In aspect-oriented programming, a pointcut is a set of join points. Pointcut specifies where exactly to apply advice, which allows separation of concerns and helps in modularizing business logic. Pointcuts are often specified using class names or method names, in some cases using regular expressions that match class or method name. Different frameworks support different Pointcut expressions; AspectJ syntax is considered as de facto standard. Frameworks are available for various programming languages like Java, Perl, Ruby, and many more which support pointcut.
RSA SecurID, formerly referred to as SecurID, is a mechanism developed by RSA for performing two-factor authentication for a user to a network resource.

Privilege escalation is the act of exploiting a bug, a design flaw, or a configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user. The result is that an application with more privileges than intended by the application developer or system administrator can perform unauthorized actions.
In computer security, a sandbox is a security mechanism for separating running programs, usually in an effort to mitigate system failures and/or software vulnerabilities from spreading. The isolation metaphor is taken from the idea of children who do not play well together, so each is given their own sandbox to play in alone. It is often used to execute untested or untrusted programs or code, possibly from unverified or untrusted third parties, suppliers, users or websites, without risking harm to the host machine or operating system. A sandbox typically provides a tightly controlled set of resources for guest programs to run in, such as storage and memory scratch space. Network access, the ability to inspect the host system, or read from input devices are usually disallowed or heavily restricted.
Safe mode is a diagnostic mode of a computer operating system (OS). It can also refer to a mode of operation by application software. Safe mode is intended to help fix most, if not all, problems within an operating system. It is also widely used for removing rogue security software.
In the field of computer network administration, pcap is an application programming interface (API) for capturing network traffic. While the name is an abbreviation of packet capture, that is not the API's proper name. Unix-like systems implement pcap in the libpcap library; for Windows, there is a port of libpcap named WinPcap that is no longer supported or developed, and a port named Npcap for Windows 7 and later that is still supported.
A software token is a piece of a two-factor authentication security device that may be used to authorize the use of computer services. Software tokens are stored on a general-purpose electronic device such as a desktop computer, laptop, PDA, or mobile phone and can be duplicated.
A password manager is a computer program that allows users to store and manage their passwords for local applications and online services like a web applications, online shops or social media. Password managers usually simplify authentication by reducing interaction from many steps like “recall-enter-submit” to one step “submit”.
A Google Account is a user account that is required for access, authentication and authorization to certain online Google services. It is also often used as single sign on for third party services.
Disk encryption is a technology which protects information by converting it into code that cannot be deciphered easily by unauthorized people or processes. Disk encryption uses disk encryption software or hardware to encrypt every bit of data that goes on a disk or disk volume. It is used to prevent unauthorized access to data storage.

Eye-Fi was a company based in Mountain View, California, that produced SD memory cards with Wi-Fi capabilities. Using an Eye-Fi card inside a digital camera, one could wirelessly and automatically upload digital photos to a local computer or a mobile device such as a smartphone or tablet computer. The company ceased business in 2016.
Toybox is a free and open-source software implementation of over 200 Unix command line utilities such as ls, cp, and mv. The Toybox project was started in 2006, and became a 0BSD licensed BusyBox alternative. Toybox is used for most of Android's command line tools in all currently supported Android versions, and is also used to build Android on Linux and macOS. All of the tools are tested on Linux, and many of them also work on BSD and macOS.
On Apple devices running iOS and iOS-based operating systems, jailbreaking is the use of a privilege escalation exploit to remove software restrictions imposed by the manufacturer. Typically it is done through a series of kernel patches. A jailbroken device permits root access within the operating system and provides the right to install software unavailable through the App Store. Different devices and versions are exploited with a variety of tools. Apple views jailbreaking as a violation of the end-user license agreement and strongly cautions device owners not to try to achieve root access through the exploitation of vulnerabilities.

Cydia is a graphical user interface of APT for iOS. It enables a user to find and install software not authorized by Apple on jailbroken iPhones, iPads and iPod Touch devices. It also refers to digital distribution platform for software on iOS accessed through Cydia software. Most of the software packages available through Cydia are free of charge, although some require purchasing.

Multi-factor authentication is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence to an authentication mechanism: knowledge, possession, and inherence. MFA protects user data—which may include personal identification or financial assets—from being accessed by an unauthorized third party that may have been able to discover, for example, a single password.

Jay Ryan Freeman is an American businessman and software engineer. He is known for creating the Cydia software application and related software for jailbroken iOS—a modified version of Apple's iOS that allows for the installation and customization of software outside of the regulation imposed by the App Store system.
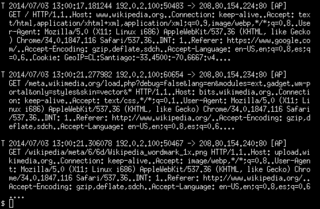
ngrep is a network packet analyzer written by Jordan Ritter. It has a command-line interface, and relies upon the pcap library and the GNU regex library.
Sideloading describes the process of transferring files between two local devices, in particular between a personal computer and a mobile device such as a mobile phone, smartphone, PDA, tablet, portable media player or e-reader.
Google Authenticator is a software-based authenticator by Google that implements two-step verification services using the Time-based One-time Password Algorithm and HMAC-based One-time Password algorithm, for authenticating users of software applications.
Browser security is the application of Internet security to web browsers in order to protect networked data and computer systems from breaches of privacy or malware. Security exploits of browsers often use JavaScript, sometimes with cross-site scripting (XSS) with a secondary payload using Adobe Flash. Security exploits can also take advantage of vulnerabilities that are commonly exploited in all browsers.





