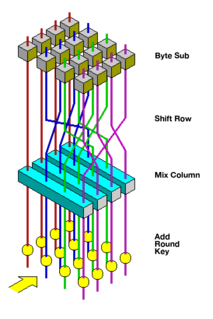
The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
Blowfish is a symmetric-key block cipher, designed in 1993 by Bruce Schneier and included in many cipher suites and encryption products. Blowfish provides a good encryption rate in software, and no effective cryptanalysis of it has been found to date. However, the Advanced Encryption Standard (AES) now receives more attention, and Schneier recommends Twofish for modern applications.

Bruce Schneier is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is a Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Center for Internet & Society as of November, 2013. He is a board member of the Electronic Frontier Foundation, Access Now, and The Tor Project; and an advisory board member of Electronic Privacy Information Center and VerifiedVoting.org. He is the author of several books on general security topics, computer security and cryptography and is a squid enthusiast.
A cypherpunk is any individual advocating widespread use of strong cryptography and privacy-enhancing technologies as a route to social and political change. Originally communicating through the Cypherpunks electronic mailing list, informal groups aimed to achieve privacy and security through proactive use of cryptography. Cypherpunks have been engaged in an active movement since at least the late 1980s.
In computing, a trusted client is a device or program controlled by the user of a service, but with restrictions designed to prevent its use in ways not authorized by the provider of the service. That is, the client is a device that vendors trust and then sell to the consumers, whom they do not trust. Examples include video games played over a computer network or the Content Scramble System (CSS) in DVDs.

The Transparent Society (1998) is a non-fiction book by the science-fiction author David Brin in which he forecasts social transparency and some degree of erosion of privacy, as it is overtaken by low-cost surveillance, communication and database technology, and proposes new institutions and practices that he believes would provide benefits that would more than compensate for lost privacy. The work first appeared as a magazine article by Brin in Wired in late 1996. In 2008, security expert Bruce Schneier called the transparent society concept a "myth", claiming it ignores wide differences in the relative power of those who access information.
The Point-to-Point Tunneling Protocol (PPTP) is an obsolete method for implementing virtual private networks. PPTP has many well known security issues.

David A. Wagner is a professor of computer science at the University of California, Berkeley and a well-known researcher in cryptography and computer security. He is a member of the Election Assistance Commission's Technical Guidelines Development Committee, tasked with assisting the EAC in drafting the Voluntary Voting System Guidelines. He is also a member of the ACCURATE project.

Alice and Bob are fictional characters commonly used as placeholders in discussions about cryptographic systems and protocols, and in other science and engineering literature where there are several participants in a thought experiment. The Alice and Bob characters were invented by Ron Rivest, Adi Shamir, and Leonard Adleman in their 1978 paper "A Method for Obtaining Digital Signatures and Public-key Cryptosystems". Subsequently, they have become common archetypes in many scientific and engineering fields, such as quantum cryptography, game theory and physics. As the use of Alice and Bob became more widespread, additional characters were added, sometimes each with a particular meaning. These characters do not have to refer to people; they refer to generic agents which might be different computers or even different programs running on a single computer.

Malcolm Timothy Gladwell is an English-born Canadian journalist, author, and public speaker. He has been a staff writer for The New Yorker since 1996. He has published seven books: The Tipping Point: How Little Things Can Make a Big Difference (2000); Blink: The Power of Thinking Without Thinking (2005); Outliers: The Story of Success (2008); What the Dog Saw: And Other Adventures (2009), a collection of his journalism; David and Goliath: Underdogs, Misfits, and the Art of Battling Giants (2013); Talking To Strangers: What We Should Know about the People We Don't Know (2019) and The Bomber Mafia: A Dream, a Temptation, and the Longest Night of the Second World War (2021). His first five books were on The New York Times Best Seller list. He is also the host of the podcast Revisionist History and co-founder of the podcast company Pushkin Industries.
End-to-end encryption (E2EE) is a system of communication where only the communicating users can read the messages. In principle, it prevents potential eavesdroppers – including telecom providers, Internet providers, malicious actors, and even the provider of the communication service – from being able to access the cryptographic keys needed to decrypt the conversation.
Security theater is the practice of taking security measures that are considered to provide the feeling of improved security while doing little or nothing to achieve it.

In cryptography, nothing-up-my-sleeve numbers are any numbers which, by their construction, are above suspicion of hidden properties. They are used in creating cryptographic functions such as hashes and ciphers. These algorithms often need randomized constants for mixing or initialization purposes. The cryptographer may wish to pick these values in a way that demonstrates the constants were not selected for a nefarious purpose, for example, to create a backdoor to the algorithm. These fears can be allayed by using numbers created in a way that leaves little room for adjustment. An example would be the use of initial digits from the number π as the constants. Using digits of π millions of places after the decimal point would not be considered trustworthy because the algorithm designer might have selected that starting point because it created a secret weakness the designer could later exploit.

The Rainbow Series is a series of computer security standards and guidelines published by the United States government in the 1980s and 1990s. They were originally published by the U.S. Department of Defense Computer Security Center, and then by the National Computer Security Center.

Password strength is a measure of the effectiveness of a password against guessing or brute-force attacks. In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. The strength of a password is a function of length, complexity, and unpredictability.

On the morning of January 31, 2007, the Boston Police Department and the Boston Fire Department mistakenly identified battery-powered LED placards depicting the Mooninites, characters from the Adult Swim animated television series Aqua Teen Hunger Force, as improvised explosive devices (IEDs), leading to a massive panic. Placed throughout Boston, Massachusetts, and the surrounding cities of Cambridge and Somerville by Peter "Zebbler" Berdovsky and Sean Stevens, these devices were part of a nationwide guerrilla marketing advertising campaign for Aqua Teen Hunger Force Colon Movie Film for Theaters.
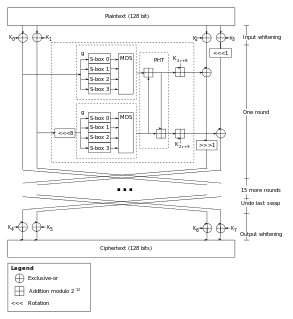
In cryptography, Twofish is a symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists of the Advanced Encryption Standard contest, but it was not selected for standardization. Twofish is related to the earlier block cipher Blowfish.

The nothing to hide argument states that individuals have no reason to fear or oppose surveillance programs, unless they are afraid it will uncover their own illicit activities. An individual using this argument may claim that an average person should not worry about government surveillance, as they would have "nothing to hide".

Bullrun is a clandestine, highly classified program to crack encryption of online communications and data, which is run by the United States National Security Agency (NSA). The British Government Communications Headquarters (GCHQ) has a similar program codenamed Edgehill. According to the Bullrun classification guide published by The Guardian, the program uses multiple methods including computer network exploitation, interdiction, industry relationships, collaboration with other intelligence community entities, and advanced mathematical techniques.

Click Here to Kill Everybody: Security and Survival in a Hyper-connected World is a 2018 nonfiction book by Bruce Schneier that explores the risks and security implications of the proliferation of Internet of Things devices and increases in widespread automation, and lays out suggestions as to how these might be best mitigated at a societal level.














