
An email client, email reader or, more formally, message user agent (MUA) or mail user agent is a computer program used to access and manage a user's email.

In computer networking, a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource. It improves privacy, security, and performance in the process.
Virtual private network (VPN) is a network architecture for virtually extending a private network across one or multiple other networks which are either untrusted or need to be isolated.
In computer security, a DMZ or demilitarized zone is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted, usually larger, network such as the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN): an external network node can access only what is exposed in the DMZ, while the rest of the organization's network is protected behind a firewall. The DMZ functions as a small, isolated network positioned between the Internet and the private network.
Remote Authentication Dial-In User Service (RADIUS) is a networking protocol that provides centralized authentication, authorization, and accounting (AAA) management for users who connect and use a network service. RADIUS was developed by Livingston Enterprises in 1991 as an access server authentication and accounting protocol. It was later brought into IEEE 802 and IETF standards.
aMule is a free peer-to-peer file sharing utility that works with the eDonkey network and the Kad network, offering similar features to eMule and adding others such as GeoIP. On August 18, 2003 it was forked from the xMule source code, which itself is a fork of the lMule project, which was the first attempt to bring the eMule client to Linux. These projects were discontinued and aMule is the resulting project, though aMule has less and less resemblance to the client that sired it.

A shell account is a user account on a remote server, typically running under Unix or Linux operating systems. The account gives access to a text-based command-line interface in a shell, via a terminal emulator. The user typically communicates with the server via the SSH protocol. In the early days of the Internet, one would connect using a modem.

In computer networking, port forwarding or port mapping is an application of network address translation (NAT) that redirects a communication request from one address and port number combination to another while the packets are traversing a network gateway, such as a router or firewall. This technique is most commonly used to make services on a host residing on a protected or masqueraded (internal) network available to hosts on the opposite side of the gateway, by remapping the destination IP address and port number of the communication to an internal host.
In computer networks, a tunneling protocol is a communication protocol which allows for the movement of data from one network to another. It can, for example, allow private network communications to be sent across a public network, or for one network protocol to be carried over an incompatible network, through a process called encapsulation.
The Internet Server Application Programming Interface (ISAPI) is an n-tier API of Internet Information Services (IIS), Microsoft's collection of Windows-based web server services. The most prominent application of IIS and ISAPI is Microsoft's web server.
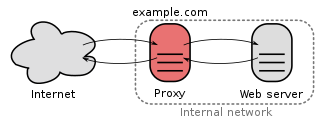
In computer networks, a reverse proxy or surrogate server is a proxy server that appears to any client to be an ordinary web server, but in reality merely acts as an intermediary that forwards the client's requests to one or more ordinary web servers. Reverse proxies help increase scalability, performance, resilience, and security, but they also carry a number of risks.
Bandwidth throttling consists in the limitation of the communication speed, of the ingoing (received) or outgoing (sent) data in a network node or in a network device such as computers and mobile phones.
Split tunneling is a computer networking concept which allows a user to access dissimilar security domains like a public network and a local area network or wide area network at the same time, using the same or different network connections. This connection state is usually facilitated through the simultaneous use of a LAN network interface controller (NIC), radio NIC, Wireless LAN (WLAN) NIC, and VPN client software application without the benefit of an access control.
An anonymizer or an anonymous proxy is a tool that attempts to make activity on the Internet untraceable. It is a proxy server computer that acts as an intermediary and privacy shield between a client computer and the rest of the Internet. It accesses the Internet on the user's behalf, protecting personal information of the user by hiding the client computer's identifying information such as IP addresses. Anonymous proxy is the opposite of transparent proxy, which sends user information in the connection request header. Commercial anonymous proxies are usually sold as VPN services.

Tor is a free overlay network for enabling anonymous communication. Built on free and open-source software and more than seven thousand volunteer-operated relays worldwide, users can have their Internet traffic routed via a random path through the network.
DirectAccess, also known as Unified Remote Access, is a VPN technology that provides intranet connectivity to client computers when they are connected to the Internet. Unlike many traditional VPN connections, which must be initiated and terminated by explicit user action, DirectAccess connections are designed to connect automatically as soon as the computer connects to the Internet. DirectAccess was introduced in Windows Server 2008 R2, providing this service to Windows 7 and Windows 8 "Enterprise" edition clients. In 2010, Microsoft Forefront Unified Access Gateway (UAG) was released, which simplifies the deployment of DirectAccess for Windows 2008 R2, and includes additional components that make it easier to integrate without the need to deploy IPv6 on the network, and with a dedicated user interface for the configuration and monitoring. Some requirements and limitations that were part of the design of DirectAccess with Windows Server 2008 R2 and UAG have been changed. While DirectAccess is based on Microsoft technology, third-party solutions exist for accessing internal UNIX and Linux servers through DirectAccess. With Windows Server 2012, DirectAccess is fully integrated into the operating system, providing a user interface to configure and native IPv6 and IPv4 support.
Internet censorship circumvention, also referred to as going over the wall or scientific browsing in China, is the use of various methods and tools to bypass internet censorship.
Hotspot Shield is a public VPN service operated by AnchorFree, Inc. Hotspot Shield was used to bypass government censorship during the Arab Spring protests in Egypt, Tunisia, and Libya.
A virtual private network (VPN) service provides a proxy server to help users bypass Internet censorship such as geo-blocking and users who want to protect their communications against data profiling or MitM attacks on hostile networks.






