Civil Rights Movement era, many individuals put under surveillance orders were first labelled as integrationists, then deemed subversive, and sometimes suspected to be supportive of the communist model of the United States' rival at the time, the Soviet Union. Other targeted individuals and groups included Native American activists, African American and Chicano liberation movement activists, and anti-war protesters.

Ongoing news reports in the international media have revealed operational details about the Anglophone cryptographic agencies' global surveillance of both foreign and domestic nationals. The reports mostly emanate from a cache of top secret documents leaked by ex-NSA contractor Edward Snowden, which he obtained whilst working for Booz Allen Hamilton, one of the largest contractors for defense and intelligence in the United States. In addition to a trove of U.S. federal documents, Snowden's cache reportedly contains thousands of Australian, British, Canadian and New Zealand intelligence files that he had accessed via the exclusive "Five Eyes" network. In June 2013, the first of Snowden's documents were published simultaneously by The Washington Post and The Guardian, attracting considerable public attention. The disclosure continued throughout 2013, and a small portion of the estimated full cache of documents was later published by other media outlets worldwide, most notably The New York Times, the Canadian Broadcasting Corporation, the Australian Broadcasting Corporation, Der Spiegel (Germany), O Globo (Brazil), Le Monde (France), L'espresso (Italy), NRC Handelsblad, Dagbladet (Norway), El País (Spain), and Sveriges Television (Sweden).

The global surveillance disclosure released to media by Edward Snowden has caused tension in the bilateral relations of the United States with several of its allies and economic partners as well as in its relationship with the European Union. In August 2013, U.S. President Barack Obama announced the creation of "a review group on intelligence and communications technologies" that would brief and later report to him. In December, the task force issued 46 recommendations that, if adopted, would subject the National Security Agency (NSA) to additional scrutiny by the courts, Congress, and the president, and would strip the NSA of the authority to infiltrate American computer systems using "backdoors" in hardware or software. Geoffrey R. Stone, a White House panel member, said there was no evidence that the bulk collection of phone data had stopped any terror attacks.

Global mass surveillance can be defined as the mass surveillance of entire populations across national borders.
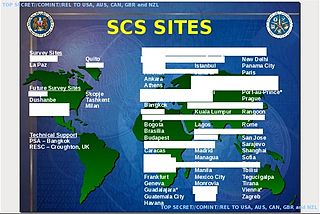
STATEROOM is the code name of a highly secretive signals intelligence collection program involving the interception of international radio, telecommunications and internet traffic. It is operated out of the diplomatic missions of the signatories to the UKUSA Agreement and the members of the ECHELON network including Australia, New Zealand, United Kingdom, Canada and the United States.

The FISA Improvements Act is a proposed act by Senator Dianne Feinstein, Chair of the Senate Intelligence Committee. Prompted by the disclosure of NSA surveillance by Edward Snowden, it would establish the surveillance program as legal, but impose some limitations on availability of the data. Opponents say the bill would codify warrantless access to many communications of American citizens for use by domestic law enforcement.

Proposed reforms of mass surveillance by the United States are a collection of diverse proposals offered in response to the Global surveillance disclosures of 2013.
References
- 1 2 Edward Moyer (2013-09-27). "NSA offers details on 'LOVEINT' (that's spying on lovers, exes)". CNET. Archived from the original on 2014-02-01. Retrieved 2014-03-23.
- ↑ Siobhan Gorman (2013-08-23). "NSA Officers Spy on Love Interests". Washington Wire. The Wall Street Journal. Archived from the original on 2014-04-01. Retrieved 2014-03-23.
- ↑ Andrea Peterson (2013-08-24). "LOVEINT: When NSA officers use their spying power on love interests". The Washington Post. Archived from the original on 2014-03-28. Retrieved 2014-03-23.
- ↑ Lee Ferran (2013-09-27). "'LoveINT': Given Immense Powers, NSA Employees Super Cyber-Stalked Their Crushes". American Broadcasting Company. Archived from the original on 2014-03-24. Retrieved 2014-03-23.
- ↑ National Broadcasting Company (2013-09-27). "'Loveint': NSA letter discloses employee eavesdropping on girlfriends, spouses". National Broadcasting Company. Archived from the original on 2014-03-23. Retrieved 2014-03-23.
- ↑ Ryan Gallagher (2013-09-27). "Loveint: How NSA spies snooped on girlfriends, lovers, and first dates". Future Tense. Slate. Archived from the original on 2014-04-02. Retrieved 2014-03-23.
- ↑ Andreas Förster (2007-08-31). "BKA-REFORM - Das Bundeskriminalamt soll per Gesetz mehr Befugnisse bei der Terrorabwehr bekommen. Neue Fahndungsmethoden sollen die Jagd auf Staatsfeinde erleichtern.: Beamter unter Verdacht". Berliner Zeitung (in German). Archived from the original on 2011-04-29. Retrieved 2014-03-16.