Related Research Articles

In computing, booting is the process of starting a computer as initiated via hardware such as a physical button on the computer or by a software command. After it is switched on, a computer's central processing unit (CPU) has no software in its main memory, so some process must load software into memory before it can be executed. This may be done by hardware or firmware in the CPU, or by a separate processor in the computer system. On some systems a power-on reset (POR) does not initiate booting and the operator must initiate booting after POR completes. IBM uses the term Initial Program Load (IPL) on some product lines.
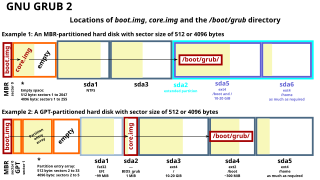
A boot sector is the sector of a persistent data storage device which contains machine code to be loaded into random-access memory (RAM) and then executed by a computer system's built-in firmware.

Multi-booting is the act of installing multiple operating systems on a single computer, and being able to choose which one to boot. The term dual-booting refers to the common configuration of specifically two operating systems. Multi-booting may require a custom boot loader.

A bootloader, also spelled as boot loader or called bootstrap loader, is a computer program that is responsible for booting a computer. If it also provides an interactive menu with multiple boot choices then it's often called a boot manager.

Unified Extensible Firmware Interface is a specification for the firmware architecture of a computing platform. When a computer is powered on, the UEFI-implementation is typically the first that runs, before starting the operating system. Examples include AMI Aptio, Phoenix SecureCore, TianoCore EDK II, InsydeH2O.
Boot ROM is a piece of read-only memory (ROM) that is used for booting a computer system. It contains instructions that are run after the CPU is reset to the reset vector, and it typically loads a bootloader. There are two types of boot ROM: a mask boot ROM that cannot be changed afterwards and a writable boot ROM such as an EEPROM or a flash memory chip.

A brick is a mobile device, game console, router, computer or other electronic device that is no longer functional due to corrupted firmware, a hardware problem, or other damage. The term analogizes the device to a brick's modern technological usefulness. Brick is also used as a verb to describe a device entering such a state.
The Linux booting process involves multiple stages and is in many ways similar to the BSD and other Unix-style boot processes, from which it derives. Although the Linux booting process depends very much on the computer architecture, those architectures share similar stages and software components, including system startup, bootloader execution, loading and startup of a Linux kernel image, and execution of various startup scripts and daemons. Those are grouped into 4 steps: system startup, bootloader stage, kernel stage, and init process.
Rooting is the process by which users of Android devices can attain privileged control over various subsystems of the device, usually smartphones and tablets. Because Android is based on a modified version of the Linux kernel, rooting an Android device gives similar access to administrative (superuser) permissions as on Linux or any other Unix-like operating system such as FreeBSD or macOS.
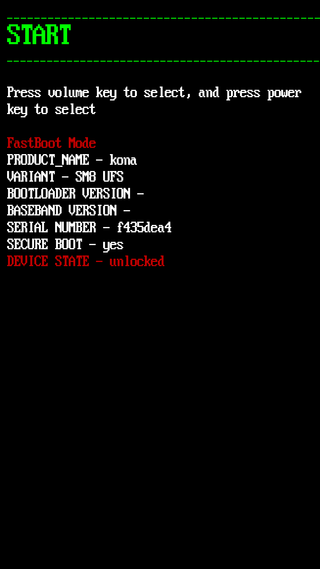
Fastboot is a communication protocol used primarily with Android devices. It is implemented in a command-line interface tool of the same name and as a mode of the bootloader of Android devices. The tool is included with the Android SDK package and used primarily to modify the flash filesystem via a USB connection from a host computer. It requires that the device be started in Fastboot mode. If the mode is enabled, it will accept a specific set of commands, sent through USB bulk transfers. Fastboot on some devices allows unlocking the bootloader, and subsequently, enables installing custom recovery image and custom ROM on the device. Fastboot does not require USB debugging to be enabled on the device. To use fastboot, a specific combination of keys must be held during boot.
The hacking of consumer electronics is a common practice that users perform to customize and modify their devices beyond what is typically possible. This activity has a long history, dating from the days of early computer, programming, and electronics hobbyists.
Samsung Knox is a proprietary security and management framework pre-installed on most Samsung mobile devices. Its primary purpose is to provide organizations with a toolset for managing work devices, such as employee mobile phones or interactive kiosks. Samsung Galaxy hardware, as well as software such as Secure Folder and Samsung Wallet, make use of the Knox framework.

Odin is a utility software program developed and used by Samsung internally which is used to communicate with Samsung devices in Odin mode through the Thor (protocol). It can be used to flash a custom recovery firmware image to a Samsung Android device. Odin is also used for unbricking certain Android devices. Odin is the Samsung proprietary alternative to Fastboot.
Custom firmware, also known as aftermarket firmware, is an unofficial new or modified version of firmware created by third parties on devices such as video game consoles, mobile phones, and various embedded device types to provide new features or to unlock hidden functionality. In the video game console community, the term is often written as custom firmware or simply CFW, referring to an altered version of the original system software inside a video game console such as the PlayStation Portable, PlayStation 3, PlayStation Vita/PlayStation TV, PlayStation 4, Nintendo 3DS, Wii U and Nintendo Switch. Installing custom firmware on some devices requires bootloader unlocking.
IPSW is a file format used to install iOS, iPadOS, tvOS, HomePod, watchOS, and most recently, macOS firmware for devices equipped with Apple silicon. All Apple devices share the same IPSW file format for iOS firmware and their derivatives, allowing users to flash their devices through Finder or iTunes on macOS or Windows, respectively. Users can flash Apple silicon Macs through Apple Configurator 2.
Samsung Experience was the name of the software overlay by Samsung for its Galaxy devices running Android 7.x “Nougat” and Android 8.x “Oreo”. It was introduced in late 2016 on a beta build based on Android 7.0 “Nougat” for the Galaxy S7, succeeding TouchWiz. It has been succeeded in 2018 by One UI based on Android 9 “Pie” and later versions.

Bootloader unlocking is the process of disabling the bootloader security that makes secure boot possible. It can make advanced customizations possible, such as installing custom firmware. On smartphones, this can be a custom Android distribution or another mobile operating system. Some bootloaders are not locked at all and some are locked, but can be unlocked with a command or with assistance from the manufacturer. Some do not include an unlocking method and can only be unlocked through a software exploit.
The Qualcomm Emergency Download mode, commonly known as Qualcomm EDL mode and officially known as Qualcomm HS-USB QD-Loader 9008 is a feature implemented in the boot ROM of a system on a chip by Qualcomm which can be used to recover bricked smartphones. On Google's Pixel 3, the feature was accidentally shown to users after the phone was bricked.

The Android recovery mode is a mode of Android used for installing updates and wipe data. It consists of a Linux kernel with ramdisk on a separate partition from the main Android system.
The booting process of Android devices starts at the power-on of the SoC and ends at the visibility of the home screen, or special modes like recovery and fastboot. The boot process of devices that run Android is influenced by the firmware design of the SoC manufacturers.
References
- ↑ According to u-boot's md/Kconfig the communication protocol is named Thor.
- ↑ "Info about i9100 | LineageOS Wiki".
- ↑ Dumitru, Bogdan. "Boot any Samsung Devices into Download Mode". Odin . Retrieved 2021-09-11.
- ↑ "EMMC hacking, or: How I fixed long-dead Galaxy S3 phones". 10 January 2018.