
Counterterrorism, also known as anti-terrorism, incorporates the practices, military tactics, techniques, and strategies that governments, law enforcement, businesses, and intelligence agencies use to combat or eliminate terrorism. Counterterrorism strategies are a government's motivation to use the instruments of national power to defeat terrorists, the organizations they maintain, and the networks they contain.

Military intelligence is a military discipline that uses information collection and analysis approaches to provide guidance and direction to assist commanders in their decisions. This aim is achieved by providing an assessment of data from a range of sources, directed towards the commanders' mission requirements or responding to questions as part of operational or campaign planning. To provide an analysis, the commander's information requirements are first identified, which are then incorporated into intelligence collection, analysis, and dissemination.

Counterintelligence is an activity aimed at protecting an agency's intelligence program from an opposition's intelligence service. It includes gathering information and conducting activities to prevent espionage, sabotage, assassinations or other intelligence activities conducted by, for, or on behalf of foreign powers, organizations or persons.
Measurement and signature intelligence (MASINT) is a technical branch of intelligence gathering, which serves to detect, track, identify or describe the distinctive characteristics (signatures) of fixed or dynamic target sources. This often includes radar intelligence, acoustic intelligence, nuclear intelligence, and chemical and biological intelligence. MASINT is defined as scientific and technical intelligence derived from the analysis of data obtained from sensing instruments for the purpose of identifying any distinctive features associated with the source, emitter or sender, to facilitate the latter's measurement and identification.

The United States Intelligence Community (IC) is a group of separate United States government intelligence agencies and subordinate organizations that work both separately and collectively to conduct intelligence activities which support the foreign policy and national security interests of the United States. Member organizations of the IC include intelligence agencies, military intelligence, and civilian intelligence and analysis offices within federal executive departments.
Cyberterrorism is the use of the Internet to conduct violent acts that result in, or threaten, the loss of life or significant bodily harm, in order to achieve political or ideological gains through threat or intimidation. Acts of deliberate, large-scale disruption of computer networks, especially of personal computers attached to the Internet by means of tools such as computer viruses, computer worms, phishing, malicious software, hardware methods, programming scripts can all be forms of internet terrorism. Cyberterrorism is a controversial term. Some authors opt for a very narrow definition, relating to deployment by known terrorist organizations of disruption attacks against information systems for the primary purpose of creating alarm, panic, or physical disruption. Other authors prefer a broader definition, which includes cybercrime. Participating in a cyberattack affects the terror threat perception, even if it isn't done with a violent approach. By some definitions, it might be difficult to distinguish which instances of online activities are cyberterrorism or cybercrime.
In the United States, fusion centers are designed to promote information sharing at the federal level between agencies such as the Federal Bureau of Investigation, the U.S. Department of Homeland Security, the U.S. Department of Justice, and state, local, and tribal law enforcement. As of February 2018, the U.S. Department of Homeland Security recognized 79 fusion centers. Fusion centers may also be affiliated with an emergency operations center that responds in the event of a disaster.
Intelligence analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context. The descriptions are drawn from what may only be available in the form of deliberately deceptive information; the analyst must correlate the similarities among deceptions and extract a common truth. Although its practice is found in its purest form inside national intelligence agencies, its methods are also applicable in fields such as business intelligence or competitive intelligence.

The Central Intelligence Agency, known informally as theAgency and historically as thecompany, is a civilian foreign intelligence service of the federal government of the United States, officially tasked with gathering, processing, and analyzing national security information from around the world, primarily through the use of human intelligence (HUMINT) and conducting covert action. As a principal member of the United States Intelligence Community (IC), the CIA reports to the Director of National Intelligence and is primarily focused on providing intelligence for the President and Cabinet of the United States. Following the dissolution of the Office of Strategic Services (OSS) at the end of World War II, President Harry S. Truman created the Central Intelligence Group under the direction of a Director of Central Intelligence by presidential directive on January 22, 1946, and this group was transformed into the Central Intelligence Agency by implementation of the National Security Act of 1947.

John Owen Brennan is a former American intelligence officer who served as the Director of the Central Intelligence Agency (CIA) from March 2013 to January 2017. He served as chief counterterrorism advisor to U.S. President Barack Obama, with the title Deputy National Security Advisor for Homeland Security and Counterterrorism, and Assistant to the President. Previously, he advised Obama on foreign policy and intelligence issues during the 2008 election campaign and presidential transition.
Intelligence-led policing (ILP) is a policing model built around the assessment and management of risk. Intelligence officers serve as guides to operations, rather than operations guiding intelligence.
Intelligence Analysis Management is the process of managing and organizing the analytical processing of raw intelligence information. The terms "analysis", "production", and "processing" denote the organization and evaluation of raw information used in a phase informally called "connecting the dots", thus creating an "intelligence mosaic". The information may result in multiple analytic products, each with different security classifications, time scales, and levels of detail. Intelligence analysis goes back to the beginning of history. Sherman Kent is often considered the father of modern intelligence analysis. His writings include a 1947 book, Strategic Intelligence for American World Policy.
The counter-terrorism page primarily deals with special police or military organizations that carry out arrest or direct combat with terrorists. This page deals with the other aspects of counter-terrorism:

After the Central Intelligence Agency lost its role as the coordinator of the entire Intelligence Community (IC), special coordinating structures were created by each president to fit his administrative style and the perceived level of threat from terrorists during his term.
Richards "Dick" J. Heuer, Jr. was a CIA veteran of 45 years and most known for his work on analysis of competing hypotheses and his book, Psychology of Intelligence Analysis. The former provides a methodology for overcoming intelligence biases while the latter outlines how mental models and natural biases impede clear thinking and analysis. Throughout his career, he worked in collection operations, counterintelligence, intelligence analysis and personnel security. In 2010 he co-authored a book with Randolph (Randy) H. Pherson titled Structured Analytic Techniques for Intelligence Analysis.
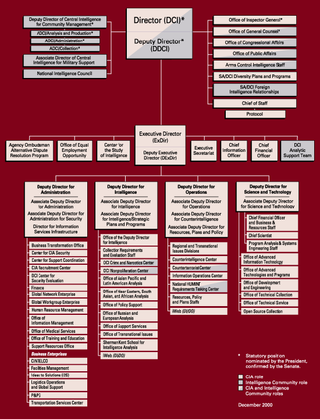
The CIA publishes organizational charts of its agency. Here are a few examples.
Recorded Future is a privately held cybersecurity company founded in 2009, with headquarters in Somerville, Massachusetts.
In computer security, a threat is a potential negative action or event facilitated by a vulnerability that results in an unwanted impact to a computer system or application.

Counter-IED efforts are done primarily by military and law enforcement with the assistance of the diplomatic and financial communities. It involves a comprehensive approach of countering the threat networks that employ improvised explosive devices (IEDs), defeating the devices themselves, and training others. Counter-IED, or C-IED, is usually part of a broader counter-terrorism, counter-insurgency, or law enforcement effort. Because IEDs are a subset of a number of forms of asymmetric warfare used by insurgents and terrorists, C-IED activities are principally against adversaries and not only against IEDs. C-IED treats the IED as a systemic problem and aims to defeat the IED threat networks themselves.
Cyber threat intelligence (CTI) is knowledge, skills and experience-based information concerning the occurrence and assessment of both cyber and physical threats and threat actors that is intended to help mitigate potential attacks and harmful events occurring in cyberspace. Cyber threat intelligence sources include open source intelligence, social media intelligence, human Intelligence, technical intelligence, device log files, forensically acquired data or intelligence from the internet traffic and data derived for the deep and dark web.









