This article needs additional citations for verification .(July 2020) |
In distributed computing, SECIOP (SECure Inter-ORB Protocol) is a protocol for secure inter-ORB communication. [1]
This article needs additional citations for verification .(July 2020) |
In distributed computing, SECIOP (SECure Inter-ORB Protocol) is a protocol for secure inter-ORB communication. [1]
The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution.
The Common Object Request Broker Architecture (CORBA) is a standard defined by the Object Management Group (OMG) designed to facilitate the communication of systems that are deployed on diverse platforms. CORBA enables collaboration between systems on different operating systems, programming languages, and computing hardware. CORBA uses an object-oriented model although the systems that use the CORBA do not have to be object-oriented. CORBA is an example of the distributed object paradigm.
The Java Transaction Service (JTS) is a specification for building a transaction manager that maps onto the Object Management Group (OMG) Object Transaction Service (OTS) used in the Common Object Request Broker Architecture (CORBA) architecture. It uses General Inter-ORB Protocol (IIOP) to propagate the transactions between multiple JTS transaction managers.
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The benefits of a VPN include increases in functionality, security, and management of the private network. It provides access to resources that are inaccessible on the public network and is typically used for telecommuting workers. Encryption is common, although not an inherent part of a VPN connection.
An application layer is an abstraction layer that specifies the shared communications protocols and interface methods used by hosts in a communications network. An application layer abstraction is specified in both the Internet Protocol Suite (TCP/IP) and the OSI model. Although both models use the same term for their respective highest-level layer, the detailed definitions and purposes are different.
Message-oriented middleware (MOM) is software or hardware infrastructure supporting sending and receiving messages between distributed systems. MOM allows application modules to be distributed over heterogeneous platforms and reduces the complexity of developing applications that span multiple operating systems and network protocols. The middleware creates a distributed communications layer that insulates the application developer from the details of the various operating systems and network interfaces. APIs that extend across diverse platforms and networks are typically provided by MOM.
In distributed computing, SSLIOP is an Internet Inter-ORB Protocol (IIOP) over Secure Sockets Layer (SSL), providing confidentiality and authentication.
In distributed computing, General Inter-ORB Protocol (GIOP) is the message protocol by which object request brokers (ORBs) communicate in CORBA. Standards associated with the protocol are maintained by the Object Management Group (OMG). The current version of GIOP is 2.0.2. The GIOP architecture provides several concrete protocols, including:
In distributed computing, CSIv2 is a protocol implementing security features for inter-ORB communication. It intends, in part, to address limitations of SSLIOP.
An Interoperable Object Reference (IOR) is a CORBA or RMI-IIOP reference that uniquely identifies an object on a remote CORBA server.
Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications by allowing them to communicate in a way designed to prevent eavesdropping, tampering, or message forgery. The DTLS protocol is based on the stream-oriented Transport Layer Security (TLS) protocol and is intended to provide similar security guarantees. The DTLS protocol datagram preserves the semantics of the underlying transport—the application does not suffer from the delays associated with stream protocols, but because it uses UDP or SCTP, the application has to deal with packet reordering, loss of datagram and data larger than the size of a datagram network packet. Because DTLS uses UDP or SCTP rather than TCP, it avoids the "TCP meltdown problem", when being used to create a VPN tunnel.
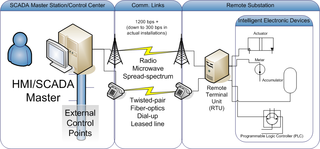
Distributed Network Protocol 3 (DNP3) is a set of communications protocols used between components in process automation systems. Its main use is in utilities such as electric and water companies. Usage in other industries is not common. It was developed for communications between various types of data acquisition and control equipment. It plays a crucial role in SCADA systems, where it is used by SCADA Master Stations, Remote Terminal Units (RTUs), and Intelligent Electronic Devices (IEDs). It is primarily used for communications between a master station and RTUs or IEDs. ICCP, the Inter-Control Center Communications Protocol, is used for inter-master station communications. Competing standards include the older Modbus protocol and the newer IEC 61850 protocol.
RMI-IIOP denotes the Java Remote Method Invocation (RMI) interface over the Internet Inter-Orb Protocol (IIOP), which delivers Common Object Request Broker Architecture (CORBA) distributed computing capabilities to the Java platform. It was initially based on two specifications: the Java Language Mapping to OMG IDL, and CORBA/IIOP 2.3.1.
SAP NetWeaver Process Integration is SAP's enterprise application integration (EAI) software, a component of the NetWeaver product group used to facilitate the exchange of information among a company's internal software and systems and those of external parties. Before the current version, SAP PI was called SAP Exchange Infrastructure . Like other NetWeaver components, SAP PI is compatible with software products of other companies.
Domino Internet Inter-ORB Protocol (DIIOP) is CORBA over IIOP for Lotus Domino. DIIOP allows external programs to attach to, and manipulate Domino databases. DIIOP is frequently used to allow Java-based and other non CORBA programs to connect to Lotus Domino.
In computer network protocol design, inter-server communication is an extension of the client–server model in which data are exchanged directly between servers. In some fields server-to-server (S2S) is used as an alternative, and the term inter-domain can in some cases be used interchangeably.
In software development, Java Interface Definition Language, or Java IDL, is an implementation of the CORBA specification and enables interoperability and connectivity with heterogeneous objects. It is basically an Object Request Broker provided with JDK. The Java IDL enables distributed Web applications to transparently invoke operations on remote network services using the industry standards interface description language (IDL) and Internet InterORB Protocol IIOP from Object Management Group.
GIOP may refer to:
A dynamic circuit network (DCN) is an advanced computer networking technology that combines traditional packet-switched communication based on the Internet Protocol, as used in the Internet, with circuit-switched technologies that are characteristic of traditional telephone network systems. This combination allows user-initiated ad hoc dedicated allocation of network bandwidth for high-demand, real-time applications and network services, delivered over an optical fiber infrastructure.

The InterPlanetary File System (IPFS) is a protocol and peer-to-peer network for storing and sharing data in a distributed file system. IPFS uses content-addressing to uniquely identify each file in a global namespace connecting all computing devices.