 | |
| Developer(s) | Cedric Tissieres Philippe Oechslin Objectif Sécurité |
|---|---|
| Stable release | 3.8.0 / March 6, 2018 |
| Repository | |
| Written in | C++, C |
| Operating system | GNU/Linux, Microsoft Windows, macOS |
| Available in | English |
| Type | Password cracking |
| License | GNU General Public License |
| Website | ophcrack |
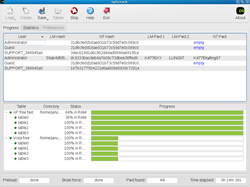
Ophcrack is a free open-source (GPL licensed) program that cracks Windows log-in passwords by using LM hashes through rainbow tables. The program includes the ability to import the hashes from a variety of formats, including dumping directly from the SAM files of Windows, and can be run via the command line or using the program’s GUI (Graphical user interface). On most computers, ophcrack can crack most passwords within a few minutes. [1]
Contents
Rainbow tables for LM hashes are provided for free by the developers. By default, ophcrack is bundled with tables that allow it to crack passwords no longer than 14 characters using only alphanumeric characters. Available for free download are four Windows XP tables and four Windows Vista tables. [2]
Objectif Sécurité has even larger tables that are intended for professional use. [3] Larger rainbow tables are NTLM hash for cracking Windows Vista/Windows 7. [2] In september 2019 these tables have also been made available for free. [4]
Ophcrack is also available as Live CD distributions, which automates the retrieval, decryption, and cracking of passwords from a Windows system. One Live CD distribution is available for Windows XP and lower and another for Windows Vista and Windows 7. [5] The Live CD distributions of ophcrack are built with SliTaz GNU/Linux.
Starting with version 2.3, Ophcrack also cracks NTLM hashes. This is necessary if the generation of the LM hash is disabled (this is default for Windows Vista) or if the password is longer than 14 characters (in which case the LM hash is not stored).
Starting with version 3.7.0, the source code has been moved from SourceForge to GitLab. [6]