Related Research Articles
Blowfish is a symmetric-key block cipher, designed in 1993 by Bruce Schneier and included in many cipher suites and encryption products. Blowfish provides a good encryption rate in software, and no effective cryptanalysis of it has been found to date. However, the Advanced Encryption Standard (AES) now receives more attention, and Schneier recommends Twofish for modern applications.
In cryptography, a block cipher is a deterministic algorithm operating on fixed-length groups of bits, called blocks. They are specified elementary components in the design of many cryptographic protocols and are widely used to the encryption of large amounts of data, including data exchange protocols. It uses blocks as an unvarying transformation.
In cryptography, RC4 is a stream cipher. While it is remarkable for its simplicity and speed in software, multiple vulnerabilities have been discovered in RC4, rendering it insecure. It is especially vulnerable when the beginning of the output keystream is not discarded, or when nonrandom or related keys are used. Particularly problematic uses of RC4 have led to very insecure protocols such as WEP.

A stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as state cipher. In practice, a digit is typically a bit and the combining operation is an exclusive-or (XOR).
ISAAC is a cryptographically secure pseudorandom number generator and a stream cipher designed by Robert J. Jenkins Jr. in 1993. The reference implementation source code was dedicated to the public domain.

Serpent is a symmetric key block cipher that was a finalist in the Advanced Encryption Standard (AES) contest, where it was ranked second to Rijndael. Serpent was designed by Ross Anderson, Eli Biham, and Lars Knudsen.
In cryptography, SAFER is the name of a family of block ciphers designed primarily by James Massey on behalf of Cylink Corporation. The early SAFER K and SAFER SK designs share the same encryption function, but differ in the number of rounds and the key schedule. More recent versions — SAFER+ and SAFER++ — were submitted as candidates to the AES process and the NESSIE project respectively. All of the algorithms in the SAFER family are unpatented and available for unrestricted use.
In cryptography, Khufu and Khafre are two block ciphers designed by Ralph Merkle in 1989 while working at Xerox's Palo Alto Research Center. Along with Snefru, a cryptographic hash function, the ciphers were named after the Egyptian Pharaohs Khufu, Khafre and Sneferu.
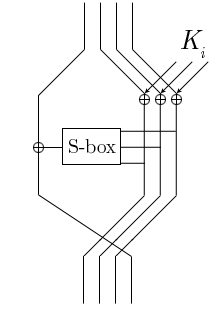
In cryptography, MacGuffin is a block cipher created in 1994 by Bruce Schneier and Matt Blaze at a Fast Software Encryption workshop. It was intended as a catalyst for analysis of a new cipher structure, known as Generalized Unbalanced Feistel Networks (GUFNs). The cryptanalysis proceeded very quickly, so quickly that the cipher was broken at the same workshop by Vincent Rijmen and Bart Preneel.
In cryptography, Madryga is a block cipher published in 1984 by W. E. Madryga. It was designed to be easy and efficient for implementation in software. Serious weaknesses have since been found in the algorithm, but it was one of the first encryption algorithms to make use of data-dependent rotations, later used in other ciphers, such as RC5 and RC6.
HC-256 is a stream cipher designed to provide bulk encryption in software at high speeds while permitting strong confidence in its security. A 128-bit variant was submitted as an eSTREAM cipher candidate and has been selected as one of the four final contestants in the software profile.
In cryptography, Hierocrypt-L1 and Hierocrypt-3 are block ciphers created by Toshiba in 2000. They were submitted to the NESSIE project, but were not selected. Both algorithms were among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003, however, both have been dropped to "candidate" by CRYPTREC revision in 2013.
In cryptography, Zodiac is a block cipher designed in 2000 by Chang-Hyi Lee for the Korean firm SoftForum.
In cryptography, CIPHERUNICORN-E is a block cipher created by NEC in 1998. It was among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003. However, it has been dropped to "candidate" level by the CRYPTREC revision of 2013.
In cryptography, xmx is a block cipher designed in 1997 by David M'Raïhi, David Naccache, Jacques Stern, and Serge Vaudenay. According to the designers it "uses public-key-like operations as confusion and diffusion means." The cipher was designed for efficiency, and the only operations it uses are XORs and modular multiplications.
In cryptography, a distinguishing attack is any form of cryptanalysis on data encrypted by a cipher that allows an attacker to distinguish the encrypted data from random data. Modern symmetric-key ciphers are specifically designed to be immune to such an attack. In other words, modern encryption schemes are pseudorandom permutations and are designed to have ciphertext indistinguishability. If an algorithm is found that can distinguish the output from random faster than a brute force search, then that is considered a break of the cipher.
BLAKE is a cryptographic hash function based on Daniel J. Bernstein's ChaCha stream cipher, but a permuted copy of the input block, XORed with round constants, is added before each ChaCha round. Like SHA-2, there are two variants differing in the word size. ChaCha operates on a 4×4 array of words. BLAKE repeatedly combines an 8-word hash value with 16 message words, truncating the ChaCha result to obtain the next hash value. BLAKE-256 and BLAKE-224 use 32-bit words and produce digest sizes of 256 bits and 224 bits, respectively, while BLAKE-512 and BLAKE-384 use 64-bit words and produce digest sizes of 512 bits and 384 bits, respectively.
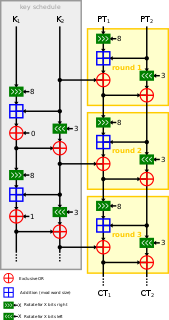
Speck is a family of lightweight block ciphers publicly released by the National Security Agency (NSA) in June 2013. Speck has been optimized for performance in software implementations, while its sister algorithm, Simon, has been optimized for hardware implementations. Speck is an add–rotate–xor (ARX) cipher.

Simon is a family of lightweight block ciphers publicly released by the National Security Agency (NSA) in June 2013. Simon has been optimized for performance in hardware implementations, while its sister algorithm, Speck, has been optimized for software implementations.
In cryptography, security level is a measure of the strength that a cryptographic primitive — such as a cipher or hash function — achieves. Security level is usually expressed in "bits", where n-bit security means that the attacker would have to perform 2n operations to break it, but other methods have been proposed that more closely model the costs for an attacker. This allows for convenient comparison between algorithms and is useful when combining multiple primitives in a hybrid cryptosystem, so there is no clear weakest link. For example, AES-128 is designed to offer a 128-bit security level, which is considered roughly equivalent to a RSA using 3072-bit key.
References
- ↑ M. Boesgaard, M. Vesterager, T. Pedersen, J. Christiansen, O. Scavenius. Rabbit: A High-Performance Stream Cipher. Proc. FSE 2003. Springer LNCS 2887, pp. 307-329 (PDF) Archived 2013-12-11 at the Wayback Machine
- ↑ M. Boesgaard, T. Pedersen, M. Vesterager, E. Zenner. The Rabbit Stream Cipher - Design and Security Analysis. Proc. SASC 2004. (PDF) Archived 2013-12-11 at the Wayback Machine
- ↑ Rabbit becomes public domain by Erik Zenner (October 6, 2008, archived)
- ↑ The eSTREAM Project - eSTREAM Phase 3 "Intellectual Property : Rabbit has been released into the public domain and may be used freely for any purpose. See announcement."
- ↑ Martin Boesgaard; Mette Vesterager; Thomas Christensen; and Erik Zenner. "The Stream Cipher Rabbit". p. 18.
- ↑ Christophe De Cannière, Joseph Lano, and Bart Preneel, "Comments on the Rediscovery of Time Memory Data Tradeoffs", 2005. (PDF)
- ↑ Jean-Philippe Aumasson, "On a bias of Rabbit", Proc. SASC 2007. (PDF)
- ↑ Yi Lu, Huaxiong Wang, San Ling, "Cryptanalysis of Rabbit", Proc. ISC 2008 ()