Related Research Articles
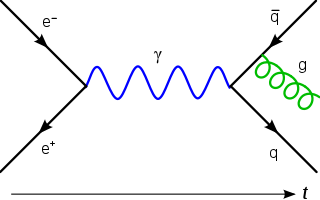
In particle physics, quantum electrodynamics (QED) is the relativistic quantum field theory of electrodynamics. In essence, it describes how light and matter interact and is the first theory where full agreement between quantum mechanics and special relativity is achieved. QED mathematically describes all phenomena involving electrically charged particles interacting by means of exchange of photons and represents the quantum counterpart of classical electromagnetism giving a complete account of matter and light interaction.

Quantum information is the information of the state of a quantum system. It is the basic entity of study in quantum information theory, and can be manipulated using quantum information processing techniques. Quantum information refers to both the technical definition in terms of Von Neumann entropy and the general computational term.
Quantum key distribution (QKD) is a secure communication method that implements a cryptographic protocol involving components of quantum mechanics. It enables two parties to produce a shared random secret key known only to them, which then can be used to encrypt and decrypt messages. The process of quantum key distribution is not to be confused with quantum cryptography, as it is the best-known example of a quantum-cryptographic task.

In physics, a squeezed coherent state is a quantum state that is usually described by two non-commuting observables having continuous spectra of eigenvalues. Examples are position and momentum of a particle, and the (dimension-less) electric field in the amplitude and in the mode of a light wave. The product of the standard deviations of two such operators obeys the uncertainty principle:
HAVAL is a cryptographic hash function. Unlike MD5, but like most modern cryptographic hash functions, HAVAL can produce hashes of different lengths – 128 bits, 160 bits, 192 bits, 224 bits, and 256 bits. HAVAL also allows users to specify the number of rounds to be used to generate the hash. HAVAL was broken in 2004.
Quantum networks form an important element of quantum computing and quantum communication systems. Quantum networks facilitate the transmission of information in the form of quantum bits, also called qubits, between physically separated quantum processors. A quantum processor is a small quantum computer being able to perform quantum logic gates on a certain number of qubits. Quantum networks work in a similar way to classical networks. The main difference is that quantum networking, like quantum computing, is better at solving certain problems, such as modeling quantum systems.
BB84 is a quantum key distribution scheme developed by Charles Bennett and Gilles Brassard in 1984. It is the first quantum cryptography protocol. The protocol is provably secure assuming a perfect implementation, relying on two conditions: (1) the quantum property that information gain is only possible at the expense of disturbing the signal if the two states one is trying to distinguish are not orthogonal ; and (2) the existence of an authenticated public classical channel. It is usually explained as a method of securely communicating a private key from one party to another for use in one-time pad encryption. The proof of BB84 depends on a perfect implementation. Side channel attacks exist, taking advantage of non-quantum sources of information. Since this information is non-quantum, it can be intercepted without measuring or cloning quantum particles.
SARG04 is a 2004 quantum cryptography protocol derived from the first protocol of that kind, BB84.
A quantum money scheme is a quantum cryptographic protocol that creates and verifies banknotes that are resistant to forgery. It is based on the principle that quantum states cannot be perfectly duplicated, making it impossible to forge quantum money by including quantum systems in its design.
Quantum cryptography is the science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum cryptography is quantum key distribution, which offers an information-theoretically secure solution to the key exchange problem. The advantage of quantum cryptography lies in the fact that it allows the completion of various cryptographic tasks that are proven or conjectured to be impossible using only classical communication. For example, it is impossible to copy data encoded in a quantum state. If one attempts to read the encoded data, the quantum state will be changed due to wave function collapse. This could be used to detect eavesdropping in quantum key distribution (QKD).
Within quantum cryptography, the Decoy state quantum key distribution (QKD) protocol is the most widely implemented QKD scheme. Practical QKD systems use multi-photon sources, in contrast to the standard BB84 protocol, making them susceptible to photon number splitting (PNS) attacks. This would significantly limit the secure transmission rate or the maximum channel length in practical QKD systems. In decoy state technique, this fundamental weakness of practical QKD systems is addressed by using multiple intensity levels at the transmitter's source, i.e. qubits are transmitted by Alice using randomly chosen intensity levels, resulting in varying photon number statistics throughout the channel. At the end of the transmission Alice announces publicly which intensity level has been used for the transmission of each qubit. A successful PNS attack requires maintaining the bit error rate (BER) at the receiver's end, which can not be accomplished with multiple photon number statistics. By monitoring BERs associated with each intensity level, the two legitimate parties will be able to detect a PNS attack, with highly increased secure transmission rates or maximum channel lengths, making QKD systems suitable for practical applications.

The three-stage quantum cryptography protocol, also known as Kak's three-stage protocol is a method of data encryption that uses random polarization rotations by both Alice and Bob, the two authenticated parties, that was proposed by Subhash Kak. In principle, this method can be used for continuous, unbreakable encryption of data if single photons are used. It is different from methods of QKD for it can be used for direct encryption of data, although it could also be used for exchanging keys.
Yi Mu (穆怡) is a professor in Faculty of Data Science, City University of Macau, SAR, Macau, China. He obtained his PhD from the Australian National University in 1994. He was a professor of computer science at the University of Wollongong prior to his job as a professor at Fujian Normal University during 2018 and 2020. He has published more than 500 papers in journals and conference proceedings in cryptography, information security, quantum cryptography, and quantum optics. He was Editor-in-Chief of the International Journal of Applied Cryptography
Consider two remote players, connected by a channel, that don't trust each other. The problem of them agreeing on a random bit by exchanging messages over this channel, without relying on any trusted third party, is called the coin flipping problem in cryptography. Quantum coin flipping uses the principles of quantum mechanics to encrypt messages for secure communication. It is a cryptographic primitive which can be used to construct more complex and useful cryptographic protocols, e.g. Quantum Byzantine agreement.
Continuous-variable (CV) quantum information is the area of quantum information science that makes use of physical observables, like the strength of an electromagnetic field, whose numerical values belong to continuous intervals. One primary application is quantum computing. In a sense, continuous-variable quantum computation is "analog", while quantum computation using qubits is "digital." In more technical terms, the former makes use of Hilbert spaces that are infinite-dimensional, while the Hilbert spaces for systems comprising collections of qubits are finite-dimensional. One motivation for studying continuous-variable quantum computation is to understand what resources are necessary to make quantum computers more powerful than classical ones.
In quantum physics, light is in a squeezed state if its electric field strength Ԑ for some phases has a quantum uncertainty smaller than that of a coherent state. The term squeezing thus refers to a reduced quantum uncertainty. To obey Heisenberg's uncertainty relation, a squeezed state must also have phases at which the electric field uncertainty is anti-squeezed, i.e. larger than that of a coherent state. Since 2019, the gravitational-wave observatories LIGO and Virgo employ squeezed laser light, which has significantly increased the rate of observed gravitational-wave events.
In quantum computing, quantum memory is the quantum-mechanical version of ordinary computer memory. Whereas ordinary memory stores information as binary states, quantum memory stores a quantum state for later retrieval. These states hold useful computational information known as qubits. Unlike the classical memory of everyday computers, the states stored in quantum memory can be in a quantum superposition, giving much more practical flexibility in quantum algorithms than classical information storage.

The DARPA Quantum Network (2002–2007) was the world's first quantum key distribution (QKD) network, operating 10 optical nodes across Boston and Cambridge, Massachusetts. It became fully operational on October 23, 2003 in BBN's laboratories, and in June 2004 was fielded through dark fiber under the streets of Cambridge and Boston, where it ran continuously for over 3 years. The project also created and fielded the world's first superconducting nanowire single-photon detector. It was sponsored by DARPA as part of the QuIST program, and built and operated by BBN Technologies in close collaboration with colleagues at Harvard University and the Boston University Photonics Center.
Quantum secret sharing (QSS) is a quantum cryptographic scheme for secure communication that extends beyond simple quantum key distribution. It modifies the classical secret sharing (CSS) scheme by using quantum information and the no-cloning theorem to attain the ultimate security for communications.
References
- ↑ Mu, Yi; Seberry, Jennifer; Zheng, Yuliang (15 January 1996). "Shared cryptographic bits via quantized quadrature phase amplitudes of light" (PDF). Optics Communications. 123 (1–3): 344–352. Bibcode:1996OptCo.123..344M. CiteSeerX 10.1.1.55.4631 . doi:10.1016/0030-4018(95)00688-5.