
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on exploiting the advantages of exponential growth, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer.

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
Cross-site scripting (XSS) is a type of security vulnerability that can be found in some web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy. During the second half of 2007, XSSed documented 11,253 site-specific cross-site vulnerabilities, compared to 2,134 "traditional" vulnerabilities documented by Symantec. XSS effects vary in range from petty nuisance to significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner network.

CIH, also known as Chernobyl or Spacefiller, is a Microsoft Windows 9x computer virus that first emerged in 1998. Its payload is highly destructive to vulnerable systems, overwriting critical information on infected system drives and, in some cases, destroying the system BIOS. The virus was created by Chen Ing-hau, a student at Tatung University in Taiwan. It was believed to have infected sixty million computers internationally, resulting in an estimated NT$1 billion (US$35,801,231.56) in commercial damages.
Linux malware includes viruses, Trojans, worms and other types of malware that affect the Linux family of operating systems. Linux, Unix and other Unix-like computer operating systems are generally regarded as very well-protected against, but not immune to, computer viruses.

Mydoom was a computer worm that targeted computers running Microsoft Windows. It was first sighted on January 26, 2004. It became the fastest-spreading e-mail worm ever, exceeding previous records set by the Sobig worm and ILOVEYOU, a record which as of 2024 has yet to be surpassed.

In computing, SQL injection is a code injection technique used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution. SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.

Myspace is a social networking service based in the United States. Launched on August 1, 2003, it was the first social network to reach a global audience and had a significant influence on technology, pop culture and music. It also played a critical role in the early growth of companies like YouTube and created a developer platform that launched the successes of Zynga, RockYou and Photobucket, among others. From 2005 to 2009, Myspace was the largest social networking site in the world.
ILOVEYOU, sometimes referred to as the Love Bug or Loveletter, was a computer worm that infected over ten million Windows personal computers on and after May 5, 2000. It started spreading as an email message with the subject line "ILOVEYOU" and the attachment "LOVE-LETTER-FOR-YOU.TXT.vbs." At the time, Windows computers often hid the latter file extension by default because it is an extension for a file type that Windows knows, leading unwitting users to think it was a normal text file. Opening the attachment activates the Visual Basic script. First, the worm inflicts damage on the local machine, overwriting random files, then, it copies itself to all addresses in the Windows Address Book used by Microsoft Outlook, allowing it to spread much faster than any other previous email worm.
Christopher Boyd, also known by his online pseudonym Paperghost, is a computer security researcher.

Samy Kamkar is an American privacy and security researcher, computer hacker and entrepreneur. At the age of 16, he dropped out of high school. One year later, he co-founded Fonality, a unified communications company based on open-source software, which raised over $46 million in private funding. In 2005, he created and released the fastest spreading virus of all time, the MySpace worm Samy, and was subsequently raided by the United States Secret Service under the Patriot Act. He also created SkyJack, a custom drone which hacks into any nearby Parrot drones allowing them to be controlled by its operator and created the Evercookie, which appeared in a top-secret NSA document revealed by Edward Snowden and on the front page of The New York Times. He has also worked with The Wall Street Journal, and discovered the illicit mobile phone tracking where the Apple iPhone, Google Android and Microsoft Windows Phone mobile devices transmit GPS and Wi-Fi information to their parent companies. His mobile research led to a series of class-action lawsuits against the companies and a privacy hearing on Capitol Hill. Kamkar has a chapter giving advice in Tim Ferriss' book Tools of Titans.
An XSS worm, sometimes referred to as a cross site scripting virus, is a malicious payload, usually written in JavaScript, that breaches browser security to propagate among visitors of a website in the attempt to progressively infect other visitors. They were first mentioned in 2002 in relation to a cross site scripting vulnerability in Hotmail.

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.

Malvertising is the use of online advertising to spread malware. It typically involves injecting malicious or malware-laden advertisements into legitimate online advertising networks and webpages. Because advertising content can be inserted into high-profile and reputable websites, malvertising provides malefactors an opportunity to push their attacks to web users who might not otherwise see the ads, due to firewalls, more safety precautions, or the like. Malvertising is "attractive to attackers because they 'can be easily spread across a large number of legitimate websites without directly compromising those websites'."

Evercookie is a JavaScript application programming interface (API) that identifies and reproduces intentionally deleted cookies on the clients' browser storage. It was created by Samy Kamkar in 2010 to demonstrate the possible infiltration from the websites that use respawning. Websites that have adopted this mechanism can identify users even if they attempt to delete the previously stored cookies.
Cross-site request forgery, also known as one-click attack or session riding and abbreviated as CSRF or XSRF, is a type of malicious exploit of a website or web application where unauthorized commands are submitted from a user that the web application trusts. There are many ways in which a malicious website can transmit such commands; specially-crafted image tags, hidden forms, and JavaScript fetch or XMLHttpRequests, for example, can all work without the user's interaction or even knowledge. Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user's browser. In a CSRF attack, an innocent end user is tricked by an attacker into submitting a web request that they did not intend. This may cause actions to be performed on the website that can include inadvertent client or server data leakage, change of session state, or manipulation of an end user's account.
The social networking service Myspace was among the most popular web sites in the 2000s decade. It has faced criticism on a variety of fronts, including for a massive redesign of the site in 2012 which occurred after the majority of original users had abandoned the website, misuse of the platform for cyber-bullying and harassment, risks for users' privacy, and major data losses.
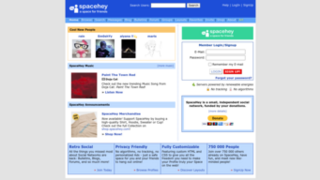
SpaceHey is an English-language online social network operated by the German company tibush GmbH and headquartered in Pfullingen. Founded in 2020 by Anton Röhm, the project serves as a homage to social media platform MySpace during its peak in the mid-2000s. However, it is not officially affiliated with MySpace.










